Deciding what operating system (OS) will keep your computer running smoothly—and with the highest level of security—is a controversial yet frequent question many business owners, government officials, and ordinary Joes and Janes ask.
There are many different operating systems—the software at the base of every computer, controlling the machine’s array of functions—like Mac OS10, which comes pre-loaded on Apple laptops and desktops, and Microsoft Windows that’s on the majority of personal computers. ‘s Android and Apple’s iOS for mobile devices are designed specifically for devices with smaller touchscreens.
Whatever OS you use—and many users are very loyal to their operating system of choice and will argue that their’s is the best—it’s not entirely secure or private. Hackers are still infiltrating systems every day, and they can easily target victims with malware to spy on users and disable their operating system altogether.
Because of this, choosing a secure system is essential to staying secure online. Below are the top three secure operating systems that will help users take the next step to ensure proper cyber and hardware security.
The most secure operating system
1) Linux

Linux is an open-source operating system that has been around since the mid-1990’s and can be modified and customized to fit your security needs. The operating system is known for its great ability to let developers patch up any loopholes that hackers may be able to get through, offering a stable system that is largely free of viruses, virtually eliminating the fear of having to reinstall yearly due to a malware-caused malfunction.
The open-source nature of Linux gives users the freedom to run the software, study how it works, and customize its settings. Linux, like every other OS, is comprised of different parts to keep the operating system running. If you’ve never used Linux before, you might want to learn a few of these terms:
- The bootlander: Manages the booting process of the software, appearing as a splash screen before proceeding to the launch.
- The kernel: Manages the CPU, memory, and peripheral devices. The kernel is the core of Linux.
- Daemons: These are background services such as sound, images, and printing connections that run after booting.
- The shell: A command control that allows you to communicate with the computer itself through a text interface—but if you doesn’t know how to code, it won’t be of any use.
- Graphical server: Also refers to as the “X” system, the graphical server produces images and graphics across the OS.
- Desktop environment: Users can choose from a list of environments, like Unity, Cinnamon, KDE, and others that are pre-downloaded with browsers and extension files.
- Applications: Linux offers thousands of extra apps that are available for download in case the desktop environment does not offer it to begin with.
Linux has a family of different free versions (known as distributions, or distros) to choose from, based on users’ computer skills. If you’re just getting started, check out Mint or Ubuntu. And because Linux is open-source, users can make copies of modified systems and give them away to friends in need.
READ MORE:
- The best free password managers
- How to encrypt an iPhone in seconds
- The best free VPN to maintain your privacy online
- The best 4 antivirus tools to keep your computer adware free
2) OpenBSD
OpenBSD is another free and open-source operating system that was created by Berkeley Software Distribution at the University of California, Berkley, by a team of volunteers. The whole thing is kept afloat with donations through their own OpenBSD Foundation.
OpenBSD prides itself on portability, standardization, correctness, proactive security, and integrated cryptography. The operating system has a full-disclosure policy, meaning its developers will be completely transparent with any security flaws they find, when they occur.
OpenBSD comes with a secure minimal firewall, web server, mail server, and an optional customizable desktop. It is a minimal, secure operating system that doesn’t mess around with pleasing its users—it is uncompromising in its focus on a reliance on code for security purposes.
Because of this, OpenBSD is not for the low-skill tech users—unless you want to learn to code. However, users in the know will find the system’s five-minute installation and no-frills mission a refreshing departure from other OSes.
3) Tails
Tails—The Amnesiac Incognito Live System—is specifically designed to take up little space and erase any trace of its use across the Internet. As such, it can be downloaded to and run from an SD card or USB stick.
Tails receives about a third of its funding from the U.S. government, which originally supported the project protect whistleblowers whose identity could be in danger. But is also available for regular users who simply want to keep their identities and their data private.
The operating system anonymizes user activity through the popular Tor network, which encrypts user data and bounces their connections between different computers to protect user identity and ensure strong security. By using Tails, a user’s location will be hidden, access to otherwise unavailable content will be available, cyberattacks will be protected against, and user’s identity will most likely remain a secret.
Tails is available for use on basically any machine and can run as a temporary alternative to a computer’s main operating system. Downloading Tails is simple, but the encryption process that follows will take time—but it will be worth the wait when you’re browsing without anyone able to look over your digital shoulder.
