A new virus is infecting smartphones around the world, and it’s managing to extract hundreds of dollars from users with a nefarious combination of technical trickery, social engineering, and the near-universal fear of getting busted for downloading porn.
The virus is called Android-Trojan.Koler.A and functions by disabling nearly all functions of the device and then displaying the following message:
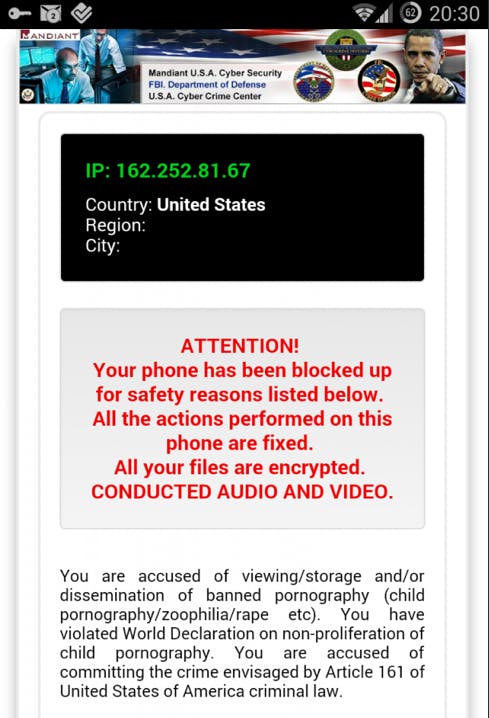
Screengrabs via Bitdefender
The virus takes advantage of the smartphone’s geolocation function to display county-appropriate warning messages.
For example, infected devises in the United States tell users they have broken U.S. law, and infected devices in the United Kingdom tell users they have broken U.K. law.
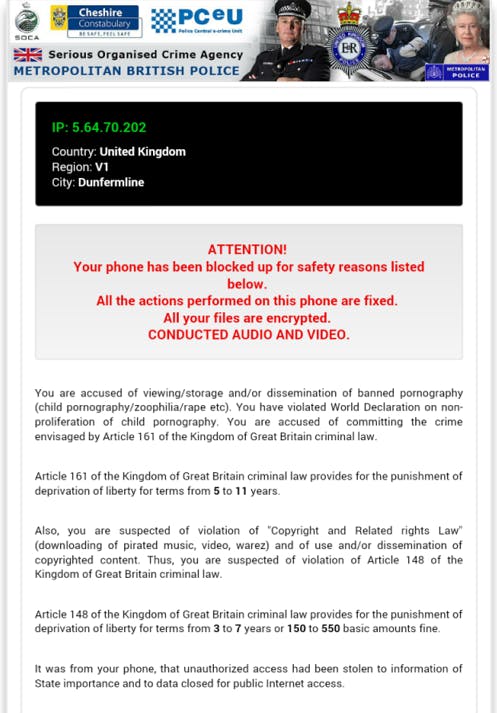
The ultimate goal of the hackers behind the virus is to extract money from victims, which is done by saying they need to pay a $300 fine using untraceable payment mechanisms like Paysafecard or MoneyPak unlock the device.
What makes Android-Trojan.Koler.A so nefarious, is that, in order get it in the first place, users need to have looked at porn on their smartphones—lending an air of believability to the virus’s claims of being the work of a government law enforcement organization. Users get infected with the virus after visiting one of a handful of porn sites on an Android phone. Upon visiting the sites on a smartphone, a message will pop up informing the user that they need to download a video player. However, what’s actually downloaded is a a software package containing the virus.
In order to get the malware onto a phone, the user has to allow apps to be downloaded outside of approved app stores. While app stores like the Google Play market aren’t 100-percent guaranteed to catch every virus hackers attempt to sneak through, the marketplaces employ teams of engineers tasked with ensuring the safety of the apps being sold. Any app downloaded outside of an app store environment comes with an additional level of risk.
Ars Technica reports that, in a six-hour period earlier this week, the virus claimed upwards of 68 victims in the Middle East, Europe, and the United States.
In a blog post about the malware, cybersecurity firm BitDefender speculates that the people behind the Reveton/IcePol malware distribution network are behind the virus. A server belonging to the network was seized by Romanian police last September.
This malware is reminiscent of the CryptoLocker virus that swept across the globe earlier this year. Using a similar blackmail strategy, CryptoLocker, once downloaded onto a hard drive, encrypts a wide variety of files, from Word documents to family photos, and demands the user pay $300 in Bitcoin within the next 100 hours or the key necessary to unencrypt the files will be shredded forever. Once payment is made, the hackers behind CryptoLocker would send victims the encryption key required to unlock their files.
Unlike CryptoLocker, it doesn’t appear that Android-Trojan.Koler.A actually encrypts any of the phone’s data. Instead, it just renders most applications on the device inaccessible to the user by disabling the back button within the app. The app automatically opens after a few seconds when users are on the home screen, making it extremely difficult, if not impossible, to uninstall manually.
The blog MalwareBytes instructs that the simplest way to remove the app is to boot the phone in safe mode, where the phone doesn’t load third-party applications, and then uninstall the offending program. Directions for how to start your phone in safe mode can be found here.
Photo by closari/Flickr (CC BY 2.0)


