The devastating Christmas Day attacks against the gaming networks of Sony and Microsoft were a marketing scheme for a commercial cyberattack service, according to the hackers claiming responsibility for the attacks.
Known as Lizard Squad, the hacker collective says it shut down the PlayStation Network (PSN) and Xbox Live network on Dec. 25 using a distributed denial-of-service (DDoS) attack, a common technique that overloads servers with data requests. The powerful attacks rendered the networks unusable for days, infuriating gamers around the world and causing yet-untold losses of revenue.
“Playing games on a Twitter is fun, but it comes down to the money.”
Now, members of Lizard Squad say the group is selling the DDoS service they used against Sony and Microsoft to anyone willing to pay.
The service, dubbed Lizard Stresser, launched early Tuesday morning via Twitter (redacted below) and is fully operational, a Lizard Squad member who goes by the alias “dragon” told the Daily Dot via a direct message on Twitter and subsequent conversation through the instant messaging service Jabber. Customers can use the service against any target they wish, including large websites or Internet services, such as PSN or Xbox Live. Dragon, who is listed as co-owner of the service, says the launch of Lizard Stresser will be the group’s last move before they “vanish off back to the caves where we came from.”
A DDoS attack sends a huge amount of traffic to a server or computer network, swamping its capacity. The overload of “fake” traffic means legitimate users can’t connect, rendering the network temporarily unusable. While DDoS attacks may be considered a form of protest, they have been interpreted as a violation of the Computer Fraud and Abuse Act.
It’s worth noting that DDoS attacks don’t require actual hacking the traditional sense. “A DDoS attack does not involve breaking into someone else’s computer in any way. It doesn’t expose user data, doesn’t destroy files,” noted hacker Gregg Housh wrote in the Kernel earlier this year. “It’s like a hundred crazy couponers blocking every lane in the grocery store: It’s obnoxious but not damaging anything.”
A powerful DDoS attack requires access to a botnet—a network of computers under a hacker’s control, capable of generating large amounts of traffic. Anyone who purchases the Lizard Stresser service, dragon claims, immediately has the ability to launch major DDoS attacks.
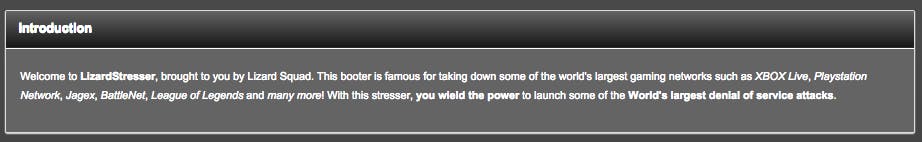
Once customers log into Lizard Squad’s new service, they are greeted by a list of the group’s accomplishments:
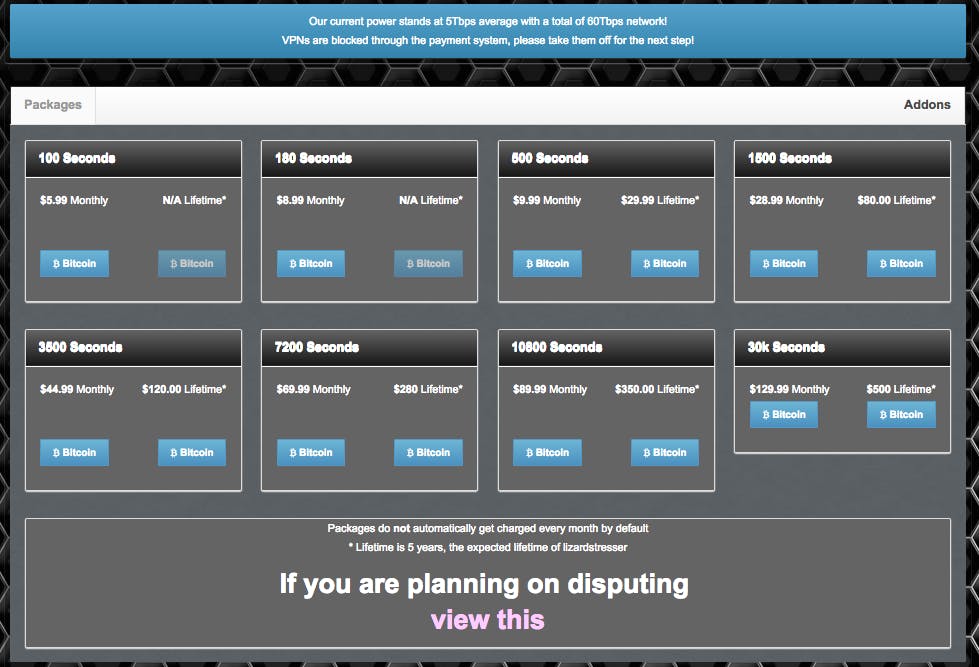
The cost of attacks range anywhere from $6 to $500, paid for with Bitcoin, the difficult-to-trace cryptocurrency. The most expensive tier offers 30,000 minutes of attack (a little more than 20 days), and costs just $130 per month. For $500, customers can launch unlimited attacks.
