For 655,000 patients who were enjoying a quiet Sunday, life may become a lot more complicated. Their personal, medical, and insurance information is up for sale in a forum on the dark net.
Early on Sunday, “TheDarkOverlord” listed three databases for sale on TheRealDeal market. None of the victim entities from which the databases were stolen were named, but the database descriptions included geographic area.
The first database was listed as a “Healthcare Database (48,000 Patients) from Farmington, Missouri, United States.” Priced at about $100,000, the database contains patient information including first and last name; middle initial; postal address; Social Security number; date of birth; gender; marital status; email address; and home, work, and cellphone numbers. The Daily Dot was able to obtain a small sample of unredacted data from this database. Some of the data, such as addresses and phone numbers, were found to be out of date when we attempted to verify the data, but we were able to verify some of it.
The second database was described as “(210,000 Patients) from Central/Midwest United States.” The seller comments, “it was retrieved from a severely misconfigured network using readily available plaintext usernames and passwords.”
Priced at $200,000, this database includes Social Security numbers, first and last names, middle initial, gender, date of birth, and postal address.
The third database was described as “Healthcare Database (397,000 Patients) from Atlanta, Georgia, United States:”
This product is a very large database in plaintext from a healthcare organization in the state of Georgia. It was retrieved from an accessible internal network using readily available plaintext usernames and passwords.
Priced at $400,000, this database contains a lot more fields, including primary and secondary health insurance and policy numbers, in the following format:
