Anyone with a simple email address could have posted the controversial boner-in-underwear photo to Representative Anthony Weiner’s Twitter account that is roiling the Internet.
The revelation could help the embattled politician, whose missteps in responding to the scandal have helped fuel the efforts of amateur factcheckers to get to the bottom of the Weiner affair.
The picture in question — a shot of a man’s crotch in gray underwear — was sent to Twitter via ImageShack’s photo- and video-posting service, Yfrog.
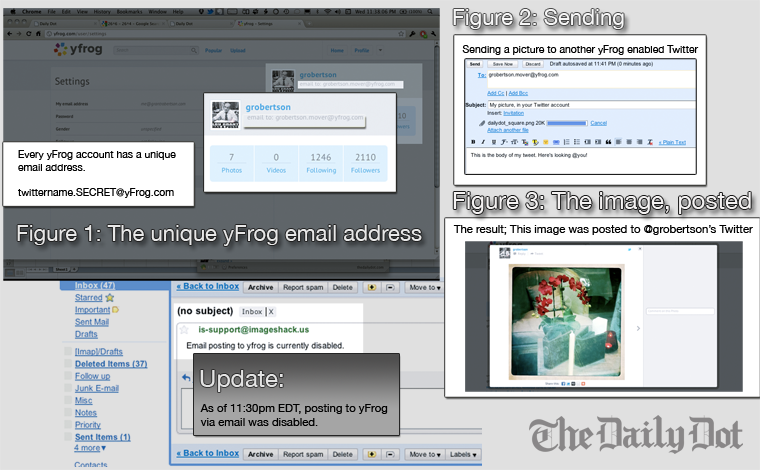
To post a Yfrog photo, one can use a number of common Twitter clients that support it. One also can log into the Yfrog website.
Or one can simply send a photo via email using an email address generated by Yfrog, as readers of Joseph Cannon’s Cannonfire blog pointed out.
Daily Dot’s own investigations confirm their observations that the email addresses Yfrog generates are not that secure, potentially putting millions of users in danger of Weineresque exposure. (ImageShack has said in a job listing that Yfrog has approximately 50 million monthly users.)
As of deadline, ImageShack had not responded to the Daily Dot’s calls or emails. The Daily Dot spoke in person to an ImageShack employee at its Los Gatos, Calif. office who identified himself as “Alex” and said company executives were out of the office and hence not available. However, Yfrog’s website announced late Wednesday evening—after our inquiries—that it had suspended posting via email.
The posting addresses we generated before Yfrog suspended the feature follow a format of one’s Twitter username followed by a period and then a random word five to six characters in length, ending with @yfrog.com.
Such addresses could be vulnerable to what’s known as a “brute-force attack” using a dictionary of common word parts, a technique where hackers try random words to eventually guess passwords or other security measures. Yfrog’s automatically generated random word appears to always be of a predictable length, dramatically decreasing the time it would take a hacker to find the “secret” random word.
Adding to the insecurity, Yfrog does not require that users send photos from a verified email address.
A Cannonfire reader claimed that Yfrog subtly changes the display of photos posted through a different email address, omitting a URL that normally appears. Screenshots of the photo posted to Weiner’s account showed this same quirk.
The Daily Dot was not able to replicate this behavior in its tests, however.
This is the latest wrinkle to a story that has captivated bloggers, Tweeters, — and especially political conspiracy theorists — since the story broke just after people had taken off for Memorial Day. On Friday evening conservative blogger Andrew Breitbart ‘s blog Big Government ran an item posting the erection picture and saying Weiner had sent it to a Washington State college student.
Weiner quickly tweeted that he’d been hacked — though he claimed it was on Facebook, not Twitter or Yfrog — and took the picture down.
The awkward response was oddly uncharacteristic of a techno-savvy politician who’s actively embraced tools like Twitter, where he uses hashtags as insider jokes, and communities like Reddit, where he maintains an account and participated in a popular question-taking forum.
The discovery of Yfrog’s apparent security hole lends credence to Weiner’s contention that he wasn’t the one to post the photo. But it raises questions about who might have had access to the email address — and the photo.
Weiner has said he doesn’t know for sure that it’s not a photo of his own crotch. (You’d think he’d know, but that’s what he’s saying.)
One possibility: a disgruntled aide who worked on Weiner’s social-media efforts.
Still another: Someone could have gotten the email from Weiner’s contacts — on his BlackBerry or computer. (Someone with access to those files might also have access to photos Weiner took using his cameraphone.)
Or, lastly, any hacker with the time and inclination to run a simple brute-force attack could have sent it in — though that doesn’t explain the provenance of the photo.
This latest revelation is unlikely to put Weiner at ease.
Instead, as with other bits of evidence scraped up about the photo, it’s likely to get viewed through people’s political lenses.
That has much to do with the origin of the story: Breitbart is a famous pot-stirrer who is no friend to those on the left. And Weiner isn’t some random politico: He’s a prominent New York Democrat whose name often comes up in talk of higher offices (as well as bad puns) and was known for his active social life before his marriage last year to Huma Abedin, a former aide to Hillary Clinton.
Grant Robertson contributed reporting to this article. / Photo by Pablo Manriquez (CC BY 2.0)


