From February to May, a group of Chinese hackers silently managed to breach tens of thousands of servers across the world to mine cryptocurrency, cybersecurity firm Guardicore Labs has found.
At one point, the attackers had installed cryptomining malware on some 50,000 servers belonging to organizations working in the health care, telecommunications, media, and IT sectors. Cryptominers are a strand of malware that hijack the resources of infected machines to solve complicated mathematical problems and collect cryptocurrency rewards.
The Guardicore researchers, who had been closely following the traces of the hackers for months, have released an in-depth report that reveals how they managed to breach so many servers. The firm’s findings show that the success of the hackers’ campaign hinged on using sophisticated malware deployment and protection techniques—and leveraging the ignorance of the IT administrators of the targeted organizations.
Weak passwords and unpatched systems are still a problem
According to Guardicore’s findings, the hackers operated from several servers and probed the internet for computers running MS SQL Server, a popular database server that runs on millions of Windows server machines.
But they didn’t exploit some backdoor vulnerability in SQL Server to find their way into the servers. Instead, they went in right through the front door, providing the username and password of the server’s administrator.
We’re in 2019, and still tens of thousands of servers that are protected by weak passwords. The attackers to stage brute-force attacks against the targeted servers, trying different passwords until they got the right one.
Moreover, SQL Server has specific configurations that can prevent random users from accessing the service. Apparently, the targeted organizations had also forgone applying any of those settings.
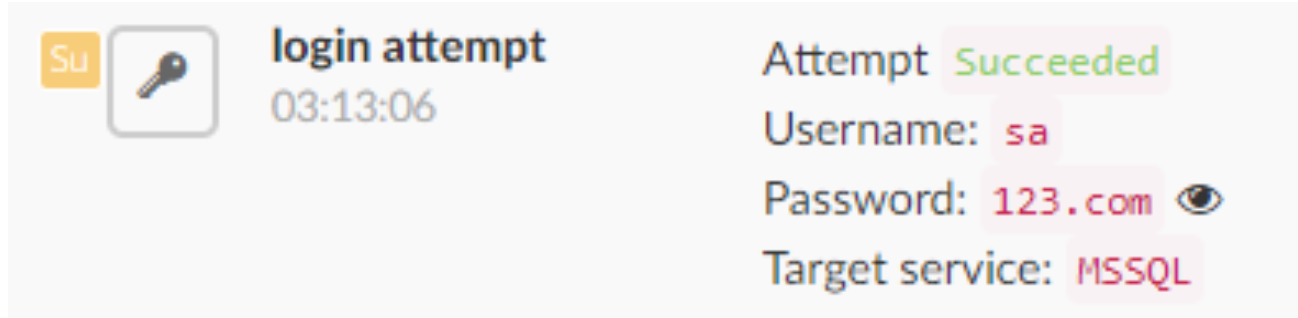
The attackers were able to target servers that had weak administrator passwords such as “123.com”
Once the attackers had access to the SQL Server administrator, they were able to run arbitrary commands at the operating system level to download and run their malicious payloads and scripts on the Windows servers.
Interestingly, the attackers exploited a vulnerability in the Windows operating system that dates back to 2014 to run their payload with SYSTEM privileges, which means the malware has access to all the resources of the server. Again, this vulnerability had been patched more than five years ago, but the targeted organizations had not bothered to update them.
This is not the first time that organizations show laxness in patching their systems. In May 2017, a group of hackers infected hundreds of thousands of Windows computers with the WannaCry ransomware by exploiting a vulnerability that had been patched months earlier.
“As recent events show, organizations rarely patch on time or even remove end of life systems,” Daniel Goldberg and Ophir Harpaz, security researchers at Guardicore Labs, said in written comments to The Daily Dot.
Why TurtleCoin?
The malware installed on the infected computers was designed to mine TurtleCoin, a lesser known cryptocurrency. Cryptocurrency networks reward miners to maintain their integrity and validate transactions. Miners are computers that compete to solve complicated equations and verify the transactions made on the cryptocurrency’s network. The miner who solves the equation faster than others takes away new cryptocurrencies released every few minutes. In most coins, more compute power results in faster calculations and greater chances of winning the mining rewards.
Miners create a “mining pools” to distribute the workload across several mining computers and perform calculations in parallel. According to Guardicore’s analysis, the attackers had split their collection of infected computers between two mining pools.
There can be a few reasons why the attackers chose TurtleCoin instead of a better-known currency such as bitcoin or ether. First, it takes a huge amount of computing resources, also called “hash power,” to compete in the market for mining mainstream cryptocurrencies, because the space is already saturated by large mining farms in China and other countries. In contrast, the mining of altcoins like TurtleCoin is much less competitive, and a miner with 50,000 servers has a great chance of getting away with a large part of the mining rewards.