/PrimaryHealthInsType, / PrimaryHealthInsCo,/ PRIMINSPOLICYID, / PRIMINSGROUPID, / SecondaryHealthInsType,/SecondaryHealthInsCo, / SECONDARYINSPOLICYID, / SECONDARYINSGROUPID,/ Address1, / Address2,/ Age, / DOB, / CellPhone, / City, / Email,FNameCaps, / MI,LNameCaps, / NamePrefix, / Phone, / WorkPhone, / Sex, / SSNO, / State, / Zip
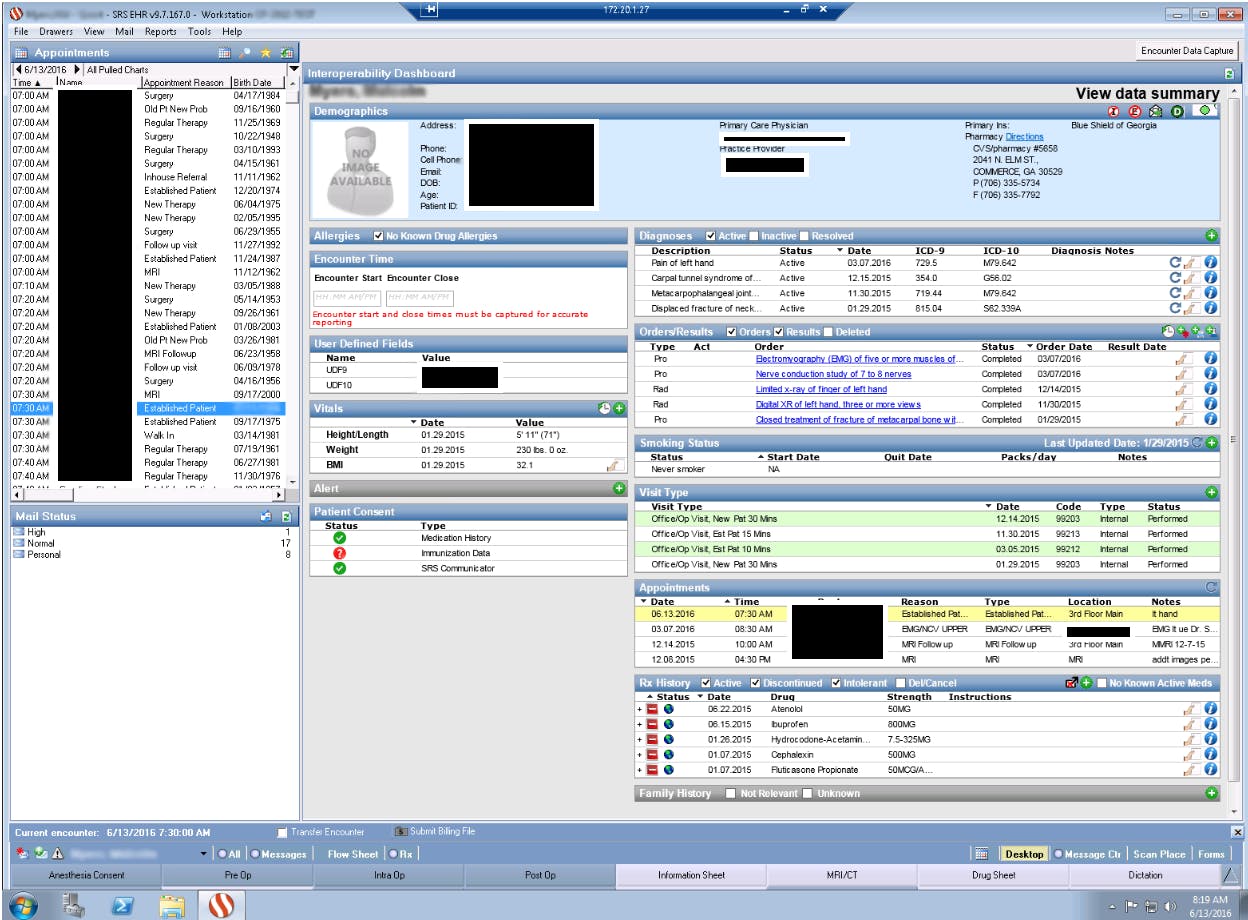
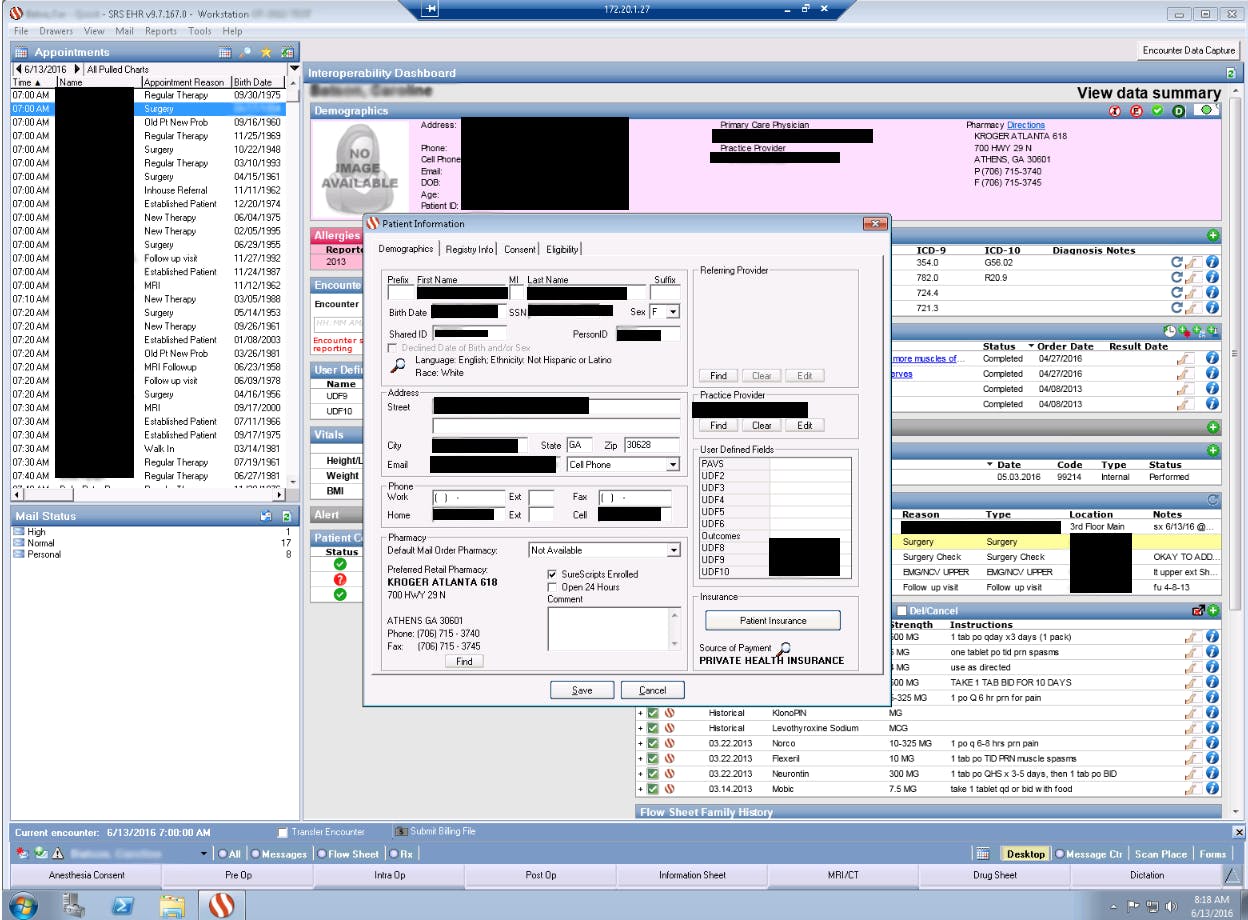
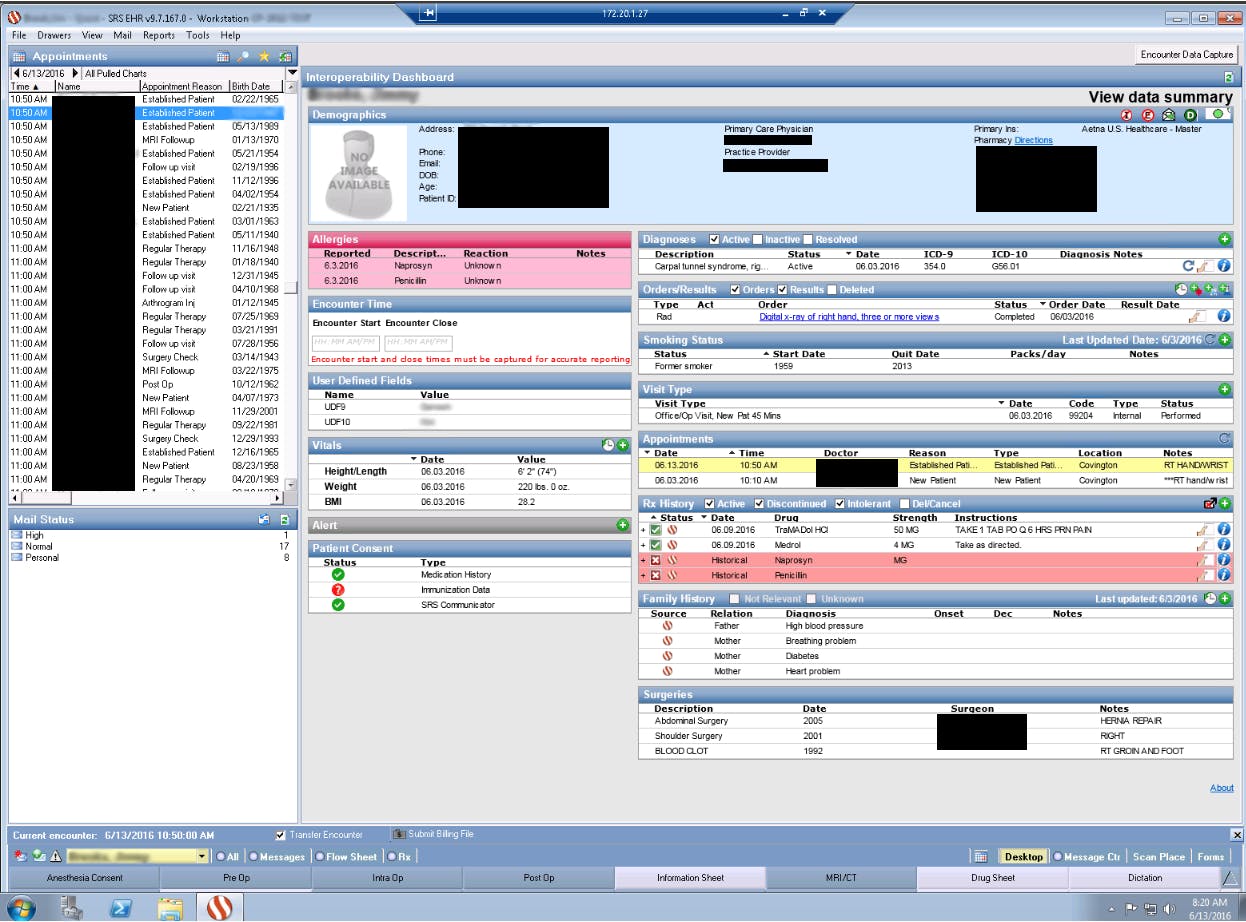
Those fields don’t tell the whole story, though, about what data the hacker has acquired, as the hacker is in possession of patients’ sensitive medical information as well. According to TheDarkOverlord, the Atlanta entity uses SRS EHR v. 9 software, which, he told the Daily Dot, is very vulnerable. (The Daily Dot is unaware of TheDarkOverlord’s gender and whether there is more than one hacker involved. This article uses the pronoun “he” merely for the sake of simplicity and clarity.)
