In a callback to the long-term cyberespionage campaign Red October, CrySyS and Kaspersky Lab have announced another similar find: a series of campaigns prosecuted over years by a single group through multiple campaign iterations.
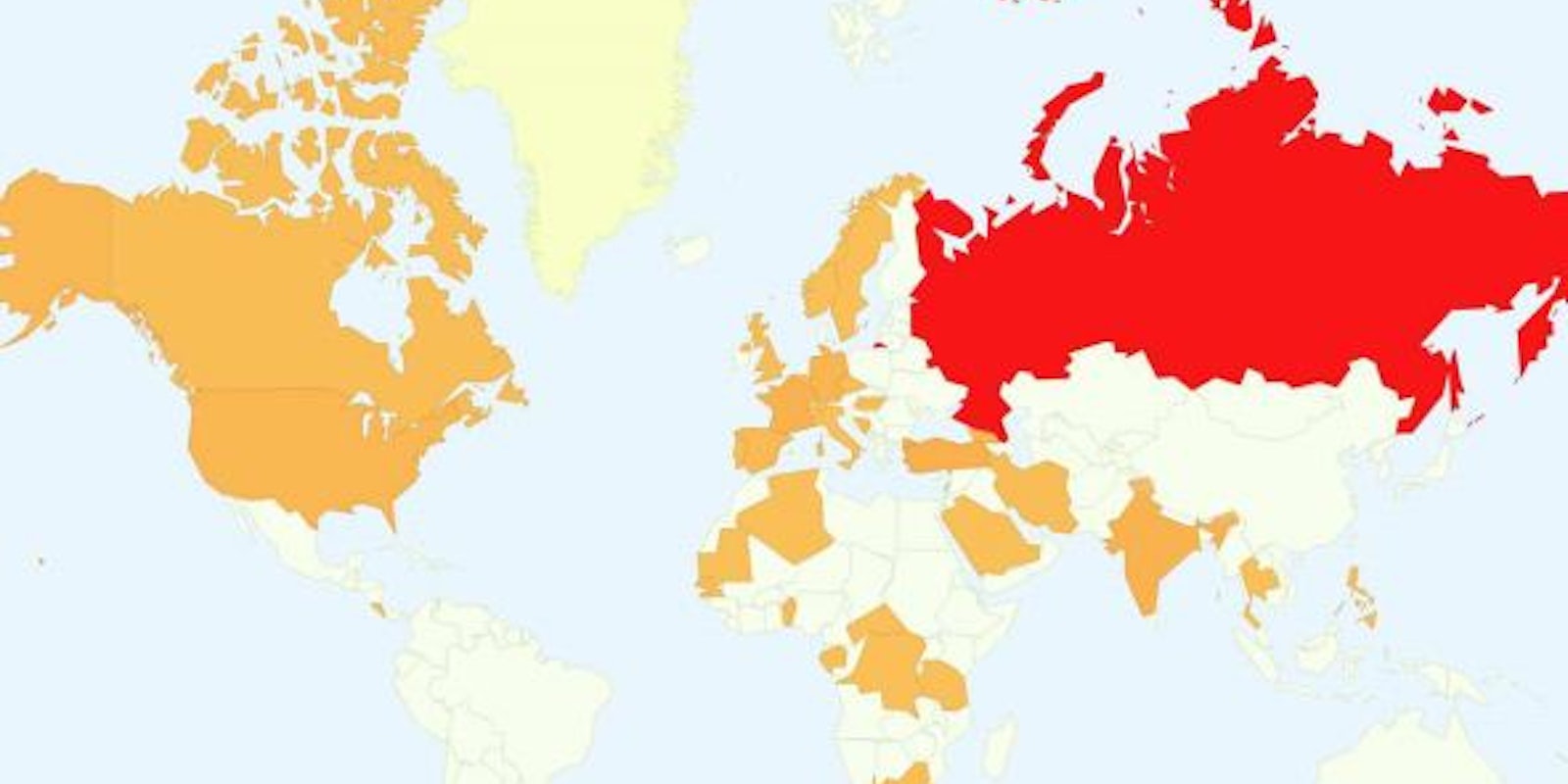
“TeamSpy,” like Red October, has been conducted over a number of years. In this case as much as a decade, twice as long as Red October. It has penetrated government and business targets in a host of countries, centered on Central and Eastern Europe but with outliers in Western Europe, the Middle East and even further afield.
The Hungary-based CrySyS team was made aware of the campaign when the Hungarian National Security Authority contacted them after a high-level Hungarian government target was hit.
Research uncovered the fact that the spies had built their attack technology on TeamViewer, a legit remote administration software. In their analysis (PDF), Kaspersky calls the TeamSpy campaign a “covert cross-nation, cyber surveillance data theft and monitoring operation” that scored hits on hundreds of victims, including many high-profile governmental and industrial targets.
TeamViewer is advertised as having over 100,000 users “spread over more than 200 countries.” (Which is somewhat odd, given most sources list the number of countries in the world as under 200.) Its penetration and legitimacy added to the utility of the program as a tool.
Kaspersky characterizes the hack as “clever” though “lazy.” Not a technically demanding campaign overall, it was, nevertheless, effective.
The presence of multiple instance of Russian in the code indicate the attackers are possibly from the Commonwealth of Independent States, the inheritor of the old Soviet Union; as does the embedded “1251” instruction in that code that is necessary to adapt to Cyrillic characters. There are also similarities to “Teambot/Sheldor,” a cyber crime campaign that targeted banks, which also used TeamViewer.
The dissemination of the virus that launches the attacks is carried out via multiple “watering hole” attacks, wherein sites the victim may use are seeded with redirections to sites that download the virus to the visitor.
The infected TeamViewer, according to CrySyS’s technical report (PDF), is used “to directly command the victim computer; to investigate screen captures in real-time.” The command and control (C&C) servers “maintain a list of the TeamViewer ID and password of victim computers and also to monitor the availability, to check which victims can be controlled currently.”
The campaign could have started as long as a decade ago, given the registration dates of its primary C&Cs. However, it has clearly been running in its present configuration, and on Russian hosts, for the past three years. In the last six to nine months it has shown a pronounced uptick in activity.
Large-scale hacking campaigns can sometimes smudge the line between criminal and governmental. TeamSpy is a large-scale campaign set with a high time investment, so it is more likely to fall (at least fall further) on the cyber espionage side of that line.
H/T Ars Technica | Image via CrySyS (PDF)