The Ashley Madison hack is real—and it’s worse than almost anyone imagined.
The hackers, known only as Impact Team, dumped a 10GB file online Tuesday night that’s chock-full of sensitive corporate and customer data pilfered from the servers of Ashley Madison parent company Avid Life Media (ALM).
In addition to data on more than 30 million accounts, the hackers were able to export a wide range of internal company documents—evidence that the hackers had access to far more than just user databases.
More than 33 million accounts and 36 million email addresses were included in the cache, making it one of the largest leaks of customer data in history.
At this point, the document trove has been available online for roughly a day and has circulated widely across the Internet. While many of the documents appear fairly innocuous (such as a 35-page list of domains owned by ALM and an office blueprint), others were obviously never intended for public dissemination.
The repercussions for ALM, a company that advertises itself as a “discreet” and its clients “anonymous,” will likely be significant. The targets of such leaks are not always viewed as victims, particularly if the company or organization is negligent in protecting its data. Smaller leaks in the past have resulted in class-action lawsuits against the attacked organizations.
In 2012, for example, the Texas-based intelligence firm Stratfor settled with its customers for $1.75 million after Anonymous hackers leaked their private information. An internal investigation by Verizon business discovered serious security flaws throughout the company’s systems. And just last month, U.S. government employees filed a $1 billion lawsuit against the Office of Personal Management (OPM) because the agency failed to stop a cyberattack that compromised the personal information of tens of millions of federal workers.
In addition to the personal information of ALM’s customers, numerous internal company documents have been published online, detailing everything from the structure of ALM’s computer network to the company’s PayPal account passwords.
User data
More than 33 million accounts and 36 million email addresses were included in the cache, making it one of the largest leaks of customer data in history. The leak also contains the names, street addresses, email addresses, phone numbers, and credit card transactions of roughly 33 million accounts—tasty material for blackmailers and identity thieves.
Included in the user lists are more than 15,000 email addresses from either .gov or .mil domains, meaning they are registered to the U.S. government or a branch of the U.S. military. Because users could sign up for Ashley Madison without a verified email address, it’s possible—even likely—that some of those accounts were not actually registered by public servants or military personnel.
Major stockholders
An internal document lists ALM’s major stockholders. In addition to Ashley Madison, the company owns several other hookup sites, including CouglarLife.com and EstablishedMen.com. At over 5 million shares, Jason DeZwirek owns the largest portion of the pie, according to the document.
According to CrunchBase, DeZwirek was the founder, chairman, and CEO of Kaboose, Inc., “the largest independent family focused online media company in the world.” The company was sold to Disney and Barclays Private Equity in 2009. DeZwirek is the current director of CECO Environmental Corp, a Cincinnati-based environmental company founded in 1966.
DeZwirek’s father, Phillip DeZwirek, also owns stock in Ashley Madison, according to the document. The elder DeZwirek was CECO’s chief executive for over 30 years. In 2013, he paid out $1.5 million in penalties to the U.S. Securities and Exchange Commission to resolve insider-trading charges. He offered no admission of guilt, however.
Noel Biderman, ALM’s CEO, is listed as the third largest shareholder at 3.5 million shares. A promissory note included in the cache shows that Biderman borrowed $3.9 million from ALM to purchase his shares.
Areas of Concern
A two-page Word document included in the cache lays out a number of potential attack and data-loss scenarios. Such Areas of Concern documents are common for companies to have and is likely not entirely unique to Ashley Madison. The document shows that Ashley Madison was at least concerned about the fact that its customer information might at some point be compromised.
The company also appeared concerned about compromising its PCI compliance, the standard industry requirements to ensure the safe storage and transmission of payment information.
It is unclear from the documents included in the leak what steps ALM took to mitigate these risks.
