BY BEN KLEMENS
If you know the difference between HTTP and HTTPS, you can probably skip this part.
But for those of you not into tech acronyms, HTTP is the hypertext transfer protocol that your browser uses to talk to Web servers bringing you data. It is relatively simple, to the point that if you have a way to inspect the packets of data as they come down the wire, you could read the Web page right off of them. Those packets are being sent down a long series of routers between you and the Web server, and there is a not-insignificant chance that somewhere along the way they are being inspected or stored by criminals, overly aggressive advertisers, the U.S. National Security Agency, or some bored creep somewhere.
Thus, HTTPS, the secure version. Via HTTPS, the site you are connecting to (herein https://example.com, because I don’t feel like inventing something clever) has some associated encryption codes, and your PC (or phone or watch or whatever contraption you are connecting with) uses the codes to encrypt all data before sending it, and the other side sends encrypted data back. So all of the packets are basically illegible to any of the many parties that handle those packets, but are legible to you and the web server at example.com.
But what if the NSA intercepts your connection, tells you it is example.com, and tells your PC to use NSA’s preferred encryption codes? You send data encrypted with NSA keys over the wire, the NSA decrypts and records your data, then passes it on to example.com, and passes example.com’s requests back to you after recording those. You think nothing is wrong, but the man-in-the-middle (the NSA) has read all your communications, rendering all that encryption useless.
So you can’t trust the data until you get the right keys, but you can’t trust the keys as being from example.com until you get some other verification, but then how do you trust that other verification? The solution is a signed certificate registering the identity of example.com. There are a small number of certificate authorities providing such trustworthy certificates, and your browser knows them by name.
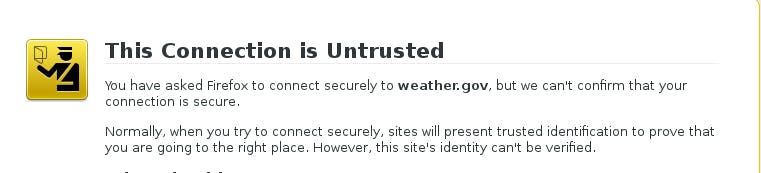
The current state of the world is that there is a mix of HTTP and HTTPS. Your bank uses HTTPS (and if it doesn’t, get a new bank immediately). But http://www.weather.gov/ works in plain HTTP, so snoops could determine for what locations you are checking the weather. Mozilla’s security team is taking its action to nudge the Web in the direction of being 100 percent HTTPS.
But this is a post about people, not security keys, so let’s talk about introverts.
Introverts are the dark matter of the social universe. If you measure the world of people by easy means, like Meetup groups, Facebook pages, tweets, or people who are willing to pick up the phone when an unknown person calls with a survey, you will get a massive undercount of introverts. Nobody ever shows up to Introvert Club meetings.
But every introvert has a family, so that is your most likely means of running into an introvert. When somebody tells you stories about the aunt or grandfather who doesn’t get out much (invariably accompanied with some comment about how they’re a little odd), there’s your introvert sighting. Most introverts have jobs or go to a school, so you might be able to sight one or two there. They try to stay quiet and out of the way and are often forgotten. At five o’clock, they disappear from the social grid.
So, you’re an introvert with some creative energy. Just because you don’t want to hang out with pals doesn’t mean that you have no curiosity about the world. What could you do?
In the last couple of decades, the answer to the introvert’s dilemma was easy: Get a computer and learn to code. Like a novelist (another popular introvert career path), you can create a new world using only words. Being an introvert is even beneficial here, because writing good code is time-intensive and you don’t have idle socialization competing for your time.
This is where I was as a kid. I couldn’t build physical things, because I’m a klutz and we didn’t have the money for parts. I was socially inept, to say the least. But I could spend time at the school computer lab, and I could borrow time on the PC of a friend who probably only put up with me because we’re both named Ben.
