Despite all the spooky stories you hear about hackers breaking into networks and computers through sophisticated attacks, most data breaches and information leaks occur as a result of social engineering attacks, or hacking scams that are based on the exploitation of human errors and weaknesses.
That is a fact that can be attested to by Hillary Clinton’s campaign chairman John Podesta, whose emails have been all over the news and social media trend charts for the past weeks after he was targeted by a phishing scam that deceived him into handing over his credentials to the attackers.
Anyone can become the victim of a phishing attack, even you. So here’s what you need to know if you want to avoid being phished and doxed like Podesta.
How phishing attacks work
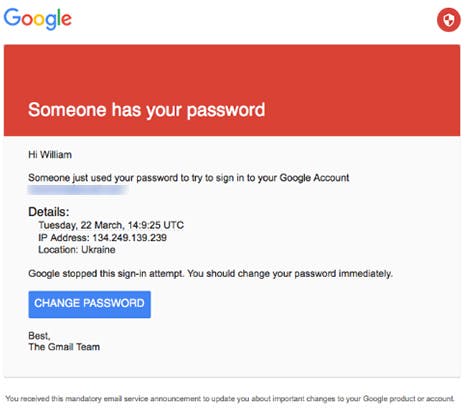
In March, Podesta received an alarming email in his Gmail account that convincingly looked like it came from Google, but was in fact sent by a group of hackers believed to be working for the Russian government. Falling for the ruse, Podesta (or another member of the Clinton staff) clicked on a link in the email, which lead to a malicious site designed to siphon his credentials to the attackers.
Of course, to his misfortune, Podesta didn’t learn about the scam until months later, when his emails started surfacing on WikiLeaks.
This is how phishing works. In layman’s terms, it is a form of fraud in which perpetrators mask themselves as a reputable entity or person and contact their victims through email, chat, or other communication channels in order to trick them into revealing information such as login credentials or access codes.
Phishing scams usually involve sending mass emails to a large number of users, containing content such as false promises of rewards or fake warnings about compromised accounts and luring the recipient to click on a link or download and open an attachment that will perform the evil deed such as installing a malware on your computer or taking you to a phony website that will steal your data.
Podesta was the target of a spear phishing attack, a more targeted version of the scam, meticulously planned and tailored with personally relevant information to improve the chances of deceiving a specific victim.
While regular phishing emails are easily discovered and blocked by most security tools and email services such as Gmail, spear phishing emails are much harder to discover and have a relatively high success rate.
How to protect yourself against phishing
The first step to protecting yourself against phishing scams is to be wary of attachments and links contained in emails—even from trusted sources—because that’s how the attacks are carried out.
Always hover over links and check the url to make sure that it’s directed to a reliable source. Don’t trust the anchor text, even if it is a URL itself—it might be a trick. For instance, the following link, https://www.dailydot.com, is actually leading to Google’s website, even if it looks like it will take you to the Daily Dot homepage. Preferably, avoid clicking on the link and go directly to the website by typing the url in the address bar.
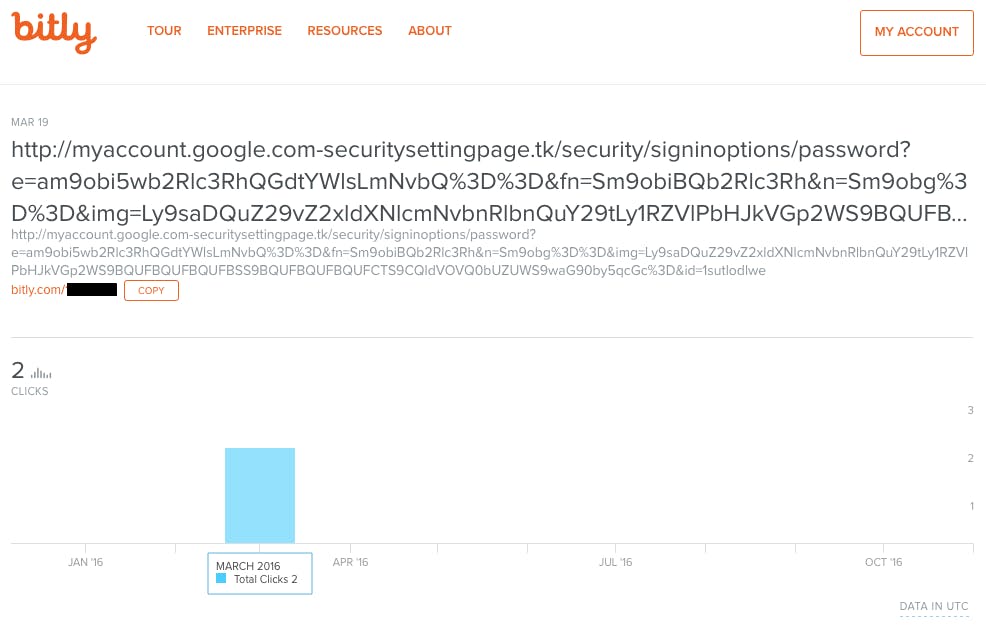
Some senders use url shorteners and link trackers like Bitly to count link clicks for analytics purposes. Attackers use the same method to conceal the destination of their links. Don’t click on shortened urls. If visiting the link is absolutely necessary, check the destination first with services such as getlinkinfo.com, which expand shortened urls and expose the content without requiring you to click on the link.
Podesta’s phishing email was using Bitly and was directed to a domain that looked like it belonged to Google, with a slight difference.
Savvy users would know that Google doesn’t need Bitly to track links, and they would easily see that the root of the domain of the url does not belong to Google. But less technical users are more likely to fall for the scam. The fact that it was coming from Google and was urging a password reset makes it hard to resist. My advice: If you receive such an email and are in doubt, never click on the link. Instead go directly to the settings page to reset your password. You’ll be safer like that.
In general, be very wary of password requests. Those are the favorite targets of phishers. Also, apply general password protection guidelines to minimize risk and potential damage in case attacks do succeed.
As for attachments, the general guideline is to not trust them and always have an antivirus software installed to scan attachments. Most email services have attachment scanning features or are able to integrate with the antimalware solution installed on your computer.
However be especially careful with file such as password-protected .RAR archives and macro-embedded Office documents. The former will bypass the email client’s virus scanning and the latter can contain malicious code that will not even be identified as malware.
Your last line of defense
No matter how prudent you are, you should always prepare yourself for the when, not the if.
The best way to protect yourself for the awful moment that your credentials do fall into the wrong hands is to setup two-factor authentication. Nowadays, most online services provide settings to protect accounts with something more than passwords, such as an associated mobile phone or a physical key. Therefore, if attackers pick up your username and password, they’ll still need that second key to access the account.
Also, consider throwing in some PGP encryption to make sure that even if hackers break into your account, they won’t be able to access sensitive communications and information.
Bottom line
Phishings scams won’t be going away anytime soon. The internet is rife with phishers, and it’ll only be a matter of time before one of them comes for you. Consider applying these tips if you don’t want to be the next John Podesta.
Ben Dickson is a software engineer and the founder of TechTalks. Follow his tweets at @bendee983