A devastating malware capable of hijacking almost every Android smartphone feature to obtain passwords, listen to call recordings, and steal photos from memory cards, is only getting stronger.
Dubbed ZooPark, the sophisticated attack discovered by Kaspersky Lab has primarily been used on targets in the Middle East for the past three years. Alexey Firsh, a security expert at the embattled cybersecurity firm, told the Daily Dot that there have been several dozen victims, “up to 100” based on internal statistics and sinkhole server data. The low number suggests the attack targets select users and may be backed by a nation-state.
Most concerning is how the malware has evolved over the years. In its earliest stage, it would mimic the Telegram application and only steal contacts from an address book and accounts registered on the device. A second version expanded its functionality with spying features for GPS location, SMS messages, call logs, and some other general information. Another update improved the malware by allowing it to steal audio recordings of phone calls, browser data including bookmarks and history, information on installed apps, and photos from memory cards.
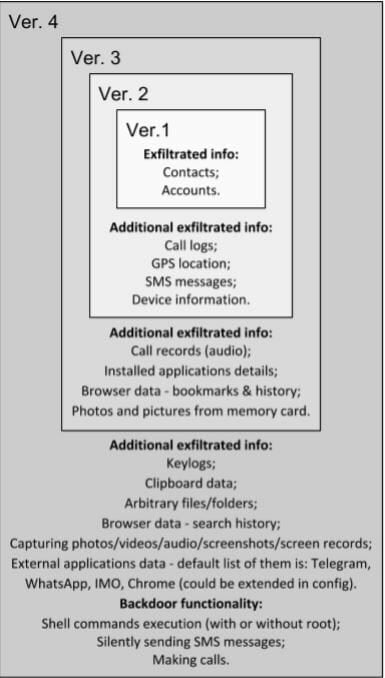
The latest improvements can steal search history, clipboard data, and keylogs. Given the huge jump in advancement from the third version, Kaspersky believes the newest update was made using commercial spyware purchased from vendors of specialist surveillance tools.
“This malware is an example of mobile spyware that is able to remotely control a device and to steal almost all confidential information from it,” Firsh said.
The attack was spread through two different pipelines, the Telegram instant messaging app and watering holes. Watering hole exploits are when bad actors attempt to attack a specific group of users by infecting a website they are known to frequently visit. According to Kaspersky, the Al-Nahar news site, the 19th most popular website in Egypt, and its sister site in Lebanon were exploited to distribute the malware. French fashion site Showroom Montorgueil was also found hosting the malicious code.
The malware has been most active in Egypt, Jordan, Morocco, Lebanon, and Iran. Current evidence suggests it targeted individuals voting for a 2017 independence referendum in Kurdistan, along with other high-profile groups like the United Nations Relief and Works Agency for Palestine Refugees in the Near East.
Firsh says this particular threat is mostly contained within a specific geographical region, but Android users should still be concerned about their privacy, given the increasing amount of attacks targeting the operating system. The ZooPark malware is still active. Kaspersky did not notify Google of the attack because the malware was not found in the official Google Play app store.
“In general, Android users should only download apps from the official Google Play store, to lessen the threat of downloading a malicious application,” Firsh noted. “Even when downloading from official stores, always double-check the name of the application and creator and be cautious of those that you are unfamiliar with. Finally, consider installing an antivirus solution on your Android device, which can protect against advanced threats like ZooPark.”
Google did not respond to our request for comment.


