The world’s nuclear power plants are inadequately prepared to deal with potential cyberattacks, according to a new report.
“The risk of a serious cyberattack on civil nuclear infrastructure is growing, as facilities become ever more reliant on digital systems and make increasing use of commercial ‘off-the-shelf’ software,” says the researchers behind an 18-month study from the London-based Chatham House. At the same time, the report notes, cyberattacks are becoming more widespread and easier to conduct.
The authors, following extensive interviews with cyber and nuclear experts from both industry and government, concluded that insufficient training and regulatory standards, limited collaboration with cybersecurity experts, and an unhealthy reliance on reactive (rather than proactive) security measures has produced a hazardous environment in which many nuclear plants may be unprepared for a large-scale cybersecurity emergency.
“Since owner-operators and vendors tend to focus on profitability and return on investment, they may not be spending enough on cybersecurity.”
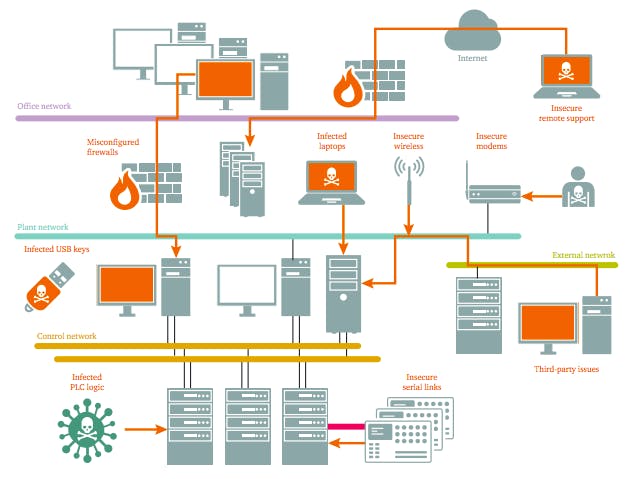
The risk of an attack that could potentially “release ionizing radiation” is, the report says, exacerbated by the “pervading myth that nuclear facilities are ‘air gapped’—or completely isolated from the public Internet—and that this protects them from cyberattack.”
“Yet not only can air gaps be breached with nothing more than a flash drive (as in the case of Stuxnet),” the report says, “but the commercial benefits of Internet connectivity mean that nuclear facilities may now have virtual private networks and other connections installed, sometimes undocumented or forgotten by contractors and other legitimate third-party operators.”
A multitude of technical, cultural, and industry-wide challenges contribute the problem, the researchers found. “Many industrial control systems are ‘insecure by design,’ since cybersecurity measures were not designed in from the beginning,” the report says. Basic security procedures are frequently ignored because nuclear plant engineers and cyber security personnel—who are often stationed off-site—fail to communicate due to the two groups’ different and highly technical terminologies. Security manuals, for example, are often written in a technical language unfamiliar to nuclear engineers and other on-site personnel.
The report lists four specific “threat actors” that pose a risk to nuclear facilities: “hacktivists; cyber criminals; states (governments and militaries); and non-state armed groups (terrorists).”
While the threat from hacktivists or cyber criminals is low, as they would likely avoid damaging any key systems, the authors warn that enemy states and terrorist groups are more likely to launch an attack that might endanger human lives or environmental safety. Any effort by a radical extremist group to penetrate a nuclear plant’s network and cause physical destruction, the report says, “is a question of time and money.”
The researchers found that the aim of most attacks would be the theft of confidential corporate data for financial benefit; however, more sophisticated attacks might cause a significant instability in a country’s power grid. The effects would range from a wide-spread loss of power to, in theory, “an uncontrolled release of ionizing radiation.”
An adversary with sufficient technical knowledge and adequate resources could mount an attack on a nuclear power plant that could trigger the release of significant quantities of ionizing radiation. All nuclear power plants need offsite power to operate safely and all have a standby generator system which is designed to be activated when a loss of mains power occurs. Attacks on the offsite power supply and the on-site backup system could create some of the effects that occurred following the 2011 earthquake and tsunami at Fukushima Daiichi, although multiple failures of the many safety features at modern nuclear power plants would also need to occur at the same time as that loss of offsite power and the disruption of standby generators.
“Since owner-operators and vendors tend to focus on profitability and return on investment, they may not be spending enough on cybersecurity,” the report concludes. “This, too, is a likely consequence of not thinking that the cyber security challenge is ‘real’: since the probability of a major attack is considered to be low, such expenditure is not considered a priority.”
Research released this summer found that Industrial Ethernet Switches, the devices that create the networks inside nuclear power plants and through which much of a plant’s function run, were the most susceptible to cyber attackers.
Image by Fernando Alfonso III