Two devastating malware affecting Android devices surfaced this week, raising serious concerns about the security of Google’s mobile operating system. On Tuesday, Kaspersky Labs exposed “Skygofree,” a spyware bundle capable of performing 48 different remote functions and affecting users in Italy. A few days later, Tokyo-based cybersecurity firm Trend Micro described a separate and unrelated malware, “GhostTeam,” that is present in Google Play apps and specifically targets people’s Facebook accounts.
“Android is a hot target due to the open architecture of the platform, which is both a blessing and a curse,” Jon Clay, Trend Micro’s director of threat communications, told the Daily Dot. “It’s great that Android users can select from a broad set of vendors for their mobile devices and have access to installing apps from anywhere, but this also gives threat actors a means to distribute malicious apps very easily.”
While these attacks were made for different purposes, they both compromise Android devices in order to steal private information from users. Here’s a more detailed look at Skygofree and GhostTeam with best practices for protecting your smartphone.
Skygofree
Described by Kaspersky as “one of the most powerful” spyware tools ever seen on Android, Skygofree lets hackers take over a device using a range of remote capabilities. It first appeared in the wild in 2015 but has been in development since 2014, continuously building on itself to become the powerful malware it is today.
“As a result of the long-term development process, there are multiple, exceptional capabilities,” Kaspersky researchers wrote in a blog post.
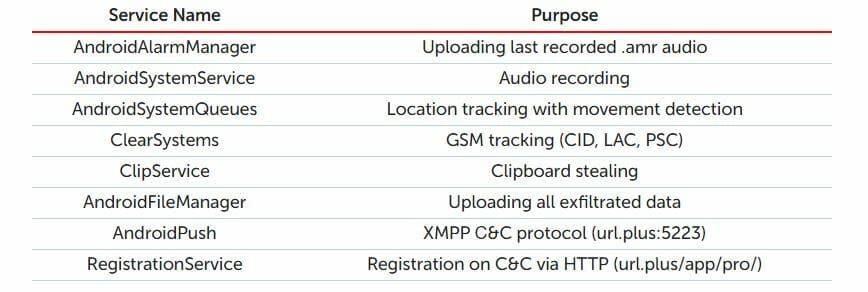
A few frightening abilities it enables include remotely capturing photos and videos, connecting to an infected Wi-Fi network, and stealing personal information from remote devices, like call records, text messages, geolocation, surrounding audio, calendar events, and other memory information. It can also trigger a smartphone’s microphone to start recording once it reaches a specific geolocation.
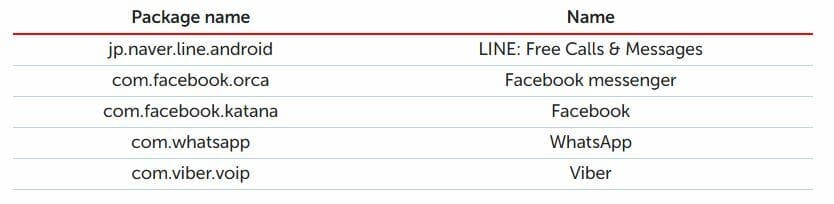
Android users’ social media accounts aren’t safe, either. Skygofree can monitor popular apps like Facebook Messenger, Line, Viber, and WhatsApp, stealing messages, even those that are encrypted.
The tool is “spread through web pages mimicking leading mobile network operators,” where it appears as an update that promises increased speeds. Victims fooled by those tempting claims will start to download the malware and its heavy payload. So far, only Android users in Italy have been infected.
Skygofree is in the same league as Pegasus, a malware discovered in August 2016 that put all the information on Apple iOS devices at risk. That spyware was developed by Israeli cyberarms dealer NSO to target a human rights activist in the United Arab Emirates and a reporter from Mexico. Apple quickly patched the bug in a software update.
Kaspersky is “pretty sure” Skygofree was created by an Italian IT company that creates offensive intrusion and surveillance software for governments and law enforcement agencies. It did not name a specific entity but said it was likely sold by a company similar to “HackingTeam,” which was hacked in 2015 and had its emails exposed in a massive leak.
