The U.S. National Security Agency has hundreds of top-secret surveillance programs operating around the world. They exploit entry points into the data networks of both telecommunication giants and private citizens. Former NSA contractor Edward Snowden began leaking information about the programs in early June to news outlets like the Guardian, Washington Post, Der Spiegel, and the Brazilian paper O Globo. Below is a list of the programs disclosed by Snowden. Click on each one for a detailed explanation of what we know so far:
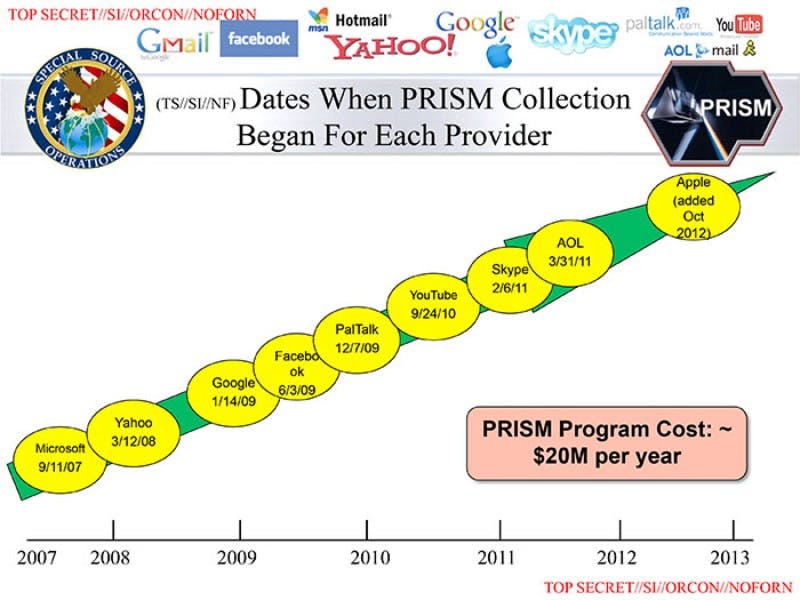
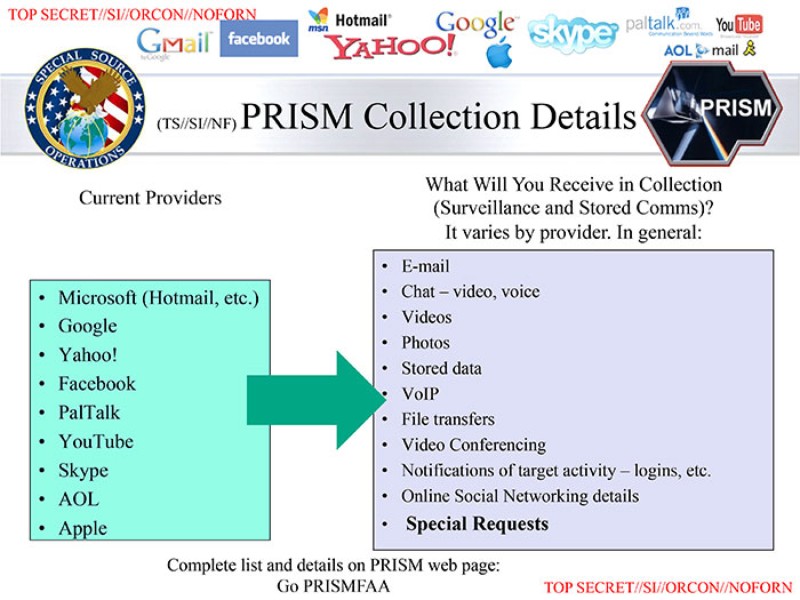
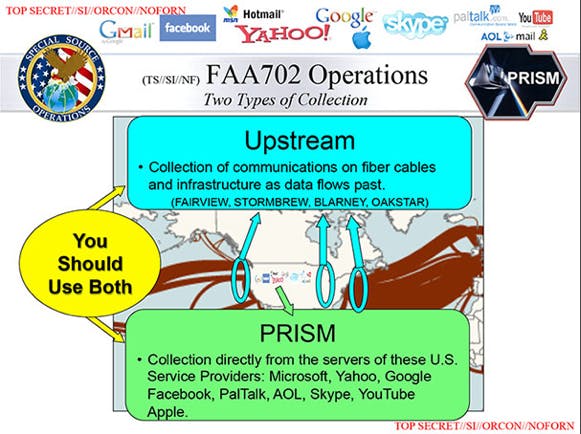
Overview: Perhaps the most infamous (though not the most comprehensive) of the NSA’s programs, PRISM is geared towards collecting the Internet data stored by nine major Silicon Valley technology companies: Facebook, Google, Yahoo, Microsoft, PalTalk, Skype, YouTube, Apple, and AOL.