I don’t really remember what I built and doubt any of it was very good. I recall writing something to draw Mandelbrot sets, and some basic physics stuff. It doesn’t matter; what does matter is that I liked doing it, and it felt better than the alternatives.
I sometimes worry that I’m stuck in fifth grade, where I got lots of positive feedback for being good at solving little problems and writing code-like things. I certainly still spend most of my time doing things along those lines.
I felt that same sense of empowerment all over again when I had access to the Web. I was granted avocado.caltech.edu, back when the world was loose enough that Caltech’s sysadmins could hand out domain names like that, and a pal and I typed up a joke site for the Caltech Divinity School, with some verbiage about the physical chemistry of transubstantiation. The dozen people who saw it thought it was funny.
Of course, I built my do-it-yourself site on a laptop built in a factory, running an operating system, with a text editor and a network stack that could serve files to users. None of that detracted from the sense of DIY wonder of it all.
What kills that DIY wonder? Pulling out a credit card dampens it. Filling in registration forms definitely dampens it. If a tool is so well-built that solving the problem consists of just starting the tool up, my sense of wonder has gone from “Look what I did” to “Look what these other people did,” which is time-efficient but not especially fun. Building something from Legos takes enough personal effort and small-scale creativity that it feels like an achievement when the thing is built, but an Ikea end table is so pre-assembled that putting it together just feels like a little chore.
I spent a lot of time advocating against the patenting of information processing algorithms. If you want more detail on the history, you can read my law review article on the matter (PDF).
In the context here, it is understandable why an introvert would oppose software patents. If I’m sitting at home working on a project, why do I need to even consider checking with an attorney? Now that software has become patentable subject matter, writing code tangles you in the social web of lawyers and patent-holders, whether you want to be there or not. As with the NSA snooping your packets, the question is only whether those holding the patents notice you and decide to take their option of pursuing you.
The maintainers of Debian, a Linux/GNU distribution that emphasizes the freedom of free software, have a number of heuristics to determine whether a piece of software puts undue restrictions on a user, two of which are about introverts (due to preference or circumstance). From summaries from https://people.debian.org/~bap/dfsg-faq.html:
The desert island test
Imagine a castaway on a desert island with a solar-powered computer. To be free, software must be modifiable by this unfortunate castaway, who must also be able to legally share modifications with friends on the island.
The dissident test
Consider a dissident in a totalitarian state who wishes to share a modified bit of software with fellow dissidents, but does not wish to reveal the identity of the modifier, or directly reveal the modifications themselves, or even possession of the program, to the government.
Requiring patent licenses to use an algorithm clearly fails these tests, unless you remembered to bring a patent lawyer to your desert island.
To give another test case, consider the “Secure Boot” issue. If you want to have a program on your PC to make sure your data has not been tampered with, you have to make sure the program itself has not been tampered with, so you have to believe that the operating system (OS) that runs the program is secure and un-tampered-with, but how do you trust the OS? The Secure Boot solution is to bake in a requirement on the hardware that only signed OSes may run on the hardware.
The Free Software Foundation continues to campaign against this. They have many reasons, but we already have two on the page here: Requiring registration with the hardware maker means it is impossible for dissidents or desert island denizens to write an operating system.
It seems like HTTPS would be an introvert’s friend. Yet I run into a great number of Web sites out there that are HTTP-no-S. It turns out that setting up encryption is really hard, and you can’t do HTTPS alone. On the part about it being hard, I invite you to work your way through Ars Technica’s guide to getting a certificate and subsequent guide to setting up a web server to use HTTPS.
An HTTPS site can not be built on a desert island network, because you need a signature from a certificate authority. A dissident is screwed, because the dissident must give identifying information to the certificate authority.
As the second Ars Technica article explained, there are ways to self-sign a certificate. The FAQ from Mozilla (PDF) points out that Firefox has a lot of good reasons for putting up scary dialogue boxes (their term) every time a user goes to a site with a self-signed certificate. If you are a dissident who can’t use a fully-signed certificate, then, you can expect Firefox will put up a “scary” warning to people who come to your site.