To protect yourself from Skygofree, only download apps from trusted developers. That can be a tricky task, but there are some best practices you can follow to keep hackers away. First, look at reviews to ensure the app hasn’t caused problems for other users. Also, look at the name of the publisher and make sure it’s legitimate. Many apps that pass through Google’s verification process disguise themselves as other, more popular apps. And, of course, always be suspicious of random pop-ups and unfamiliar links.
GhostTeam
Another bug—unrelated to Skygofree—can take control of your social media accounts, specifically Facebook. GhostTeam was injected into 53 different Play Store apps that passed through Google’s verification process. Its goal is to steal your Facebook login credentials and overload your Android phone with pop-up ads.
It could potentially have been downloaded by hundreds of thousands of unknowing Android users. One of the apps was downloaded at least 100,000 times. Once the malware determines its host is a normal Android device (not one running an emulator), it drops a payload disguised as a Google Play service. The bad actors then gain full control over the victim’s Facebook account and start spamming them with full-screen pop-up ads, generating revenue along the way. The process is similar to the banking malware discovered on Android phones late last year.
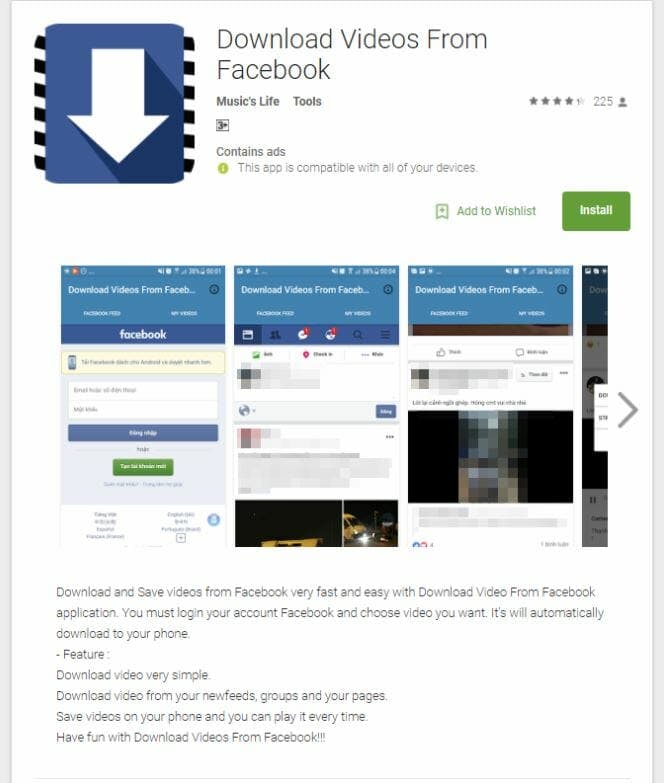
The GhostTeam malware first made its way to the Google Play Store on April 2017 and primarily affected users in India, Indonesia, and Brasil, the three countries with the most Facebook users, excluding the U.S. There’s no reason to believe the malware won’t make its way to the U.S. or Europe. Facebook is aware of GhostTeam and is doing its part to protect users.
“We are blocking the distribution of these apps where we can and we have systems to help detect compromised accounts and credentials,” a Facebook spokesperson told ZDNet.

While there have been no reports of “active cybercriminal campaigns” using the malware, Trend Micro believes it could exploit devices to mine cryptocurrency or spread fake news. It also thinks the attack was created in Vietnam because of “considerable use” of Vietnamese language in the code.
TrendMicro notified Google, and all known malware-infected apps have been removed from the Play Store. Of course, there could still be more apps floating around, so take the same precautions discussed with Skygofree: Look at app reviews before downloading them, and always keep your phone up-to-date.
“Google is doing what they can and trying hard to vet the apps that are being added to the Play store, but threat actors are crafty and find ways around most safeguards,” said Clay, Trend Micro’s director of threat communications. “Our recommendation is still to use the official Google Play Store when obtaining new apps versus installing apps from untrusted sources as well as installing a robust security app that can help block the installation of malicious apps.”


