Top secret documents released today by Edward Snowden and the Guardian revealed attempts by the U.S. and U.K. governments to crack Tor, the anonymizing tool widely used by dissidents, activists, and cybercriminals around the world.
Although Tor came out ahead with its network security intact, the documents reveal NSA did have success in attacking some users’ computers.
Tor is described by the NSA as “the king of high-secure, low-latency anonymity. There are no contenders to the throne in waiting.”
One slide that has inspired real glee in Tor users around the world is titled “Tor Stinks.” It says “We will never be able to de-anonymize all Tor users all the time. With manual analysis we can de-anonymize a very small fraction of Tor users.”
The agency has had “no success de-anonymizing a user in response” to a specific request.

This revelation comes just days after the collapse of Silk Road, the infamous Deep Web black market built around Tor’s powerful anonymizing technology. According to FBI documents, Silk Road was compromised and seized because of poor security on the part of Ross William Ulbricht, its alleged leader, rather than any technological problem on the part of Tor.
The presentations do detail some semi-effective attack against Tor users through vulnerable software.
The slides leaked from NSA and GCHQ presentations also claim, in bold red type, that “Terrorists!” use Tor.
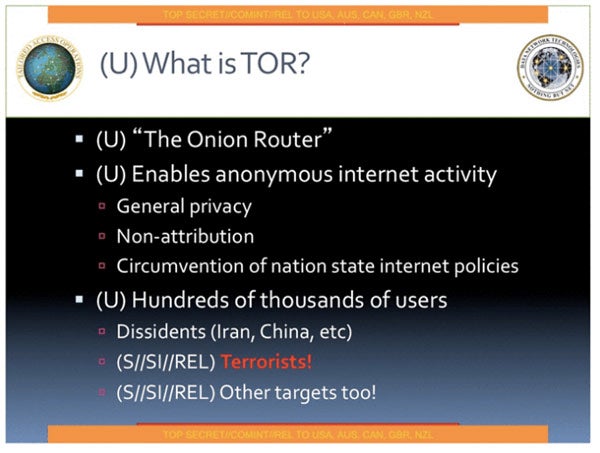
Illustration by Jay Hathaway