Much like the patent system and the Secure Boot system, an HTTPS requirement means that you have to check with a bureaucrat before you post code you wrote to the world. A kid who wants to ditch WordPress and make up his or her modern and hopefully more fun incarnation of the Caltech Divinity School now has more hurdles in the way.
If, as I argued above, introverts are attracted to geekdom more than the general population, then it follows that there is a greater density of introverts in geekdom than the general population. [Formally, given P(geek|introvert) > P(geek), one can show that P(introvert|geek) > P(introvert).]
The fact that geekdom is heavier on introverts than other fields of endeavor means that geekdom needs to care about introverts more than other fields.
We already have some important linguistic ambiguity. Is “the open source community” the full set of people interested in open source, or is it just that subset of people who are sufficiently able to overcome introversion to comment in (potentially hostile) forums? Decisions made in “the community” affect introverts and extroverts alike, but extroverts are unlikely to notice the dark matter around them. It requires an extraordinary step to stop a lively conversation among extroverts and ask who is present but hasn’t spoken loud enough to be heard.
The conversational asymmetry can be important because the archetype of the introvert I’ve described to this point, on the desert island seeking DIY wonder, doesn’t think or work like an extrovert.
Casual conversation among modern hackers has more brand names than a fashion show: “Try my project! You can clone the Docker script from GitHub and it’ll Beanstalk up an Arch instance to EC2 with SciPy/Pandas using Apache Hive to pull from Hadoop, and qGIS serving up maps using an nginx server.”
It makes sense to build using off-the-shelf tools. If you are hand-writing HTML, it just won’t look as good as the HTML assembled by somebody using a good framework that already encapsulates person-years of thought about viewports, fonts, and even color selection. By the end of it all, you’ve signed up for so many services (like Github: “Build software better, together”) that registering for an SSL certificate seems like a drop in the bucket.
I like to think I’ve mostly adapted, but most of the group hacking events I go to have at least one person who learned introverted means of assembling Lego bricks and is completely at sea in the extrovert techniques of looking through catalogs of table legs and screwing them together.
I don’t mean to make a value judgment that the group doing work via pulling-together is somehow morally superior or inferior to the ways of the self-taught introvert. It’s just the typical story of technological progress. The Wright Brothers built their own plane, in correspondence with a few other aviation enthusiasts (see this PDF paper or these PDF slides). But would you board a plane today if somebody told you it was built by two guys in their garage? When you buy hand-made plates or books or furniture, you do so because it has artisanal charm relative to the factory-made versions, but where’s the market for artisanal database back-ends?
The curtain is slowly coming down on the time when one introvert quietly writing code could build something that flies better than anything else. It’s the extroverts who are running the startup, or even the major open source code project, and the focus is less on DIY and more on pulling together stock parts.
But the Mozilla foundation’s HTTPS requirement is, to me, the real end of the DIY era. This is not a closed-source corporation, or a startup pushing its new tool, or the arrogant guy at the hackathon, but the Mozilla Foundation—“Our mission is to promote openness, innovation & opportunity on the Web”—saying that if you are building web pages using tools from your desert island, without first filling in registration forms, then you are doing it wrong. Mozilla Firefox will make increasingly active efforts to block you until you obtain the correct permissions to build modern web pages.
This statement from Mozilla describes itself as “a message to the web developer community.” The introverts on the desert island, the me of the 1990s, the kid of the present day who doesn’t like WordPress and has the energy and curiosity to try building something new, the real-world dissidents in real-world totalitarian countries, are dark matter in the background and not addressed directly in the announcement, but are affected by the announcement nonetheless.
Ben Klemens served as director of the FSF’s End Software Patents campaign, and is the lead author of Apophenia, a statistics library.
This piece was originally featured on Medium and has been reposted with permission.
Photo via mandyxclear/Flickr (CC BY ND 2.0)