4) Qubes OS
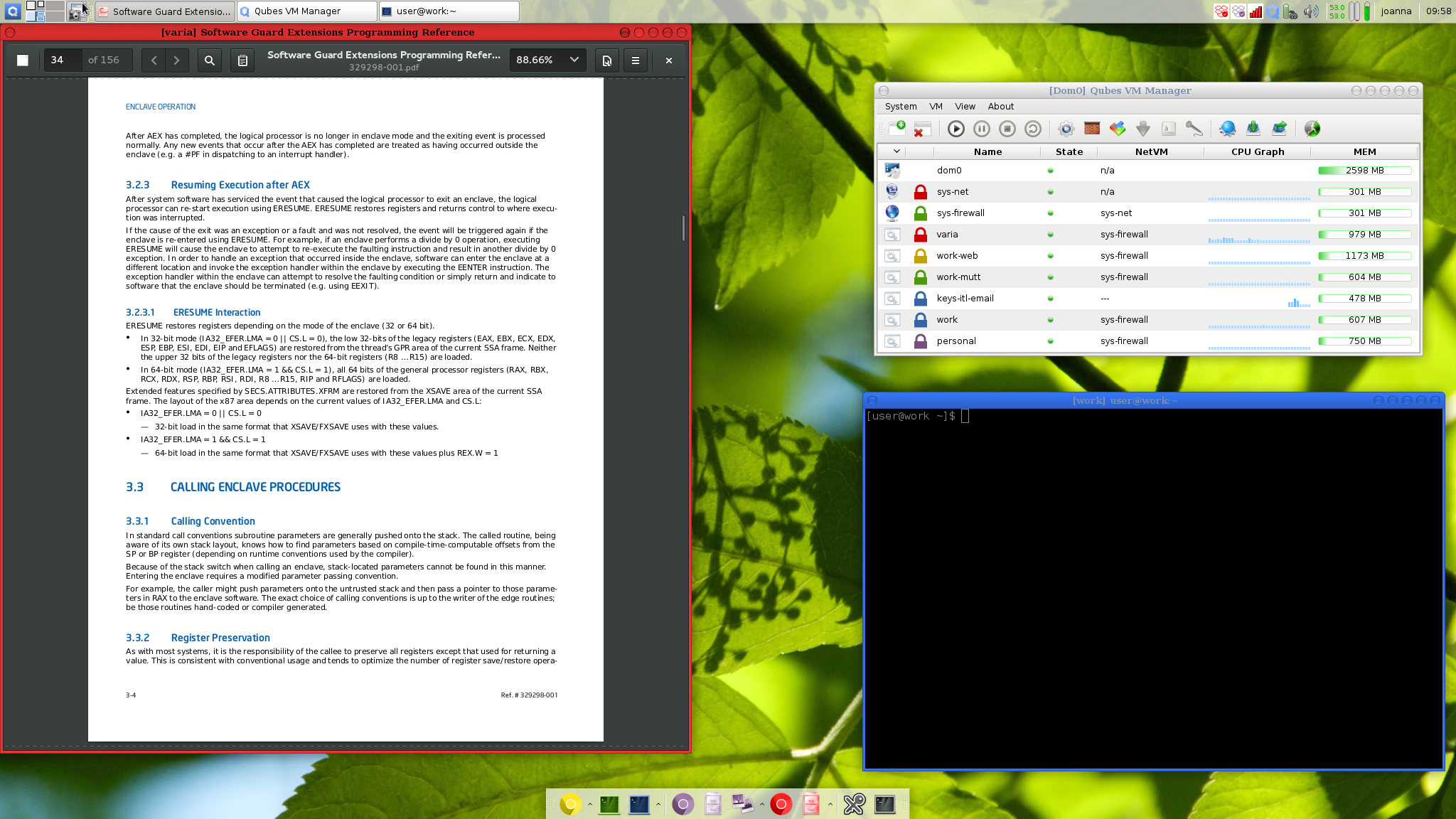
Qubes is an absurdly secure operating simple that lives by a simple—yet paranoid—assumption. It acts as if your system has already been breached and keeps everything compartmentalized to protect the system as a whole. Each program you run is created in its virtual machine, called qubes, cut off from the rest of the system. So a piece of malware opened in your email client can’t find its way into your database. It’s locked in the email browser.