What data is collected? According to a slide leaked by Snowden to the Guardian and the Washington Post in early June, PRISM collects the following information from customers of the nine aforementioned tech companies: “emails”; “chat–video, voice”; “photos”; “stored data”; “VoIP”; “file transfers”; “video conferencing”; “notifications of target activity–logins, etc”; “online social networking details”; and “special requests.”
How is the data collected? The program operates through a secretive judiciary body called the Foreign Intelligence Surveillance Court. The court, which was created by the Foreign Intelligence Surveillance Act of 1978, provides the agency with warrants for the private information of both foreigners and American citizens in matters of “national security.” The court has been criticized for its readiness to approve the seizure of such information. Since 1978, thousands of applications have been filed in the court. In all that time only 10 have ever been denied.
For the most part, the all-caps names seem not to be acronyms but simply code words. However, there is an entry for PRISM in the “Dictionary of Military and Associated Terms” compiled in 2007 and published by WikiLeaks. In that dictionary, PRISM is said to stand for “Planning Tool for Resource, Integration, Synchronization, and Management.” According to WikiLeaks, the dictionary is used by the Department of Defense (DoD), the parent agency of the NSA.
Overview: In the words of Thomas Drake, a former NSA senior executive who blew the whistle on the agency’s reckless spending and invasive surveillance in 2006, FAIRVIEW is the NSA’s project to “own the Internet.” FAIRVIEW is what Drake called an “umbrella program.” It incorporates many different operations, such as BLARNEY, OAKSTAR, and STORMBREW (discussed below), that intercept massive amounts of international Internet traffic by various means.
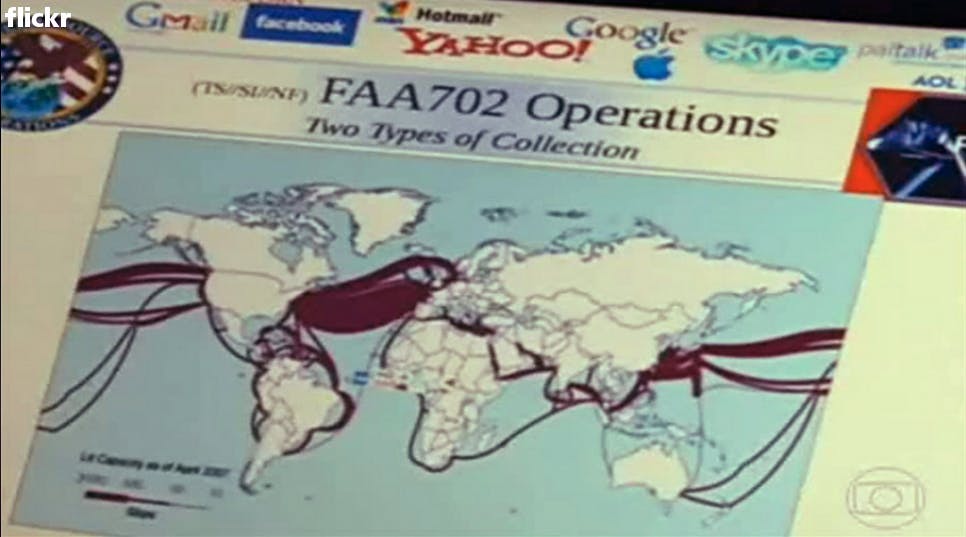
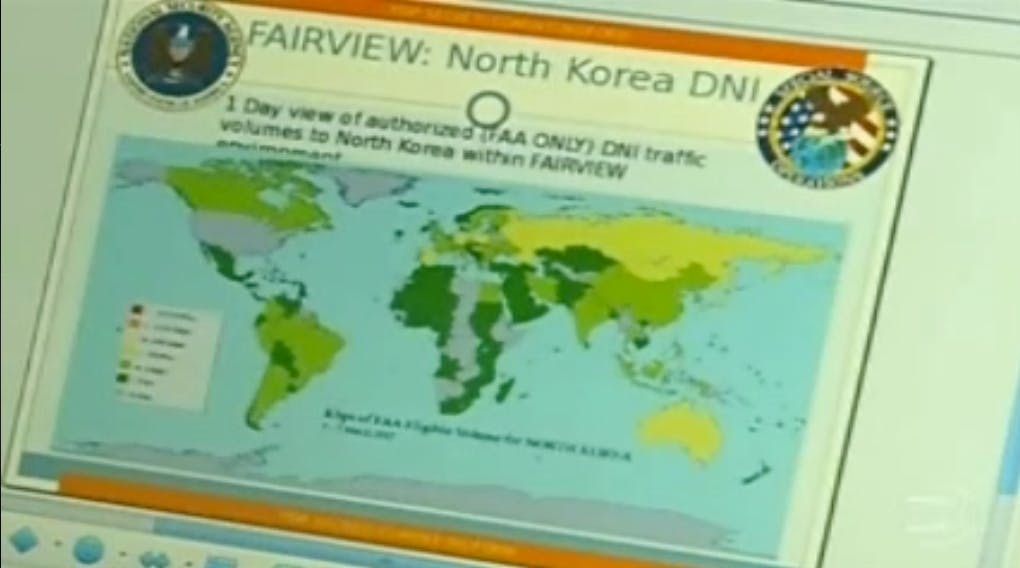
What data is collected? In an email to the Daily Dot, Drake described FAIRVIEW as focused on collecting messages and phone calls at “the main Internet backbone links/junctions of the undersea trunk/cable fiber optic systems.” On a slide released by O Globo (presumably depicting FAIRVIEW’s reach), there is an image of what appears to be North America’s submarine cables.
