The global cyberwar just got a bit too real.
A huge and “ongoing cyberespionage campaign” against major companies in the energy sector of North America and Europe has given the attackers the ability to carry out industrially sabotage, damage, and disrupt industry across the Western world, security firm Symantec reports.
Active infections were found in 1,018 unique organizations across 84 different countries. Targets include energy grid operators, major electricity generation firms, petroleum pipeline operators, and energy industry industrial equipment providers in the United States, Spain, France, Italy, Germany, Turkey, and Poland. Until 2012, the cadre of attackers targeted mainly U.S. and Canadian defense and aviation firms.
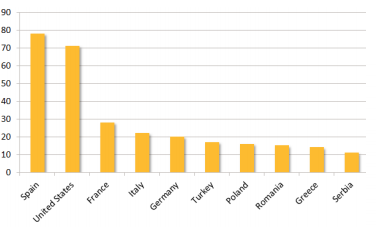
Image via Symantec
The attacker group, known as Dragonfly, is a well-armed group of unknown origin that is also known as Energetic Bear. The group has been around since at least 2011. They use a wide variety of malware to attack in various ways including spam email campaigns and watering hole attacks to steal control of crucial systems.
Although no one yet knows Dragonfly’s origins, the breadth and sophistication of its operations suggest the backing of a nation with interests in compromising Western companies. Not only that, but the attackers clearly had a Monday-to-Friday work schedule, according to Symantec analysis. They would check in at 9 a.m. and stop work at 6 p.m. on an Eastern European timezone.
“Dragonfly bears the hallmarks of a state-sponsored operation, displaying a high degree of technical capability,” according to Symantec’s blog.
“The group is able to mount attacks through multiple vectors and compromise numerous third party websites in the process. Dragonfly has targeted multiple organizations in the energy sector over a long period of time. Its current main motive appears to be cyberespionage, with potential for sabotage a definite secondary capability.”
The two main weapons in Dragonfly’s arsenal are two pieces of malware called Backdoor.Oldrea and Trojan.Karagany. Oldrea, Symantec has determined, is a custom program that can steal all of a computer’s data, download additional weapons, and open a backdoor to let attackers into the infected computer. Each weapon has infected up to 50 targets.
The “most ambitious attack” targetted industrial control system equipment providers with remote access-type Trojans, a common but effective type of cyberattack that allows someone to control a computer from a remote location. In this case, the hijacked computers were in charge of massive swaths of Western industry.
Although the group’s ability to sabotage and persistently access power plants recalls the famous Stuxnet worm used against Iran, Dragonfly’s capabilities are much more expansive.
H/T Symantec | Photo via Lennart Tange/Flickr (CC BY 2.0)
