It may have sounded like clapping, but that noise you heard yesterday was actually droves of computer programmers slapping their hands against their foreheads.
TweetDeck was the reason for their exasperation. In violation of ultra-basic Web security rules, users of the Web and Google Chrome versions of the Twitter-viewing client discovered that the application contained a cross-site scripting (XSS) vulnerability that could have been and was exploited in various ways.
While the person who uncovered the vulnerability was a seemingly innocent 19-year-old who just wanted to use little hearts in his tweets, the most notable exploit came from someone who figured out how to code a tweet that would be automatically retweeted by anyone running vulnerable versions of TweetDeck. The tweet was retweeted more than 40,000 times in about 20 minutes, and it looked like this.
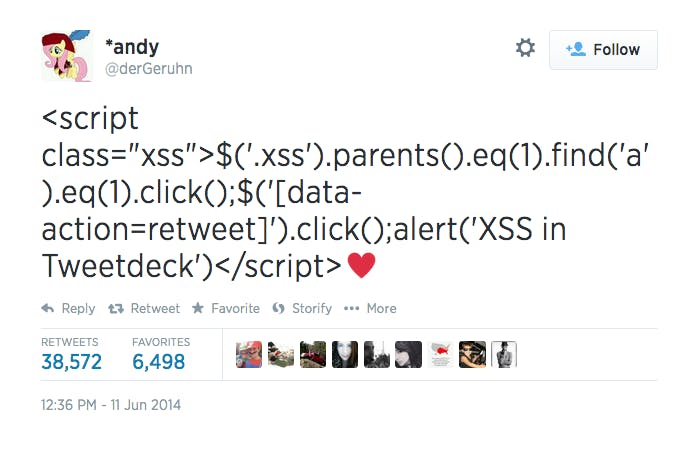
For those of us who aren’t familiar with computer coding languages like HTML and JavaScript, it looks like a complicated mess, but this video lays out the elements of the tweet, explains what they mean, and describes how they equate to a self-retweeting tweet.
You won’t be able to reuse this method to craft your own quintuple-digit-retweeted tweet, however, as TweetDeck patched the vulnerability several hours after the public learned about it.
H/T Digg | Photo by Marjan Krebelj/Flickr (CC BY 2.0)