How is the data collected? Details on FAIRVIEW’s operations are scant, but it appears that the program works (at least in part) as follows: The NSA partners with U.S. telecommunications companies that then make agreements with international companies for their Internet data. There are likely many different means through which the NSA intercepts these companies’ information. Based on conversations with Drake, the FAIRVIEW program also appears to encompass direct link-ups with offshore submarine cables. It is likely that the former operation fall under the purview of the BLARNEY program.
Overview: BLARNEY is, in short, the international version of the PRISM program. It is one of the many component programs that fall under the umbrella of FAIRVIEW. Through BLARNEY, the NSA forms partnerships with foreign telecommunication companies to gain access to their customer data.
What data is collected? Very little has been published about BLARNEY’s exact operations, but it appears to focus specifically on metadata. In early June, the Washington Post reported that BLARNEY “gathers up ‘metadata’—technical information about communications traffic and network devices—as it streams past choke points along the backbone of the Internet.” Metadata focuses not on the contents of communications but on where and when they were sent.
How is the data collected? The exact details of how the data is collected are unclear, but it appears that the information is provided to the NSA by both foreign intelligence agencies and commercial partnerships with companies. For example, Der Speigel and the Guardian have disclosed NSA partnerships with both German and British intelligence agencies. In the latter case, this partnership has afforded the agency access to information moving over the networks of major telecom companies, like BT and Vodafone. It is unclear, however, whether these partnerships are directly associated with BLARNEY.
Overview: Like BLARNEY, the STORMBREW and OAKSTAR programs appears to fall under the umbrella of FAIRVIEW. Little is known about them other than that they are listed under the line “Collection of communications on fibre cables and infrastructure as data flows passed” on a slide published (for the first time without redaction) by the Washington Post. Drake described STORMBREW to the Daily Dot as “just another exploitation system.”