Company Overview
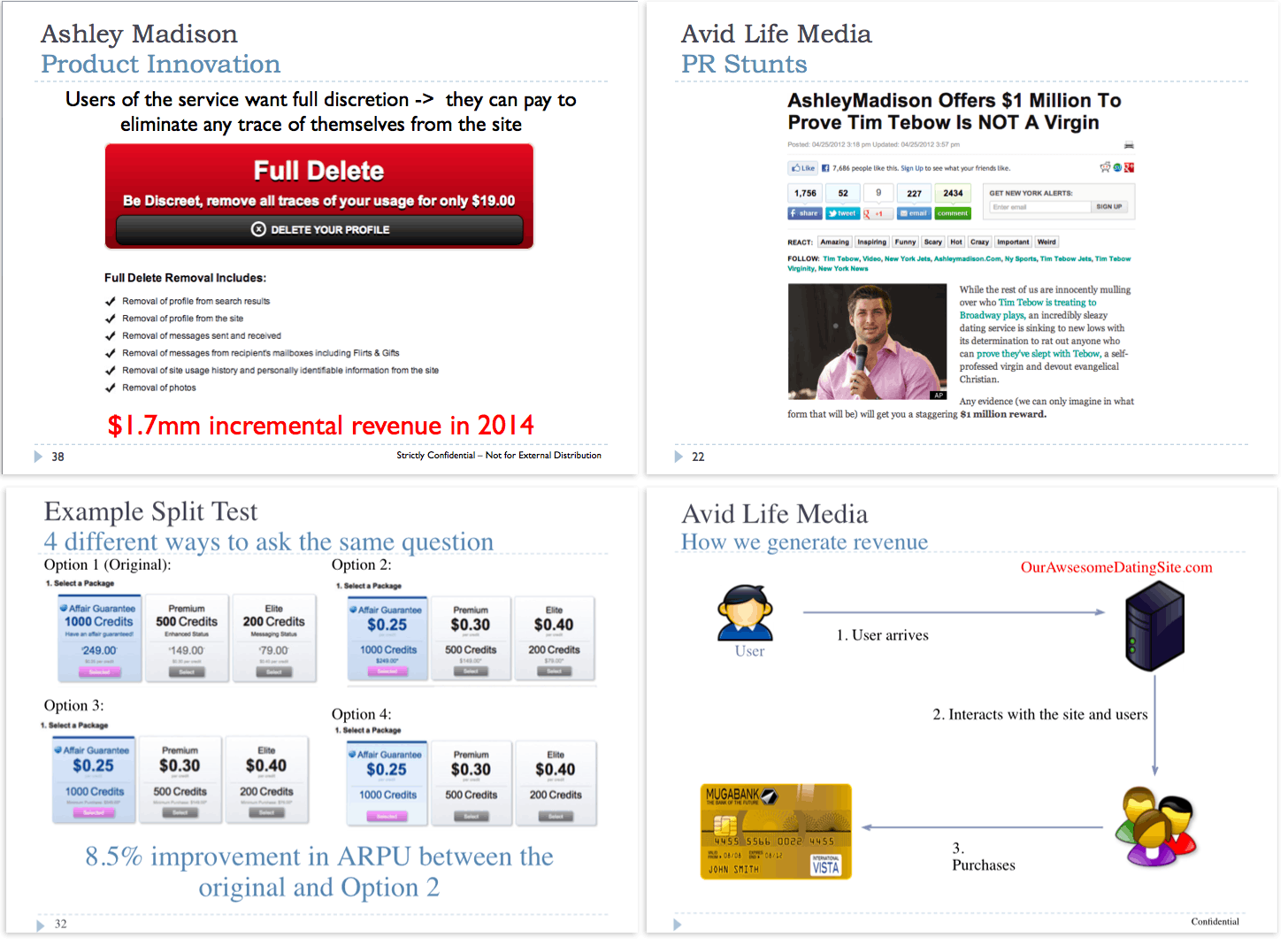
An PDF titled Company Overview and dated January 2015 is marked “Strictly Confidential—Not for External Distribution.” The slideshow provides a look at ALM’s various brands and a breakdown of their revenue, metric summaries for each website, and a look at various public-relations campaigns, or “PR Stunts,” as the document calls them.
