Are you a WordPress blogger? Yes? Did you spend the weekend attacking a gaming site? No?
Don’t be so sure.
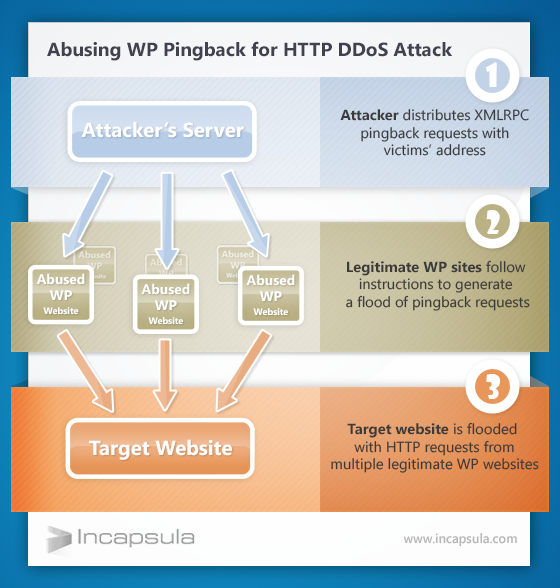
Incapsula, a Web services company that offers protection from distributed denial of service (DDoS) attacks, has announced that over the weekend one of its clients was the object of a sophisticated yet simple attack. The person or persons behind the assault exploited innocent WordPress sites to form an army of 2,500 blogs, all of which were sending relentless pingback requests to the target site.
A pingback is normally a good thing: It’s a way one blog says to another, “Hi, I linked to your content.” The problem comes when you have 2,500 blogs sending automated requests repeatedly and simultaneously; not many websites can withstand that kind of hammering for long. A normal DDoS attack consists of thousands of requests to load the site; this one consists of thousands of requests to link to the site, and it is just as disruptive.
Incapsula declined to name the victim of the attack but spelled out the mechanism and noted that hacking or infecting the interstitial sites (the ones doing the pinging) was not necessary in order for this to work. Even more worrying, Incapsula claims that 8.49 percent of the Alexa Top 25,000 websites are vulnerable to being exploited in this way.
Infographic from Incapsula
Although the company lists prominent WordPress.com sites such as Techcrunch.com as exploitable, I was unable to find a single WordPress.com blog on the list of sites that had been exploited; they were all independently hosted sites using software from WordPress.org. (Incapsula included the Italian version of Gizmodo and a Brazilian Hilary Duff fansite, as well as a metric snotload of personal and community blogs, many of which haven’t been updated in years.)
Clearly it is not necessary to be running WordPress 3.5 for your blog to be vulnerable. Any blog with pingback enabled can be exploited in this way, and most community-minded blogs do enable it, but WP 3.5 was simply the first version to have pingback enabled by default. Released in December of 2012, it didn’t take the Internet long to find out its weaknesses.
Incapsula recommends Incapsula (of course) to protect your blog from being attacked this way. To protect your blog from being used in this way to take part in an attack it advises renaming “xmlrpc.php” in the root directory, though you can also simply disable pingbacks from the dashboard if rooting around in php isn’t your idea of fun. If you don’t bother and your blog somehow becomes a part of an attack, you’ll notice everything going a little slower, if you notice anything at all. If you pay for bandwidth, you’ll get a fat bill. Otherwise, you probably will never know that your humble WordPress blog was hypnotized into robo-pinging some other site for reasons you’ll never learn, by people you’ll never know.
Illustration by mazeo, remix by Fernando Alfonso


