Lazy security has allowed various groups of hackers, likely including Anonymous, to hijack hundreds of thousands of home and office Internet routers, according to a new report from cybersecurity firm Incapsula.
The hackers target routers that have factory-default usernames and passwords, an “inexplicably negligent” mistake by ISPs and users alike, says Incapsula.
The hijacked routers, located mostly in the U.S., Thailand, and Brazil, were infected by various potent malware and used to build a botnet that began attacks against dozens of targets in late December 2014.
Using the Internet bandwidth from the homes and offices of these routers, the owners of these botnets wield a weapon that packs a heavy punch against online targets.
Botnets (“robot networks”) are armies of hijacked computers used, in this case, to launch denial-of-service attacks against whatever targets—websites, servers, individual devices—that the aggressor aims to overwhelm and take offline.
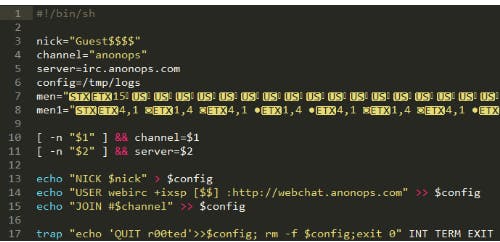
Many of the hijacked machines reported back to AnonOps.com, a gathering point for the Anonymous activist group, “indicating that Anonymous is one of the groups responsible for exploiting these under-protected devices,” the report claims.
The hacking was first discovered by Incapsula last year when dozens of its customers were victims of what researchers describe as a “homogenous botnet” made up of swaths of nearly the same home and office routers.
An investigation revealed that all the hijacked routers suffer from profoundly lax security.
All the “units are remotely accessible via HTTP and SSH on their default ports,” the report reads, meaning they can be accessed easily over the Web. “On top of that, nearly all are configured with vendor-provided default login credentials.”
The botnet is also self-sustaining. Newly hijacked routers will scan for other vulnerable machines; when a good target is found, an automated script easily conscripts it into the botnet’s ranks.
“For perpetrators, this is like shooting fish in a barrel, which makes each of the scans that much more effective,” the report explains. “Using this botnet also enables perpetrators to execute distributed scans, improving their chances against commonplace blacklisting, rate-limiting and reputation-based defense mechanisms.”
The malware infecting the machines includes the popular MrBlack trojan to new and as-yet unidentified pieces of malware.
The new botnet closely resembles the cyberweapon wielded by Lizard Squad, a group of hackers responsible for attacks against Microsoft and Sony in late 2014. It’s not clear if the same individuals are involved or if this new botnet is merely an evolution or copycat of previous work.
You can read the full report below:
Photo via See-ming Lee/Flickr (CC BY 2.0)