“I found several exploits to remotely access the SRSSQL servers,” he claimed in a private chat. “It was like stealing candy from a baby.”
All versions of SRS are vulnerable, he claims. “I suggest anyone using an SRS EHR cease activity of it immediately. I have already plundered as many as I could find since I discovered the vulnerability,” he said.
The following screenshots, provided by the TheDarkOverlord to the Daily Dot, give a sense of how much information on any one patient has been stolen. Identifying information was first redacted by the hacker or hackers.
The Daily Dot has reached out to one entity in the Atlanta area that may be the victim entity and have asked them to confirm whether they have suffered a breach. This story will be updated if and when we get a response.
In the marketplace, TheDarkOverlord claims he is attempting to sell only one copy of each database:
Ownership of this database will be exclusive and only a single copy will be sold. This has not been leaked anywhere and it has not yet been abused. If you are interested in purchasing this database and would like to make an offer other than what is listed, send a PM. Only serious offers will be entertained.
Extortion attempt failed
The offer for sale appears to be the result of the victim entities refusing to pay extortion demands. TheDarkOverlord asked DeepDotWeb to add this note to their reporting on the situation:
Next time an adversary comes to you and offers you an opportunity to cover this up and make it go away for a small fee to prevent the leak, take the offer. There is a lot more to come.
In a chat with TheDarkOverlord, he readily acknowledged that he has sought money from the entities. He would not be specific as to how much he had demanded in all cases (other than to say that it was less than $1 million), except in the case of the Farmington victim, where he indicated that he had sought 250 bitcoins, or about $160,000 at current exchange rates. The Farmington victim has until July 8 to pay up or the entire database will be leaked, he says.
When asked for how long he has had access to the Farmington system, TheDarkOverlord told the Daily Dot:
I have had access to his system since early 2016. I only started getting aggressive with data collection recently in May and he only knew of my access once I sent him the ransom email.
They use a microsoft Access database – an EHR system called MedTech.Storing plaintext username and passwords
All unencrypted
Everything
Under the federal law known as HIPAA, entities are not required to deploy encryption, but they are required to have technical safeguards in place.
“If the entities pay up, the patient data is not exposed,” TheDarkOverlord told the Daily Dot. “I delete everything I have once a victim pays. I also supply a report regarding the results and the documentation of my attack. A little token of gratitude and support.”
As to the vulnerabilities he has found and used, including a 0-day Remote Desktop Protocol (RDP), TheDarkOverlord has no intention of ever selling those.
“I keep all my exploits private for my own use,” he said. “Never publish it. Perhaps some of the victims know from the reports once they pay.”
So how many databases are they currently sitting on? “A number that is large and sad” was TheDarkOverlord’s answer.
Because the Daily Dot has yet to see proof of some of the claims TheDarkOverlord made with respect to other entities, we are not publishing their names.
As the government has pushed providers into greater use of EMR and interoperability, one can only ponder what TheDarkOverlord also told this reporter during our chat:
“Networking is the downfall of most of my targets.”
Dissent Doe is the pseudonym of a privacy advocate and activist who blogs about privacy issues and data security breaches PogoWasRight.org and DataBreaches.net. Her research on breaches has fueled resources such asDataLossDB.org and InfoisBeautiful, and has served as the basis for a number of investigations by the Federal Trade Commission.