A leaky database has exposed the physical security of multiple Oklahoma Department of Public Safety facilities and at least one Oklahoma bank.
The vulnerability—which has reportedly been fixed—was revealed on Tuesday by Chris Vickery, a MacKeeper security researcher who this year has revealed numerous data breaches affecting millions of Americans.
The misconfigured database, which was managed by a company called Automation Integrated, was exposed for at least a week, according to Vickery, who said he spoke to the company’s vice president on Saturday. Reached on Tuesday, however, an Automation Integrated employee said “no one” in the office was aware of the problem.
“They said that they were going to let their clients know,” