Surely one perk of conducting your shakedown racket online, through an “untraceable” currency, is that it obviates the need to pick up an envelope or suitcase of cash in person, exposing oneself in the process. But as the hackers who came up with the most successful cyber scam of late have discovered, the people who blindly download invasive malware from a spam link are not exactly up to speed on the mechanics of something like Bitcoin.
CryptoLocker, as described by Bleeding Computer, a forum that hosts a comprehensive support section about it, is “a ransomware program that was released around the beginning of September 2013 that targets all versions of Windows.” Users who install it will find their personal files swiftly encrypted, at which point they get the ransom note: cough up a couple Bitcoins within the next 72 hours or say goodbye to your data. Then the bomb-like countdown begins.
With Bitcoins worth well over $400 apiece these days, the customary ransom can run close to $1,000, and several times more if victims miss the original deadline, triggering a price hike. And while no security expert would advise you to pay up, the CryptoLocker thieves this month attempted to streamline the process with the introduction of CryptoLocker Decryption. You can think of it as criminal customer service: “How may we rob you today?” Per Bleeding Computer:
For those users who are affected by CryptoLocker and did not have a backup, trying to pay the ransom has been a difficult process. This is because antivirus programs remove the infection or the registry key that is required to pay the ransom and decrypt the files. It appears that the malware developers were listening, as they have now implemented a decryption service that is designed to look like a customer support site.
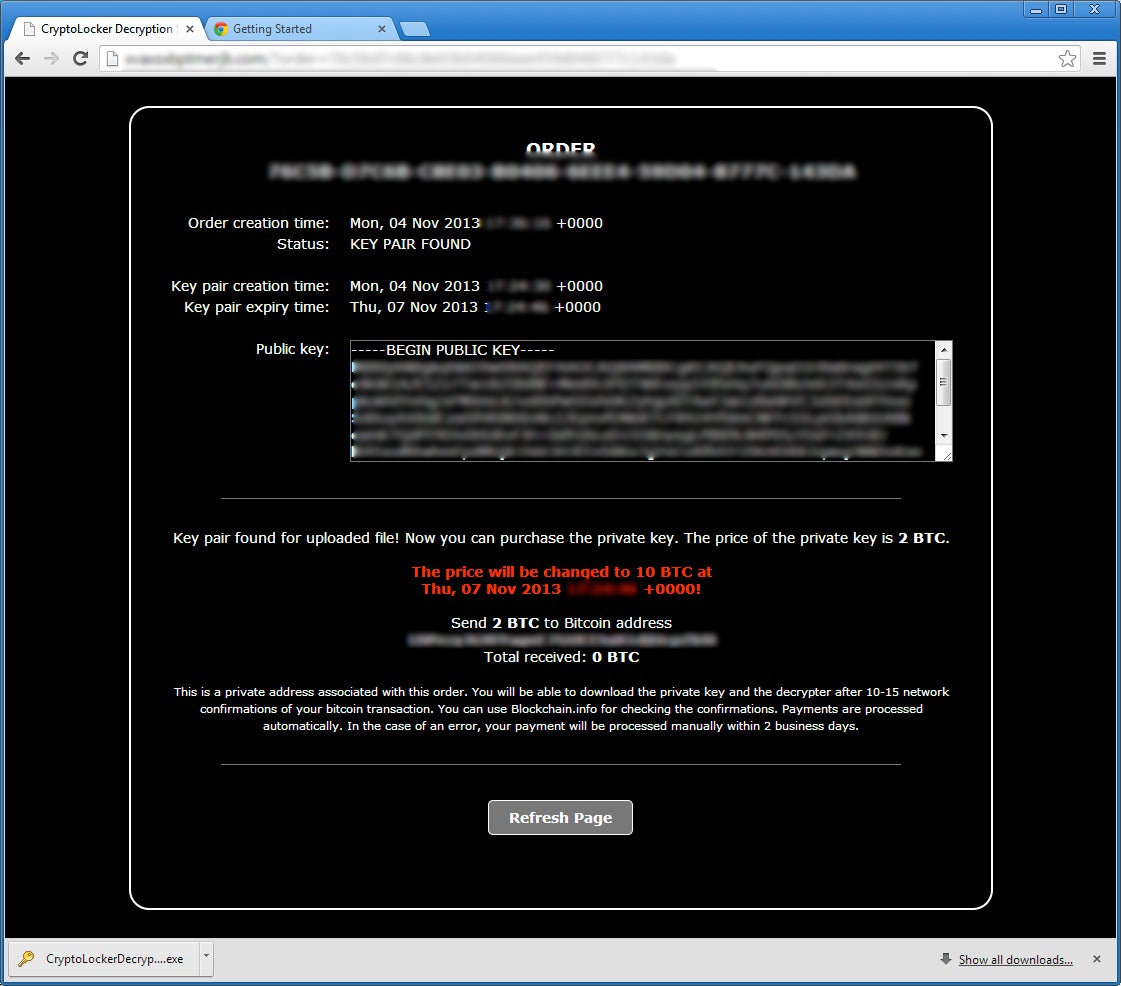
For something that purports to make the faceless transfer of funds easier, the new software isn’t all that user-friendly. It’s only accessible via the anonymous Tor network—another anonymizing tool that may be familiar to Deep Web denizens but not your average Internet tourist. Moreover, as Motherboard pointed out, “the only way to unlock the encrypted data is through the original virus, so users who had deleted it from their machine have to reinstall the malware.”
The slim percentage of victims both willing and able to jump through all these hoops are likely still enough to make the scummy enterprise worthwhile, but let’s face it: these crooks could be making a lot more money with something people can breeze through without thinking twice—like the iTunes user agreement.
H/T Motherboard | Photo by epSos .de/Flickr


