Malware apps—those invasive programs that slow down your computer and steal your personal info—aren’t just toys for mischievous hackers or identity thieves anymore. A new study provides more evidence that high-powered, corporate-funded malware programs, which can activate webcams or record your every keystroke, are being employed by autocratic states to track online dissidents. It’s the police state’s insidious response to the social Web, empowered by Western companies who seem intent to cash in on a booming young industry: Internet surveillance.
The computer takeover began the same way millions have before: With an email. The target was Ahmed Mansoor, a pro-democracy activist, blogger, and Web forum administrator in the United Arab Emirates, who, along with four other bloggers, was last year arrested for insulting the country’s leaders. It took a full pardon from the UAE president to see them free in Nov., 2011. But as Mansoor quickly discovered, he was never really free.
The sender was “Arabic WikiLeaks.” And since its subject read “very important,” in Arabic, Mansoor, 42, and a father of four, promptly opened the attached Microsoft Word document. Once opened, he saw nothing but scrambled data and text. It was a trap.
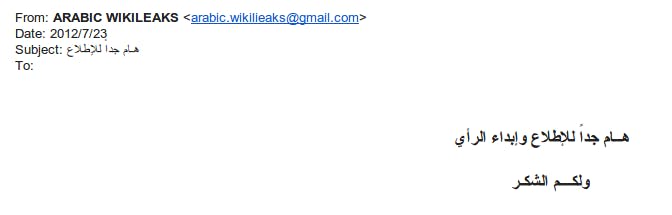
Opening that document allowed the software to exploit a security hole in Microsoft Office. Mansoor’s computer was no longer really his. Thanks to a secure connection over the Internet, someone, somewhere, had complete access through the computer’s backdoor.
There were no obvious signs Mansoor’s PC had been compromised—but he soon noticed that it had slowed down considerably. Mansoor had heard of activists in Bahrain getting hit with tracking software, and had suspicions about the email from the very beginning. With the help of a friend at pro-democracy group Bahrain Watch, Mansoor tracked down the culprit to somewhere in the UAE.
The University of Toronto’s Citzenlab recently dug into the origin of the worm. Their results are surprising. Unimaginatively called “Remote Control System,” the program that took over Mansoor’s computer is a product of Italian company HackingTeam. The company describes itself as provider of “effective, easy-to-use offensive technology to the worldwide law enforcement and intelligence communities.” It calls the program that spied on Mansoor “offensive security,” and bills it as a “crime fighting tool.”
You can see an ad for the program on the HackingTeam site. It’s an amateurish production that you can imagine playing in the background of some cheesy Hollywood movie about hackers and state surveillance. Except “Remote Control System” is all too real.
In an investigative series last year, Wired for Repression, Bloomberg News exposed how Western companies are cashing in on the big business of repression. One American company, NetApp, made a cool $4 million for a single component of a program used by the Syrian government to track emails.
In April, President Obama issued an executive order giving the Treasury Department power to sanction individuals and companies that help authoritarian governments track dissidents online.
That order obviously doesn’t apply to an Italian company like HackingTeam.
Mansoor finally scrubbed his computer completely clean on Aug. 7. A month later, he was physically assaulted by a stranger as he walked to his car at night. He’s not sure if the two events are connected. But one thing is clear: In repressive states, physical and virtual violence now go hand-in-hand.
Photo via HackingTeam.it