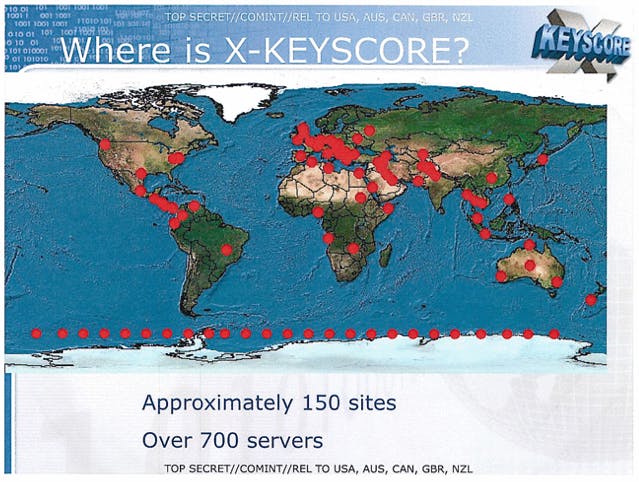
Overview: Referred to by the NSA as its “widest-reaching” program, XKEYSCORE is a surveillance tool that builds a searchable database of both metadata and communications content collected from around the world.
What data is collected? According to the Guardian, a report on XKEYSCORE by the NSA listed the project as collecting “nearly everything a typical user does on the internet,” including the content of emails and chats, visible in real time. A top secret slide explaining XKEYSCORE to NSA agents depicts a graphic of an agent sitting at a personal computer. An arrow with the word “queries” printed on it connects the agent’s computer to a database containing “phone numbers,” “email addresses,” “log ins,” and “user activity.”
How is the data collected? How exactly data is amassed by the program isn’t explicitly clear. It may function as a sort of umbrella program taking intelligence from many other sources. According to reports by both Der Spiegel and the Guardian, the NSA shares XKEYSCORE with both British and German intelligence agencies. Metadata is stored for 30 days, while the content of communications are sometimes stored for as little as a day. In one XKEYSCORE training slide produced by the NSA, over the course of a 30-day period in 2012, the NSA held 41 billion Internet records in its XKEYSCORE database. This intelligence is kept in over 700 searchable servers around the world.
Unlike, PRISM, accessing information through the program doesn’t require agents to obtain a warrant. They need simply fill out a brief questionnaire, asking them to answer questions about their target’s “foreignness factor.”
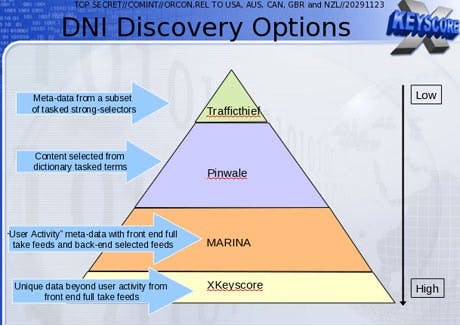
MARINA, TRAFFICTHIEF, & PINWALE
Overview: The only mention of these three programs is in a slide from the XKEYSCORE presentation comparing the size of various NSA databases: The smallest, TRAFFICTHIEF, is described as containing “metadata from a subset of tasked strong-selectors”; PINWALE, the next smallest, contains “content selected from dictionary tasked terms”; the next in size, MARINA, stores “user activity metadata with front end full take feeds and backend selected feeds.” No other information has been published about what exactly these descriptions mean.
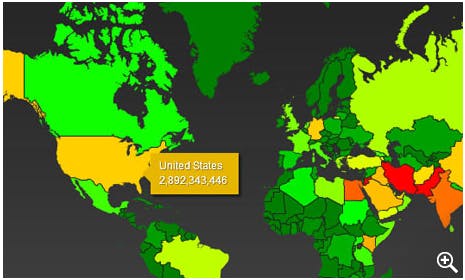
Overview: Distinct from most of the other programs mentioned on this list, BOUNDLESSINFORMANT is a measure of how well the NSA’s various intelligence gathering operations are doing. Slides given to the Guardian by Snowden indicated that in one month in 2012, the NSA collected almost 100 billion “pieces” of intelligence worldwide. Three billion pieces of intelligence were collected in the U.S. during that same period. Presumably an email or phone call would constitute a “piece” of intelligence.
Illustration by Jason Reed