Security researchers at the Toronto-based Citizen Lab have identified 33 nations likely operating a known cyber-espionage program used to infect targets’ computers and phones, and intercept online messages and conversations.
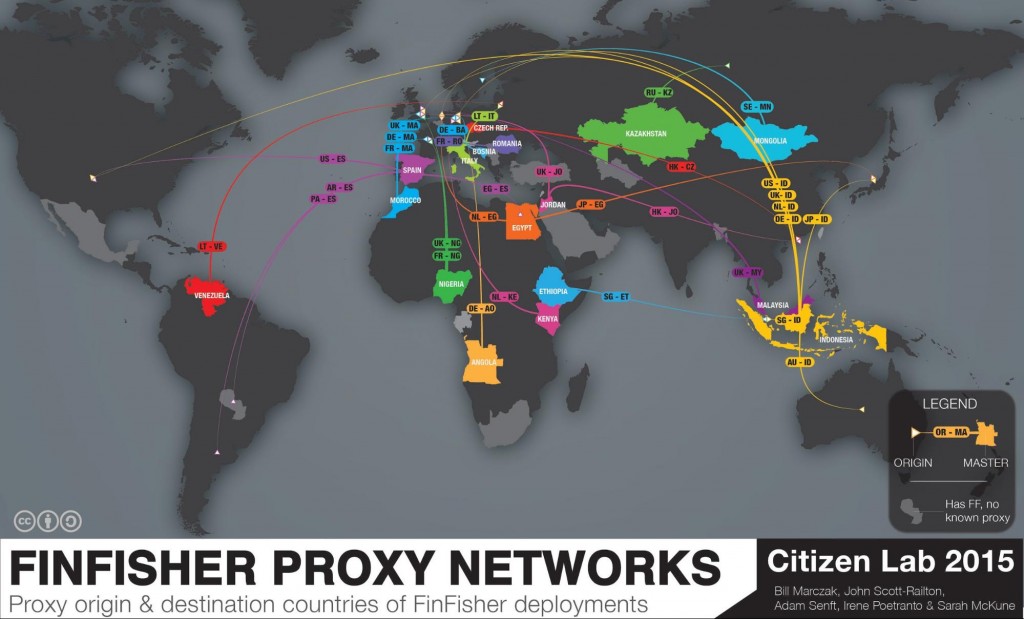
Citizen Lab was able to identify 135 IP addresses tied to a spyware suite developed by the Munich-based firm FinFisher, which is marketed to governments and law-enforcement agencies worldwide. According to researchers, the IP addresses are a mix of command and control (C&C) servers and proxy servers, which are used to obscure an attacker’s identity.
When the IP address of a FinFisher server is typed into a Web browser it typically returns a decoy page, such as a Google or Yahoo search page. The intention is to disguise the fact that server is a spyware server, Citizen Lab explains. Incidentally, the decoy pages are also what allowed the group to identify the C&C, or master server locations.
“In some cases, personal data improperly collected from civil society actors has led to their arrest and imprisonment.”
Remarkably, FinFisher’s proxy servers operating a Google decoy page responded to a “What’s my IP address?” query by apparently revealing the end-point location—and thus the proprietor—of the master servers. Another method for revealing the approximate location—but not an exact IP address—of FinFisher’s master servers was to retrieve geographical data provided by Yahoo, which was deployed as a decoy page on a “significant number” of the servers, according to Citizen Lab. “Yahoo utilizes a user’s location to customize several elements of Yahoo’s homepage, including weather and news,” the researchers noted.
A majority of the servers used Google and Yahoo decoy pages, but a few were customized to a different URL, Citizen Lab says. For example, servers in Italy and Taiwan mimicked local news websites.
“This design peculiarity is only the latest instance of fingerprint-able anomalies in spyware decoy pages,” Citizen Lab says, adding that “FinFisher or its clients may also be realizing that decoy pages are problematic,” as the group has observed fewer FinFisher servers returning decoy pages over time.
Human rights organizations have long criticized FinFisher for providing surveillance software to repressive and non-democratic regimes, which allow them to more easily target journalists and political dissidents. For example, the spyware was apparently sold to Egyptian authorities, which have a history of using violence against activists and civilians.
“Numerous Egyptian security agencies are permitted to conduct electronic surveillance, frequently with limited court oversight,” Citizen Lab says. “In some, personal data improperly collected from civil society actors has led to their arrest and imprisonment.”
Citizen Lab’s research likewise indicates that FinFisher has sold its spyware to the Directorate General of Forces Intelligence (DGFI), Bangladesh’s military intelligence agency, which has an extensive record of abuses, including torture, illegal detentions, and extrajudicial killings.
Photo via ▓▒░ TORLEY ░▒▓/Flickr (CC BY SA 2.0)