How much would you pay to avoid losing the wedding pictures stored on your computer? What about the financial documents for your small business? Or the first two chapters of the great American novel that you’re totally going to finish at some point?
Over the last few months, computer users around the world have been on the receiving end of a particularly troubling threat—pay $300 to a computer hacker who has installed an insidious virus on their systems or lose access to their files forever. The kicker: a ticking clock indicates they only have 100 hours in which to send the money.
The virus is called CryptoLocker. And while the blackmail attempts may initially seem like idle threats, failing to pay could result in the files on hard drive getting cryptographically locked, making them effectively unusable.
After being downloaded, CryptoLocker installs itself in a user’s “Documents and Settings” folder. It then scans the hard drive for a whole host of different file types—from family photographs to Microsoft Word and Adobe Photoshop documents—and encrypts them.
Once the encryption is complete, CryptoLocker launches a pop-up window informing the user they have exactly 100 hours to pay the ransom. If the target pays up, the program provides the key. However, if the deadline lapses without payment, the key is supposedly destroyed.
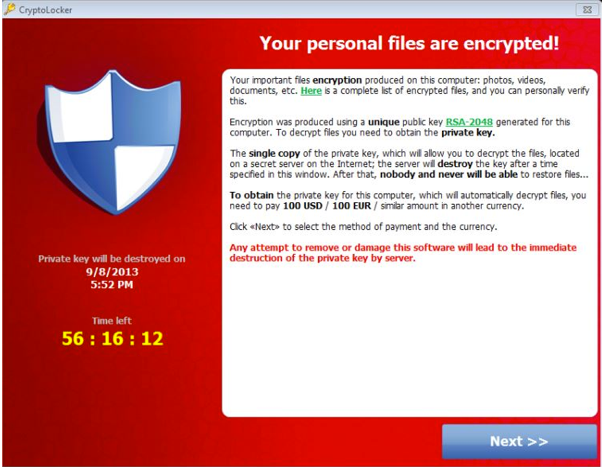
SophosLabs’ Naked Security blog warns that with the key destroyed, there’s not much someone can do to recover their files. The firm said it had received a large number of “scrambled documents” from victims of the virus, clearly hoping the company could do something to restore them.
“But as far as we can see,” the company wrote, “there’s no backdoor or shortcut…[what’s been] scrambled, only the private key can unscramble.”
Catching the criminals behind the scam might be the only way to save encrypted files, assuming they’ve kept copies of the keys
The virus breaches computers via phony emails that look like they’re well-respected organizations, such as the Better Business Bureau or package tracking notifications from FedEx or UPS.
Victim payments are handled either through Green Dot MoneyPak reloadable debit cards or the anonymous digital currency Bitcoin.
Interestingly, the whole scheme seems to mimic the plot of sci-fi author Neal Stephenson’s novel Reamde, in which the virus encrypts files on computers to extort gold used in a popular massively multiplayer online role-playing game.
CryptoLocker is the most extreme example of “ransomware.” Typically, malware of this genre is either entirely fake or simply freezes the infected computer—something computer experts are generally able to fix. However, CryptoLocker is the first widely-reported instance where a ransomware program will actually go as far as permanently encrypting files on a host’s computer.
H/T Info Security | Photo by Photo by mandyxclear/flickr


