The hacker who claimed to have breached Pornhub’s systems has taken aim at a new target.
Fidelity National Information Services, Inc. (FIS Global) is a leading provider of technology for the financial services industry. According to its website, FIS, a Fortune 500 company, serves more than 20,000 clients in over 130 countries and employs more than 55,000 people worldwide.
How many it employs in information security is not clear, but it might want to add a few more in light of a breach involving client information it allegedly suffered last week—one the firm was allegedly warned about but never publicly acknowledged.
A vulnerability in client portal?
The hacker, 1×0123, identifies himself as an “underground researcher.” According to statements previously made to the Daily Dot and other media outlets, he forgoes bug bounty programs but is generally seeking money—either from the vulnerable firm or from those who would buy information about the vulnerability to exploit for their own purposes. Last month, 1×0123 claimed to have hacked Pornhub and to have sold the information to three others before Pornhub patched the vulnerability. Pornhub denied that it had been hacked.
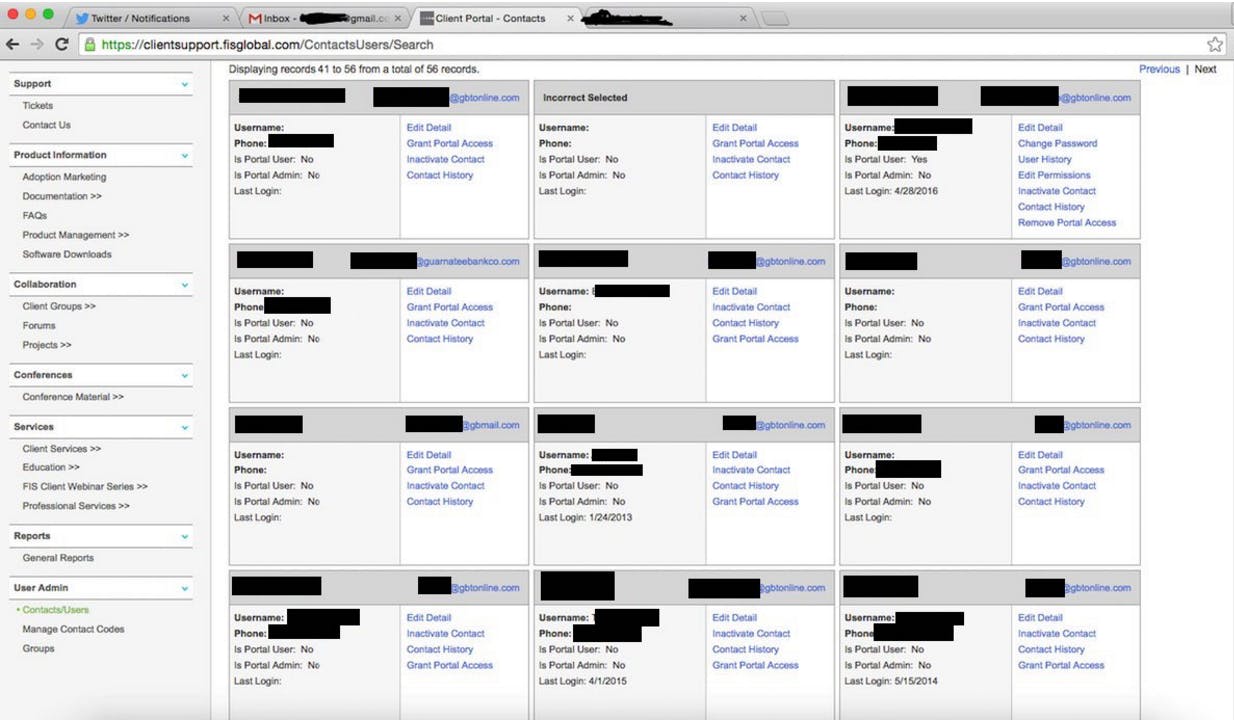
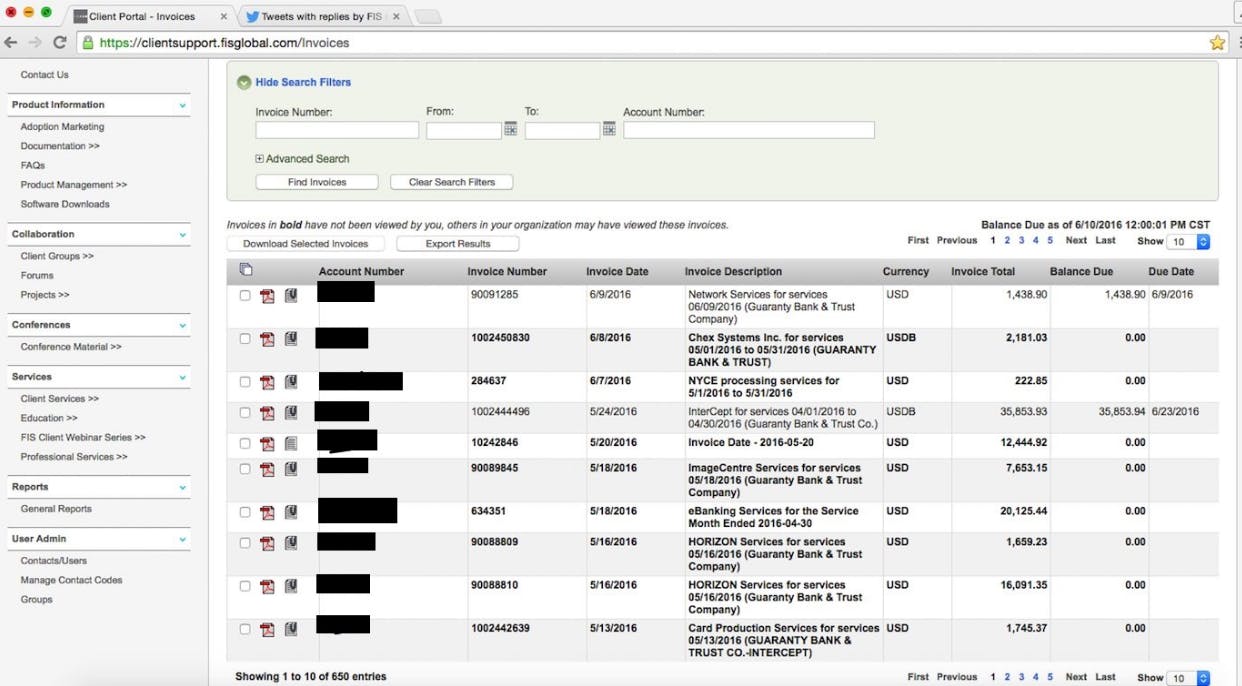
Last week, 1×0123 claimed to have accessed FIS Global’s client portal. He posted one unredacted screenshot from a Client Contacts screen and one screenshot from Client Invoices with billings to Guaranty Bank and Trust Company. Both screenshots have been redacted by the Daily Dot to shield employees’ names, email addresses, phone numbers, and account numbers:
Although the @FISGlobal account did not respond to 1×0123’s tweets and his taunt that he had reset clients’ passwords, his Twitter account was locked by Twitter:
https://twitter.com/1×0123/status/742733312561717248
In private messages, 1×0123, who indicates that English is not his first language, informed the Daily Dot that “the vulnerability exists in the login portal wich (sic) allows anyone to reset passwords without knowing the old password.. i shared 2 screenshots and they reported my [Twitter] account and got me [to] delete those.”