Another interesting point about TurtleCoin is its privacy features. While bitcoin and ether do not directly associate addresses (the equivalent of accounts in cryptocurrency) to the identities of currency holders, they make the full list of transactions visible to the public. So anyone who knows the owner of an address will be able to track all their payments. Last year, the U.S. government sanctioned several bitcoin addresses associated with Iranian cybercriminals. This means that the owners of those addresses will find it very difficult to sell or trade their bitcoins.
According to TurtleCoin’s official website, the coin has the privacy features of Monero, a cryptocurrency that is known for making it extremely difficult to map payments to addresses. This makes it especially suitable for cybercriminals who don’t want officials to track the movement of their money.
We also don’t know how much money the hackers were able to make from the operation.
“TurtleCoin is a privacy-oriented cryptocurrency, making it extremely difficult to get an accurate and reliable count of the amount in the wallet,” the Guardicore researchers told Daily Dot.
Based on the average price of TurtleCoin between February and May (0.00012 per TRTL), the network was generating around $10,000 in mining rewards per day. There’s a likely chance that with their large network of infected computers, the hackers were able to take the lion’s share of the rewards.
Crafty hackers that made stupid mistakes
The way the campaign was designed hints at highly skilled professionals at work. One of the components the hackers used was a kernel-mode rootkit that protected the cyptominer. Rootkits are malicious programs that gain access to vital system resources while hiding their presence to other software, including antiviruses.
The rootkit developed by the Chinese hackers posed as a “device driver,” a type of software that has low-level access to the operating system and enables different software to interact with the computer’s hardware. The rootkit prevented users or antivirus software from terminating the cryptominer application.
Because of their sensitivity, drivers are subject to restrictions. Developers must get their drivers digitally signed by a credible certificate authority before they can install them on Windows machines. Newer versions of Windows only permit the installation of Microsoft-signed drivers.
The hackers had managed to sign their rootkit driver with Verisign, a leading certificate authority, under the name of a fake Chinese company. They had also scrambled the content of the driver file to make it extremely difficult for analysts to reverse engineer it and make sense of its workings.
“This shows us this driver is the work of careful professionals. This is clearly very comprehensive work, and not someone’s hobby,” said the researchers, also mentioning that the rootkit contained a thorough “version comparability” table that covered practically every build of Windows 10 until some point in 2016, including beta versions.
Verisign revoked the driver’s certificate after Guardicore notified them of the malware. While the cryptominer will continue to work without the rootkit driver, but it will be easier to deactivate it.
Ironically, the hackers had also made some dumb mistakes in configuring their attack servers, which made it easy for the Guardicore researchers to analyze their attacks. For instance, while hackers usually don’t consolidate all their resources in a single location, the cryptominers had gathered everything in one server.
“Logs, victims lists, usernames, binary files—we had them all in a mouse click. In addition, all binary files had their original timestamps; an experienced malware author would have tampered with those to complicate the analysis process,” the researchers noted in their blog post.
The researchers also noted typos in the source code of different versions of the malware, misplacing the destination address of the cryptocurrencies and possibly hampering the mining process.
“There is a contrast between the high-level tools used in the campaign and some of the mistakes made in its deployment. We’d rather not assume anything regarding separate operating teams. However, we tend to believe that this is the work of a common criminal who has access to advanced tools such as rootkits and exploits. So even if the peculiar OpSec decisions hint that this is an ‘average’ attacker, there is no doubt they had done their research,” Goldberg and Harpaz said.
Organizations should be more mindful of their security practices
In the past few years, hijacking computer resources to mine cryptocurrencies has become an attractive target for cybercriminals. With the recent spike in the prices of cryptocurrencies, there’s reason to expect increased activity in the development and distributing on cryptominers.
While hackers will go to great lengths to hide their malware, there are a few tell-tale signs that hint at a server being infected with cryptominers.
“The biggest red flag is a constantly high usage of CPU/memory even when your machine isn’t supposed to be heavily used, and of course, network traffic to mining domains. Unless you are running your own crypto-mining operation, your systems should never communicate with crypto domains,” Harpaz and Goldberg warn.
But the main takeaway from the cryptominer campaign is that while security tools continue to develop and advance, hackers will continue to bank on human errors and poor company practices.
“The basics of cyber hygiene remain correct in 2019. Maintaining secure credentials, patching systems, and monitoring them, are still the most important steps for system administrators to take. We understand it’s never as trivial as just writing it, but it doesn’t matter what ‘next gen’ protection you buy if kisadmin1 is your administrator password,” Goldberg and Harpaz recommended.
READ MORE:
- Bitfinex accused of using Tether reserves to hide $850 million loss
- John McAfee to run 2020 bid while exiled on a boat
- Why bitcoin transactions aren’t as private as you think