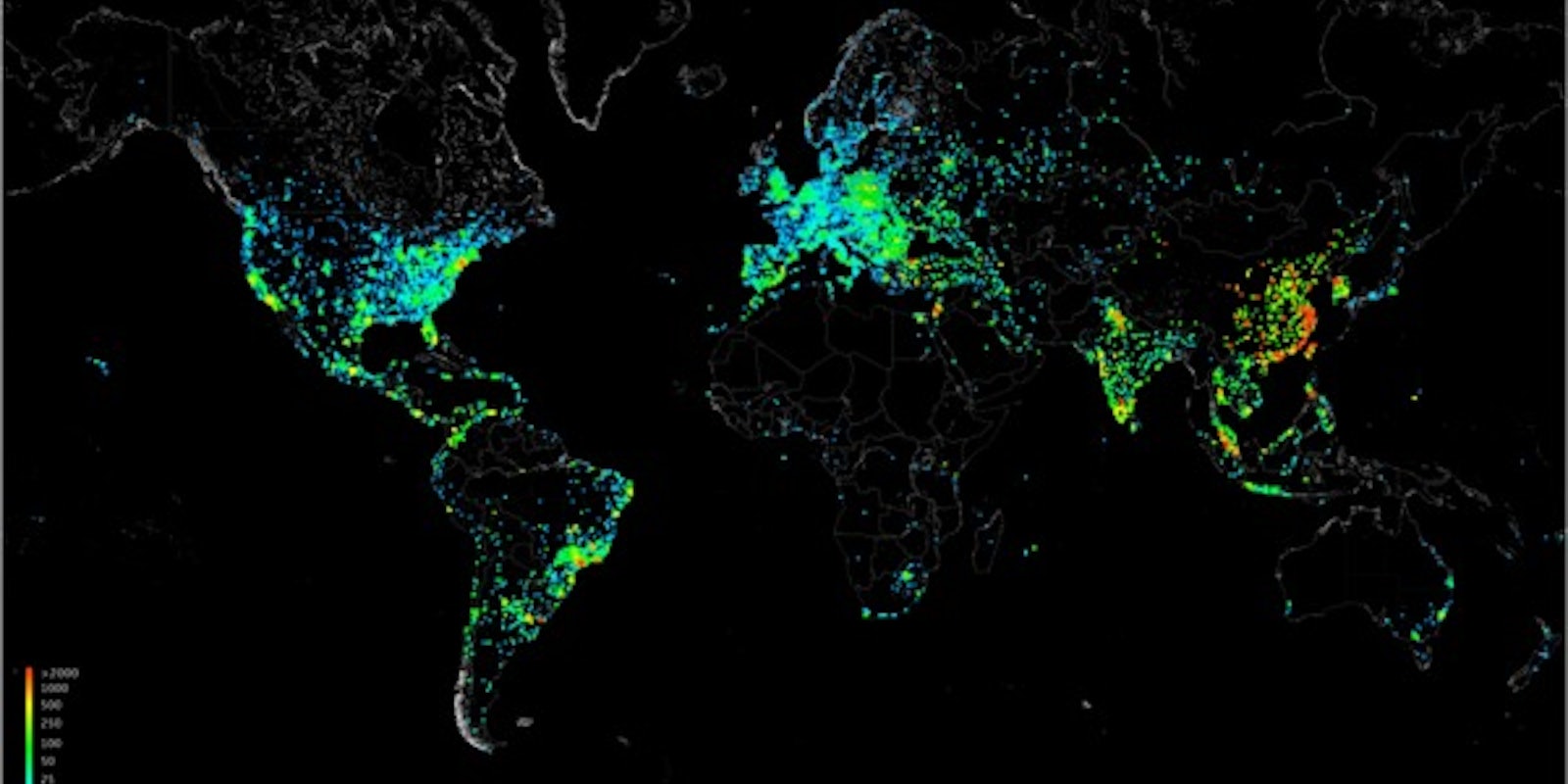
A project to measure the size of the Internet started with a joke and ended with an illegal botnet that took control of hundreds of thousands of computers and other Internet-capable gadgets.
“Two years ago while spending some time with the Nmap Scripting Engine (NSE) someone mentioned that we should try the classic telnet login root:root on random IP addresses,” wrote the anonymous researcher behind the Carna botnet. “This was meant as a joke, but was given a try.”
This seemingly silly idea—trying to scan every computer on the Internet using a default username and password—became the very serious concept behind Carna, an allegedly research-driven botnet experiment that ran from March to December of last year. It was designed as a census of IPV4 addresses—in other words, most of the Internet-connected computers, modems, routers and printers in the world.
The census project attempted to answer the question “How big is the Internet?”
And how big is it?
“That depends on how you count,” wrote the researcher.
But here were some of the “census data” that were derived from the botnet.
-
420 Million pingable IPs
-
36 Million more that had one or more ports open
-
141 Million IPs firewalled, so counted as “in use”
- 729 Million more IPs had only reverse DNS records
All together, that makes 1.3 billion IP addresses the researcher determined were in use.
Nine terabytes of data were collected during the study, all of which has been “released into the public domain for further study.”
Carna turned out to be an effective way of measuring a big chunk of the Internet, but there’s one major catch: It’s illegal and invasive, which no doubt explains why the researcher has remained anonymous. Carna was, as per the name, a botnet, a type of malware secretly loaded into any device it could penetrate. At its peak, the botnet controlled an estimated 420,000 devices.
“We used the devices as a tool to work at the Internet scale,” wrote the Carna author. “We did this in the least invasive way possible and with the maximum respect to the privacy of the regular device users.”
Although Carna was allegedly designed to minimize intrusion and avoid damaging an infected device or process, it remains a virus that a hacker used to infect millions of devices with no notice and no permission.
According to the Carna author, though, everyone whose devices he was able to scan should have changed their passwords ages ago.
“While everybody is talking about high class exploits and cyberwar, four simple stupid default telnet passwords can give you access to hundreds of thousands of consumer as well as tens of thousands of industrial devices all over the world,” he wrote.
Images via Internet Census 2012