The trade off of this security is a heightened difficulty level when using the os for everyday work. Unless you have a background in computers, you’ll need to do a lot of troubleshooting to get your workflow in order. Finding a computer that’s compatible with the os is another major issue, but the development team has provided links on their site to help you find one.
Everyday users may wonder why someone would need this much security, but they’re not who Qubes is intended for. According to founder Joanna Rutkowska, in an interview with Vice, “The users who need the protection offered by Qubes the most are human rights defenders—journalists, activists, civil society groups.” Qubes may have a tough learning curve, but if your security is a top priority, it’s well worth exploring. —John-Michael Bond
READ MORE:
- How to protect yourself against ransomware
- 10 reasons you need to ditch Chrome for the Opera browser
- What you really need to know about malware
- The best free antivirus tools for Windows and Mac
5) Solaris
Solaris is an operating system for administrators. While secure from the outside, Solaris gives systems administrators a window into how authorized users are using their computers. It’s a selling point in Solaris’ promotional materials, pointing out “misuse by authorized users is the primary source of security violations.” With Solaris, you have the tool to spot that misuse before it’s too late.
Admins have a broad range of security options with the system. Access to system data and resources can be limited on a user-by-user basis down to what files, programs, or utilities users can access. It can create usage reports by user, file, data, or time, and it eliminates super-user functions, requiring everyone to do their work under their own username. Even the admins are accountable for their actions as specific users.
Solaris’ security principal is called least privilege, which boils down to avoiding risk by tightly controlling the abilities and options available to each user. It’s a terrible operating system for home use unless you have some particularly annoying roommates you share a computer with. However, for a business that needs the utmost of security and privacy Solaris could be the system you’ve been waiting for. —J.M.B.
6) Whonix
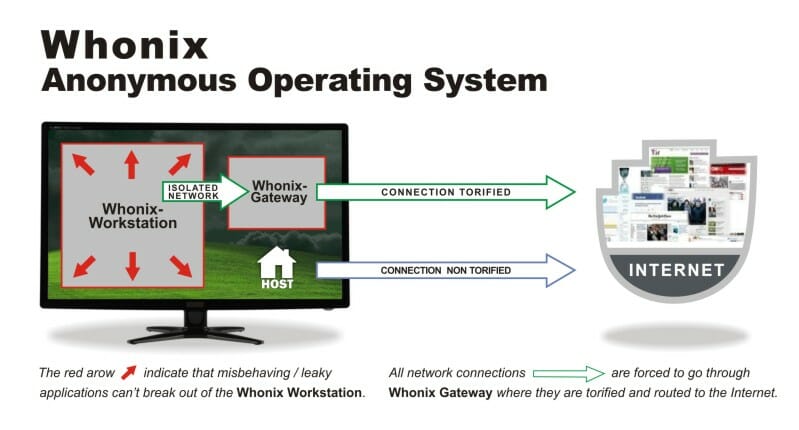
Whonix is an operating system designed for security and privacy, reducing the risk of any outside spies or attackers. The OS uses a Debian base and Tor’s free software that provides an open relay network. This protects users from network surveillance while allowing full use of the system like any other OS. One of Whonix’s claims to fame is its protection against malware and DNS leaks, which are made nearly impossible, so user’s ID address remains anonymous.
Whonix consists of two virtual machines inside the Debian base called a “Workstation” and a Tor “Gateway.” All network connections are forced to go through the Workstation that filters through Tor, then they are routed to the Internet. Applications can’t leave the Workstation either.
Both virtual machines install images on a user-provided host operating system, and compatible engines are VirtualBox, Qubes OS and Linux KVM.
The Whonix system also features Tor Browser, instant messengers like Tor Messenger, Tox, and Ricochet, encrypted email, secure data transfer, and web server administration with Apache and a host of other software programs. Unlike Tails, Whonix isn’t an “amnesic” live system. This allows both virtual machines to maintain their past state no matter how many times the system experiences a reboot, and improves security to ward away any malicious traps.
Editor’s note: This article is regularly updated for relevance.