With the notoriety achieved from their attacks on Xbox Live and Playstation Network, Lizard Squad plans to utilize their huge social media reach to attract potential customers.
The attacks on Xbox Live and PSN were all “a huge marketing scheme,” dragon told the Daily Dot. “Playing games on a Twitter is fun, but it comes down to the money. The objective here, for me at least—can’t speak for others—is money.”
That’s a notable change in tune from the first time the Daily Dot spoke with Lizard Squad. On Dec. 26, two self-proclaimed Lizard Squad members—verified by making specific changes to their website, a post in Internet Relay Chat, and tweets from Lizard Squad Twitter accounts—claimed they did it for the “lulz.”
“Microsoft and Sony are fucking retarded, literally monkeys behind computers,” a Lizard Squad member going by the alias Vinnie Omari said. “They would have better luck if they actually hired someone who knew what they were doing. Like, if they went around prisons and hired people who were convicted for stuff like this, they would have a better chance at preventing attacks.”
Lizard Squad are not the first to set up a commercial DDoS service. Dozens of similar services, known as “rental booters,” are publicly for sale on hacking forums. What sets Lizard Squad apart, the group claims, is the alleged size and strength of their botnet. Their purchase page says that the Lizard Stresser service offers attacks with an “average” load of 5 terabits per second (Tbps)—the total amount of fake traffic with which all customers can bombard their targets. The group also claims that its botnet provides “a total of 60 terabits per second,” but that number—which is effectively impossible—is just a joke, according to dragon.
A cybersecurity analyst who has kept “very close” watch on Lizard Squad’s activity says that even the 5Tbps figure may be an exaggeration—but that may not matter.
“My opinion overall is that they maybe don’t have 5 terabits of power behind them,” says the analyst, who asked to remain anonymous for fear of retaliation from Lizard Squad. “But assuming they’re using the same botnet that they used against Sony and Microsoft, they certainly have one of, if not the, strongest booter available.”
Within three hours of launch, 25 customers have already purchased Lizard Squad’s services, according to dragon. Lizard Squad hopes that they will be able to keep this service online for a “minimum of one year.” Members of the group were not able to tell us what sites customers were targeting, as they don’t keep any logs, citing “privacy reasons for criminals.”
Sources tell the Daily Dot one member of the Lizard Squad, “ryanc,” is currently under investigation by the FBI. Allegedly a 17-year-old citizen of Finland, ryanc was allegedly arrested by Finnish police in 2013 for running a major botnet made up of more than 60,000 servers around the globe.
Correction: 30,000 minutes of attack equals 20.83 days.
Photo via Dallas Krentzel/Flickr (CC BY 2.0) | Remix by Jason Reed