A new vulnerability found in major web browsers will make it easy for cybercriminals to carry out browser phishing attacks and lure their victims into fake, malicious websites. And even savvy users can fall for this one.
Usually, the best defense against phishing attacks is to check the address of the website you’re visiting. However, the new flaw, which appears inChrome, Firefox and Opera, shows that you can’t even trust your browser’s address bar anymore.
Xudong Zheng, the researcher who discovered the vulnerability, setup a demo page that demonstrates the attack. Although the true domain of the website is (https://xn--80ak6aa92e.com/), when you open it in your browser, what you see in the address bar is (https://www.аррӏе.com/).
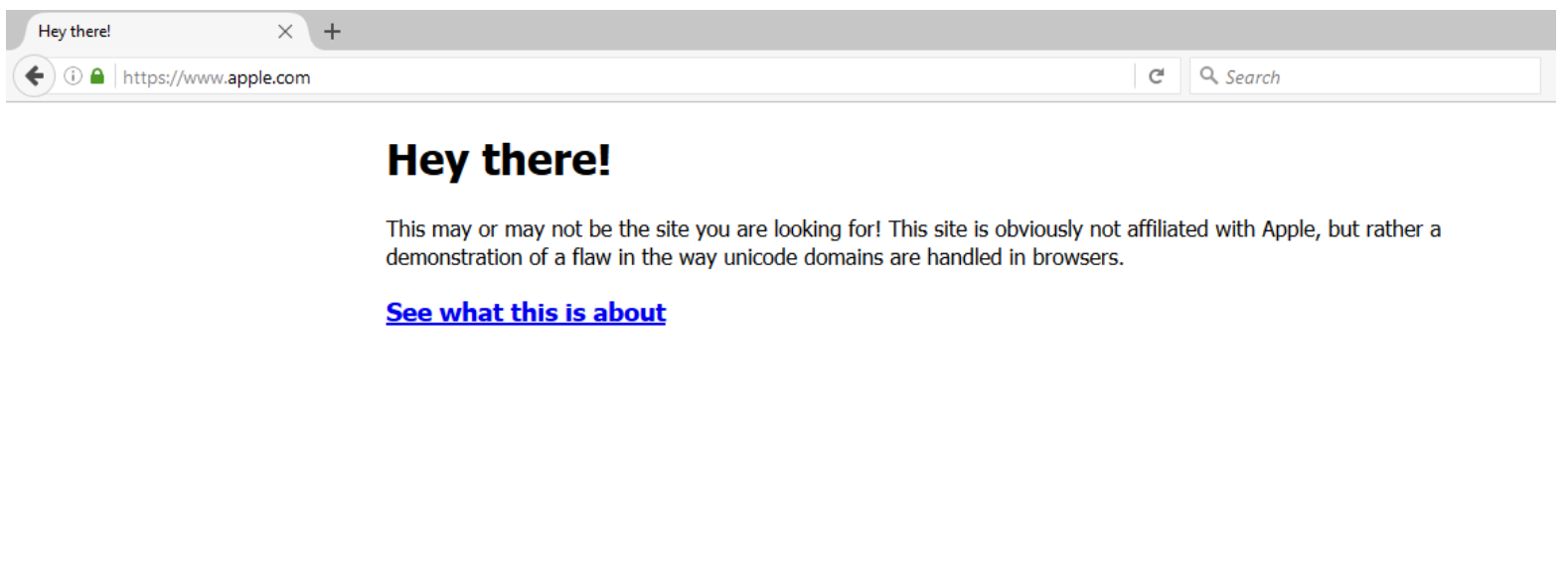
The site even sports the green padlock that confirms the authenticity of the certificate. But a look at the contents definitely shows that it’s not the genuine Apple Inc. website. Hackers can exploit the newly discovered flaw to hide their boobytrapped website behind a legitimate looking domain and lure you into giving up your banking credentials and sensitive information.
The concept behind the attack, known as “homograph attack,” has been known since 2001. It’s a kind of spoofing scheme that involves replacing ASCII characters in a website address with Unicode characters that have the same appearance. For instance, Cyrillic “а” (U+0430) and Latin “a” (U+0041) look the same but are treated differently by browsers.
To display non-ASCII characters, browsers use Punycode representation. This somewhat helps mitigate homograph attacks. Punycode transcodes host names containing Unicode characters to a subset of ASCII consisting of letters, digits, and hyphen. For instance, the Punycode representation of the Chinese domain “短.co” is “xn--s7y.co”.
However, Zheng, the researcher, has found that if all the characters constituting the domain name come from a single foreign language character set, then browsers will render them in the original language instead of using Punycode representation. That’s why his sample domain appears as the legitimate Apple website.
