At a conference Tuesday morning, Symantec revealed that the Stuxnet virus, which had been used to target Iranian nuclear facilities, actually dated back to 2005. It’s five years older than previously believed, and could have been used to precipitate an explosion at a nuclear plant.
At the RSA Conference, Symantec’s Francis de Souza told attendees in his keynote address that Stuxnet Version 0.5 was in existence as early as 2005 and that its mechanism differed greatly from the one uncovered in 2010.
The 2010 version of the virus, believed to have been created by the United States and Israel, was delivered to Iranian nuclear facilities via seeded USB drives by June of that year. It was designed to throw off the speed of centrifuges, making it impossible to create enriched uranium, central to the creation of nuclear weapons, and delaying the Iranian nuclear program.
Symantec’s new research indicates the earliest version was designed in such a way that it could be used to create a malfunction in a nuclear plant’s centrifuge gas valves, increasing internal pressure by as much as five times and resulting in debilitating physical damage.
In a blog post, Symantec explained how the earlier version worked.
After painstaking analysis, we can now confirm that the 417 PLC device attack code modifies the state of the valves used to feed UF6 (uranium hexafluoride gas) into the uranium enrichment centrifuges. The attack essentially closes the valves causing disruption to the flow and possibly destruction of the centrifuges and related systems.
When “hex,” as the gas is known, escapes confinement, either as a solid or a gas, and reacts with water, including vapor in the air, it produces highly corrosive compounds. These compounds are poisonous in themselves but can also destroy adjacent elements of the mechanism in which they were housed. The idea that such an event would precipitate an explosion or large-scale release of material seems unlikely, though it also seems conceivable. With a uranium base, hex is in itself, of course, also radioactive.
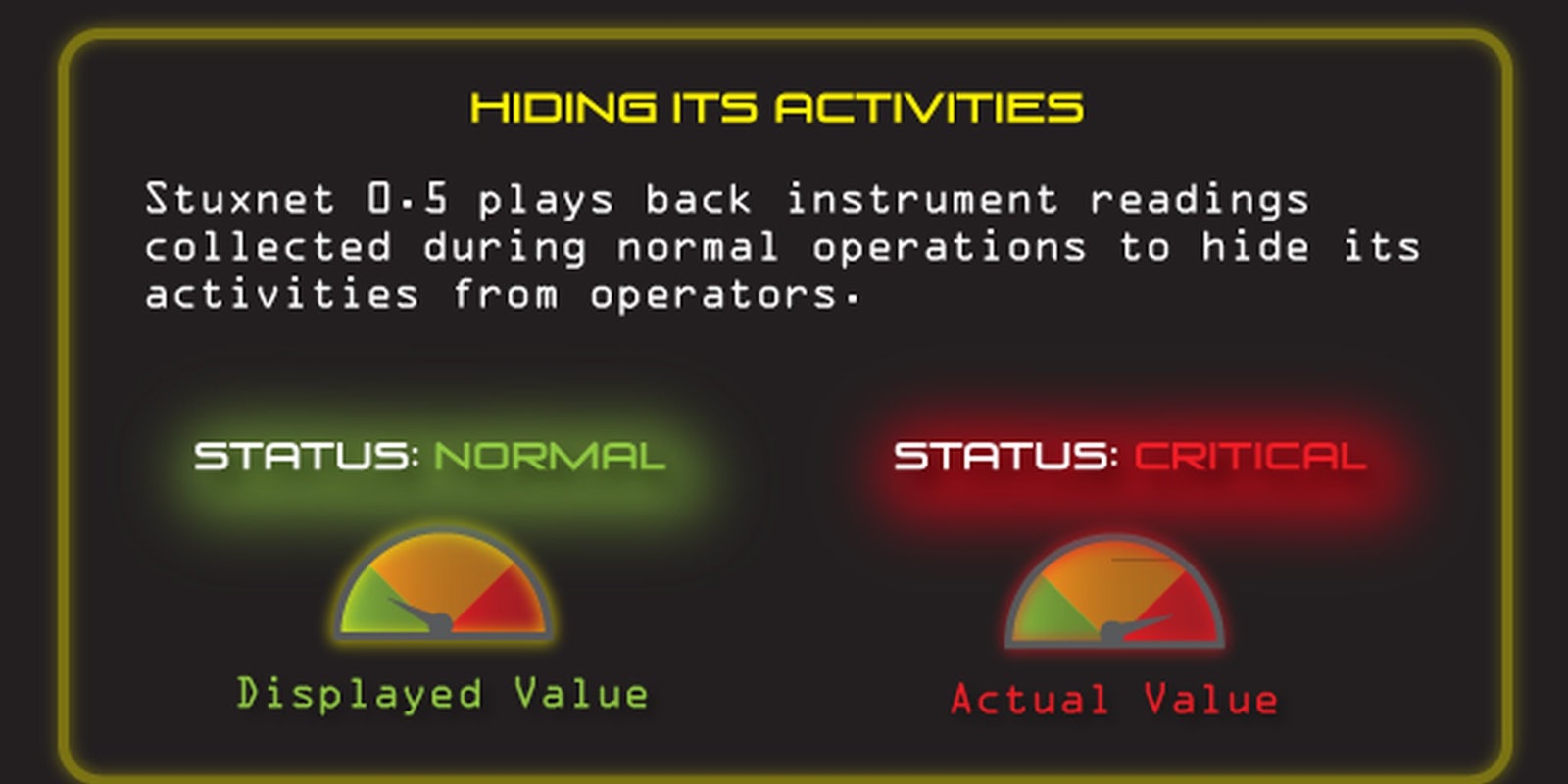
The code also captured “snapshots” of the system during normal operation and replayed it as an attack was going on to camouflage it.
“It will also prevent modification to the valve states in case the operator tries to change any settings during the course of an attack cycle,” they wrote.
The code was written in such a way as to specifically target the nuclear facilities in Narantz, Iran, the same that were targeted by the later version.
The command and control (C&C) server was registered in November of 2005 and submitted to a malware scanning service two years later. Stuxnet Version 0.5 was “designed to stop infecting computers by June of 2009 and discontinued contact with its C&C server by January of that year.”
Unlike the later version, which infected via a Microsoft vulnerability, Version 0.5 only spread via Siemens Step 7 project files,
Graphic via Symantec Blog