When we eventually get to look back on 2016, we might be tempted to label it “The Year of Leaking Voter Lists.”
The year began with many people distraught to learn that a database with voter registration records of 191 million voters had been exposed online. Voter registration lists include name, address, political party, telephone number, and whether the voter voted in the last elections and primaries. It appeared that many Americans never knew that these lists were generally considered public records.
But while they were adjusting to that piece of information, they also learned that there was a second leaking voter database with more than 56 million voter records that exposed not only voter registration data but personal information such as Christian values, bible study, and gun ownership in 19 million profiles.
Both databases had been uncovered by Chris Vickery, a security researcher at the cybersecurity firm MacKeeper. And they were both eventually secured after Chris Vickery, this reporter, and Steve Ragan of CSO began making some phone calls and trying to track down the source of the leaks.
This week, Vickery mentioned that he has uncovered yet another exposed voter list database. This one contained 154 million records and was exposed because of a misconfiguration in a CouchDB installation. Unlike the previous leaky databases that had been hosted on Amazon, this one was hosted on Google.
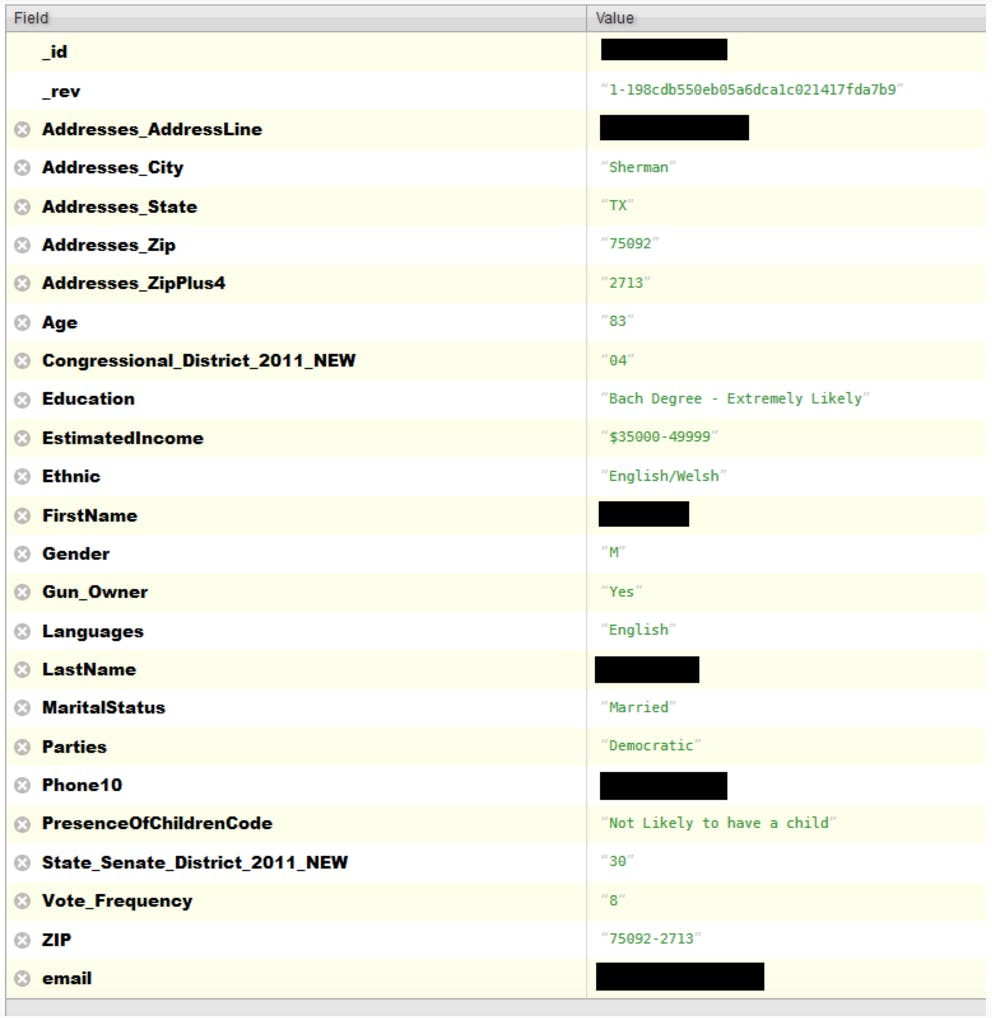
The records in this database contained a slew of personal and sensitive detail. For all individuals, the database included the following fields:
-
Addresses_AddressLine
-
Addresses_City
-
Addresses_State
-
Addresses_Zip
-
Addresses_ZipPlus4
-
Age
-
Congressional_District_2011_NEW
-
EstimatedIncome
-
Ethnic
-
FirstName
-
Gender
-
LastName
-
Parties
-
Phone10
-
State_Senate_District_2011_NEW
-
Vote_Frequency
-
ZIP
As seen in the redacted screenshot below, some entries had additional fields that included information on income, whether the individual was likely to have children, whether they owned a gun, and their ethnicity. Yet other entries had fields like “is conservative.” Vickery informs the Daily Dot that there was also a surprising amount of email addresses and Facebook profile URLs.