One slide (top left) discusses the “Product Innovation” of charging users to delete their profiles from the Ashley Madison. “Users of the service want full discretion,” it says. “They can pay to eliminate any trace of themselves from the site.”
PayPal accounts
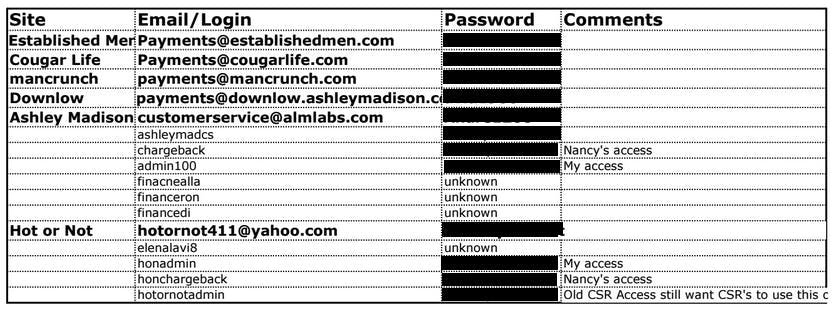
Illustrating what a nightmare scenario this is for ALM, one of the leaked documents allegedly contains a list of corporate PayPal accounts. This data would have given the hackers who stole the documents access to these accounts for at least a month. Now, the login information is available to the whole world.
Technology stack
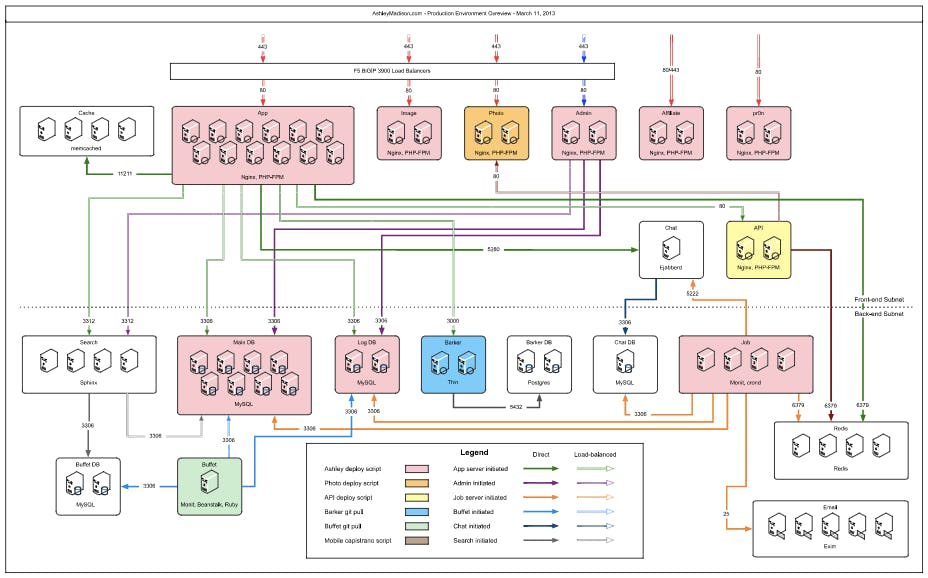
One PDF document contains a list of various technologies used by Ashley Madison as well as a visual representation of its product environment.
One section notes: “The porn affiliates that are associated with Ashley Madison used to set off Google’s adult content warning. This used to lead to the site being removed from searches. … As such, another server was set up to host the affiliates that contain adult content. The URL for this site is ashleyrnadison.com.” (This site is NSFW.)
The document, which is 22 pages long, goes on to describe in great detail the various servers, software, and database management systems ALM uses.
In short, the hackers found a roadmap for the site’s systems.
Illustration by Max Fleishman