How to protect yourself from browser phishing attacks
If you’re running Chrome, the recent update (v 58) fixes the bug. After installing the latest version, the aforementioned test page and any other address that is fully composed of foreign characters should appear in Punycode:
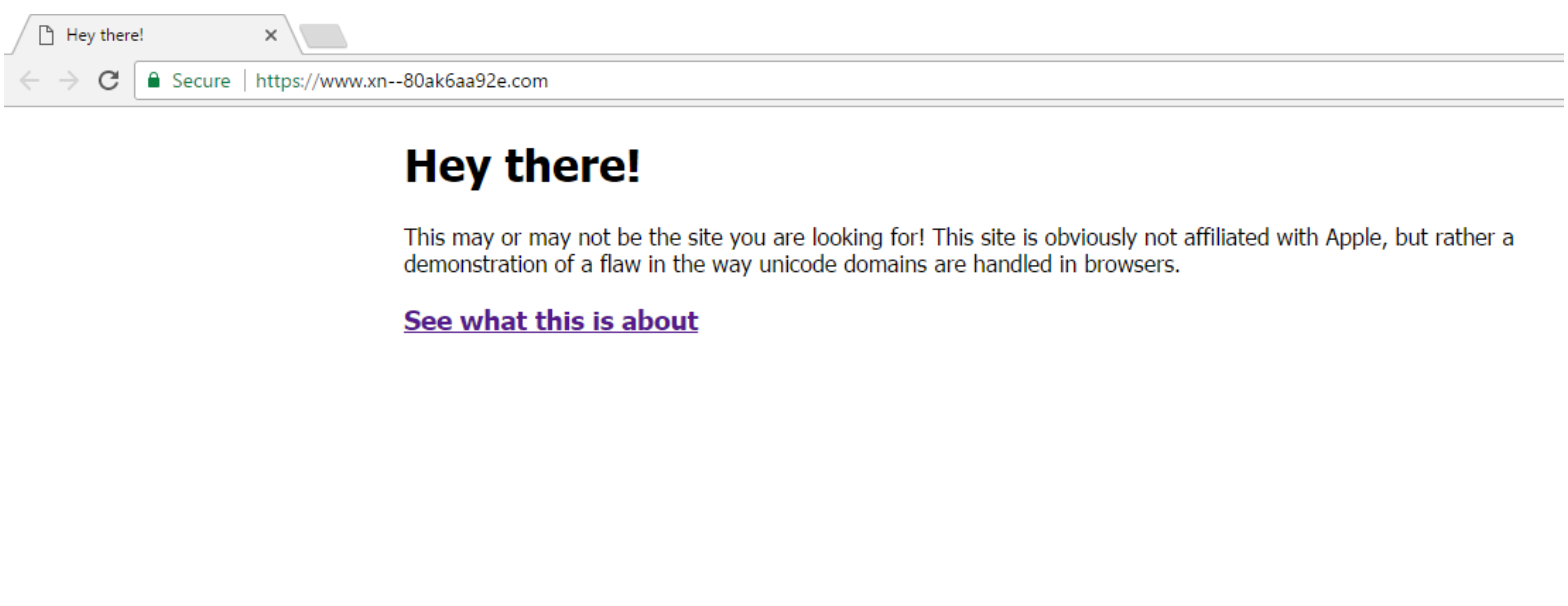
The Firefox developer community is still debating whether to apply a fix or not. In the meantime, you can tweak your browser settings to enforce Punycode under all circumstances:
- Type about:config in your browser’s address bar
- In the search box, type Punycode
- If the value of single entry titled network.IDN_show_puny_code reads false, double-click on it to change it to true
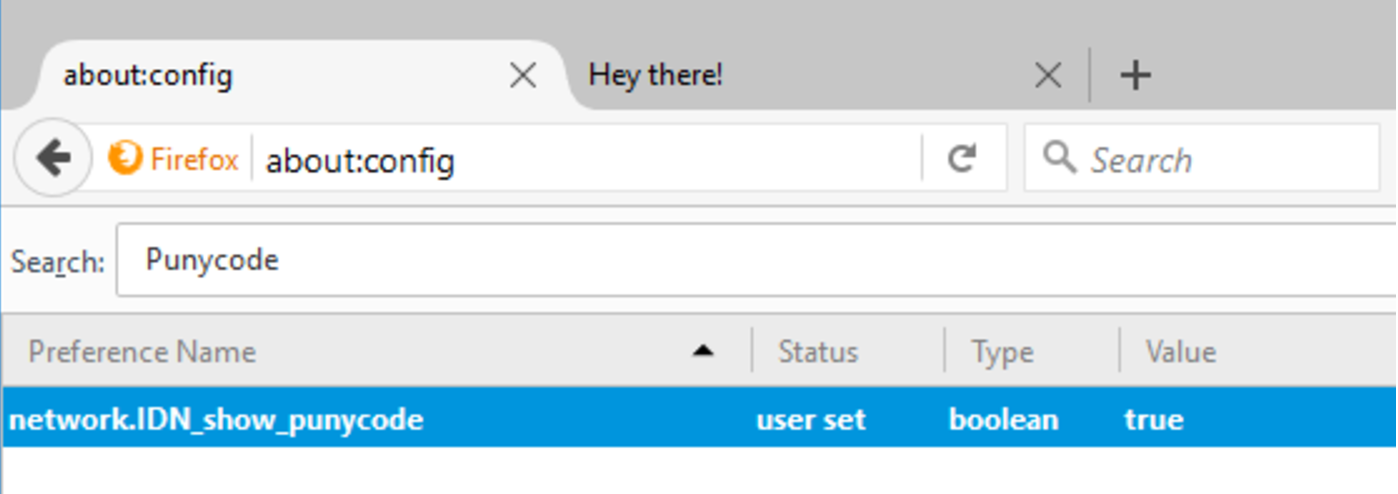
- Enter the test page address in your address bar. The Punycode representation should appear
There are other measures that can help protect you against similar attacks in other browsers. Here are two measures that can help:
- Use a password manager. Password managers don’t get fooled by phony addresses. If a fake website is using a homograph domain, the password manager will not automatically authenticate you with your stored credentials.
- When going to important websites such as Gmail, Facebook, Twitter, or your banking website, always enter the address manually or use a previously saved bookmark.
- Use two-factor authentication. This way if you accidentally fall for the trap and give away your credential without knowing, hackers won’t be able to access your account without your phone or physical key.
Ben Dickson is a software engineer and the founder of TechTalks. Follow his tweets at @bendee983 and his updates on Facebook.