1×0123 also provided the Daily Dot with other screenshots. One showed that he had been able to successfully reset the password of a named employee of Guaranty Bank and Trust Company. A LinkedIn search revealed that the named employee is a vice president of the bank. The Daily Dot called her to notify her of the compromise of her login and of the exposure of her bank’s data, but she did not return the call. Nor did the head of the bank’s cybersecurity department return a call from the Daily Dot to alert them that its data had been exposed on the Internet and more could be exposed.
The Daily Dot was also provided with an archive containing dozens of recent FIS invoices to Guaranty Bank and Trust Company for various services. Inspection of the invoices does not indicate that any customers’ personally identifiable information was included.
Of note, all of the screenshots and files provided to the Daily Dot involved Guaranty Bank and Trust Company, and only that one bank. Despite 1×0123’s claims that FIS’s client portal was vulnerable to password resetting, he either did not access or download data from other FIS clients, or he did not choose to share any other data with the Daily Dot.
1×0123 informs the Daily Dot that as of Tuesday night, the vulnerability was secured. But because he never received any response or acknowledgement from FIS, he stated that he intends to leak all the invoices he downloaded. Had FIS Global acknowledged his effort to alert it, he claims, he would not have taken that vindictive step.
Déjà vu all over again?
Last week’s incident was not FIS’s first breach. In 2011, it dutifully notified the Securities and Exchange Commission after hackers managed to raise or remove the daily withdrawal limits on 22 debit cards the hackers accessed from FIS’s prepaid card network. The cards were cloned and distributed to co-conspirators who, in a carefully timed attack, managed to withdraw $13 million from ATMs.
When FIS reported the incident to regulators and investors in May 2011, it indicated that the breach was limited in scope, putting approximately 7,000 cardholders’ non-public information at risk. But two years later, when the FDIC released an audit conducted in the months and year following the incident, FIS’s clients and the public learned that FIS’s security failures were much more serious than the company had realized or disclosed. As security journalist Brian Krebs reported in June 2013:
“‘The initial findings have identified many additional servers exposed by the attackers; and many more instances of the malware exploits utilized in the network intrusions of 2011, which were never properly identified or assessed,’ the FDIC examiners wrote in a report from October 2012. ‘As a result, FIS management now recognizes that the security breach events of 2011 were not just a pre-paid card fraud event, as originally maintained, but rather are that of a broader network intrusion.’”
In response to the breach and audit, FIS claimed to have invested $100 million in ramping up its security:
“Since that time, FIS has continued to strengthen its information security and risk position, including investments over two years of $100 million or more, as part of our goal to provide best-in-class information security and risk management to each of our 14,000-plus clients. We have openly and regularly communicated these initiatives, our progress and results to our clients and shareholders through meetings, monthly updates, quarterly public disclosures, Board materials, educational webinars, and more.”
But as Krebs noted,
“The FDIC found that even though FIS has hired a number of incident response firms and has spent more than $100 million responding to the 2011 breach, the company failed to enact some very basic security mechanisms. For example, the FDIC noted that FIS routinely uses blank or default passwords on numerous production systems and network devices, even though these were some of the same weaknesses that ‘contributed to the speed and ease with which attackers transgressed and exposed FIS systems during the 2011 network intrusion.’
“…. ‘The Executive Summary Scan reports from November 2012 show 18,747 network vulnerabilities and over 291 application vulnerabilities as past due,’ the report charges.”
FIS Global’s response
The Daily Dot contacted FIS Global to ask them about the claimed portal vulnerability, but they did not respond to email inquiries sent on Tuesday and Wednesday. Nor did its Twitter team respond to a request to follow so that the author could privately ask for a response or comment.
It is not known whether FIS ever contacted its client or clients to alert them that their data had been downloaded and was being exposed online.
Dissent Doe is the pseudonym of a privacy advocate who reports on privacy issues and data security breaches on PogoWasRight.org and DataBreaches.net. Her research on breaches has fueled resources such as DataLossDB.org and InfoisBeautiful, and it has served as the basis for a number of investigations by the Federal Trade Commission.