Who dunnit?
One of the most frustrating aspects of finding exposed databases is that there is often no indication who owns the database or whom to contact about it. In attempting to track down the owner of the database so that he could notify them of their exposure, Vickery noticed that the voter ID field was labeled “LALVOTERID.” Some Google searching him led to suspect that this might be a list somehow linked to L2, a company specializing in voter data utilization.
Vickery promptly emailed L2 to explain the situation and then spoke with them by phone. They recognized the database as likely being one of their clients’, noting that were very few clients big enough to have a national database like that and they should be able to track the source down.
Within three hours of their phone call, the database was secured. L2’s CEO Bruce Willsie confirmed that to Vickery, thanking him for finding the problem and for bringing it to L2 so that they could respond.
Noting that their unnamed national client had taken the site down quickly upon notification from L2, Willsie stated that the client told L2 that they were hacked and the firewall had been taken down. The client was now conducting their own research to determine the extent of the incursion.
“This was an old copy (from about a year ago) of the national file and it had only a very small number of our standard fields,” Willsie wrote to Vickery, adding, “I’ve asked that they report back to us with their findings and their plan for hardening their system in the future.”
Those responsible for the first two exposed databases were never identified. Although we strongly suspected we knew who the responsible parties were for each leak, Vickery, this reporter, and Steve Ragan of CSO could never get any on-the-record confirmation for either leak.
We would later learn that voter registration data similar to what was in the larger database had been up for sale on the dark web.
So another leaky database secured, thanks to MacKeeper Security Researcher Chris Vickery. But we’re 0 for 4 on learning who was responsible for leaking our personal information. And how many more leaky databases with voter information are still out there?
Everywhere you look, there’s a leaking voter list
Why does this keep happening, and what is our government doing about it? The answer to the former is linked to the answer to the latter: Our government is currently doing little to nothing, so why should entities make more effort to secure our information?
Attempts to regulate voter registration list dissemination are unlikely to succeed because political organizations and fund-raising organizations rely upon them, and their lobby makes mincemeat of any privacy lobbying efforts. No federal agency is enforcing data security in political organizations or non-profits, and so far, neither are state attorneys general.
But while Americans quickly shrug and go back to our daily lives after a bit of outraged protesting online, citizens of other countries seem to take this all much more seriously. This year:
-
Mexicans learned of two breaches of voter lists due to inadequate security by political parties. One list, held by Movimiento Ciudadano, contained data on more than 83 million voters. The second list, held by PRI, contained data on more than 2 million voters. The Mexican government has now tightened the rules about voter lists and filed criminal charges against those parties or individuals responsible for the leaks.
-
The Russian Party of People’s Freedom, PARNAS, suspended its primaries after a hacker uploaded the personal details of the candidates and all voters to their website.
-
In the Philippines, the election commission (COMELEC) was severely criticized after a faction of Anonymous hacked and dumped a database with information on 55 million Filipino voters that included passport information and fingerprints. The Filipino breach appears to be the only one in which arrests have been made so far.
-
And then there was Turkey, where 50 million citizens found their data dumped online, although some of that data appears to have been from a hack several years ago.
So, who’s next? Who knows—but it seems that it’s only a matter of time.
Dissent Doe is the pseudonym of a privacy advocate and activist who blogs about privacy issues and data security breaches on PogoWasRight.org and DataBreaches.net. Her research on breaches has fueled resources such as DataLossDB.org and InfoisBeautiful, and has served as the basis for a number of investigations by the Federal Trade Commission.