The wireless network that your phone uses is fast and ubiquitous, but new research shows that its weak security protocols could let hackers access your phone, track your location, and even disable your access to the network.
Researchers discovered that, using flaws in the 4G LTE network, an attacker can precisely locate targets with GPS coordinates, downgrade their network connections to exploit old vulnerabilities, and manipulate the devices themselves.
“The LTE access network security protocols promise several layers of protection techniques to prevent tracking of subscribers and ensure availability of network services at all times,” said the researchers, who work at Technische Universitat Berlin, Telekom Innovation Laboratories, Aalto University, and the University of Helsinki. “We have shown that the vulnerabilities we discovered in LTE access network security protocols lead to new privacy and availability threats to LTE subscribers.”
By the end of this year, approximately 1.37 billion devices will use 4G LTE. It is already in wide use in the United States. The researchers notified device manufacturers and network carriers about their discoveries, and they are reportedly fixing the problems now.
Attackers can use Facebook Messenger and Whatsapp to silently trigger pings from a rogue network, sending them the device’s location and then tracking its owner with varying degrees of precision. These pings can reveal the device’s past and future movements, too.
Sending Facebook messages to someone or even beginning to type a message to them in Whatsapp will trigger these pings, which effectively light up neon arrows pointing at the device from the perspective of an attacker monitoring the network.
Repeated friend requests and Facebook poking also trigger the pings, but they notify the user, making it a less effective method of attack. Phone calls work the same way. (Facebook messages are only stealthy because Facebook puts messages from non-friends into an “Other” folder, but the company is about to eliminate that feature.)
The problem exists in part because mobile network operators like Verizon and AT&T don’t do enough to hide and shift the ID numbers used for specific devices. Numbers meant to be temporary (like the a Globally Unique Temporary Identifier or GUTI) change only slowly over the course of days; sometimes they remain the same for weeks. Once an attacker has a device’s ID, he can track the device and its owner to within 2 square kilometers.
While 4G LTE is thought to be the most secure mobile-network protocol, German and Finnish researchers found ways to downgrade the connection to 2G and 3G networks, opening up even brand-new devices to vulnerabilities found in those older protocols.
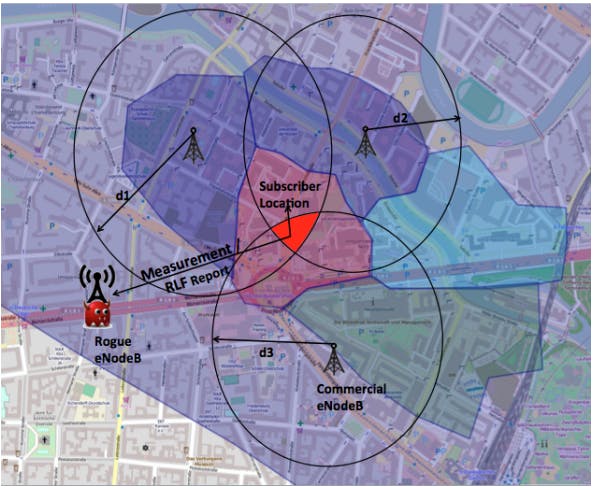
Savvy attackers use devices like a Universal Software Radio Peripheral and software like OpenLTE to monitor and decode wireless signaling messages, trigger their own messages, and even operate their own rogue base stations on the network.
“We demonstrated that our attacks can be mounted using open source LTE software stack and readily available hardware at low cost,” the researchers wrote. “We tested several handsets with LTE support of major baseband vendors and demonstrated that all of them are vulnerable to our attacks. In addition, we demonstrated our new privacy attacks in real LTE networks of several major operators.”
The attack is not easy to execute, but the necessary equipment is readily available. An attacker must also be familiar with the LTE network’s technical specifications.
To demonstrate the technique, the researchers built their own rogue base station with high-priority frequencies, essentially forcing nearby mobile devices to connect to the fake station.
The rogue base station allows an attacker to track devices and people even more precisely by intercepting measurement and error reports that devices sends out across the network. An attacker can then measure how close a device is to real base stations by measuring signal strength and then, using trilateration, calculate exactly where the person is.
The researchers also invented three new denial-of-service attacks that can force people off of LTE as well as older 3G and GSM (2G) networks.
To make sure they didn’t unintentionally force other mobile devices in the area to connect to the rogue station, researchers carried out the attacks inside a Faraday cage that quarantined them off from the rest of the world.
The researchers did not respond to a request for comment.
Photo via John Karakatsanis/Flickr (CC BY 2.0) | Remix by Max Fleishman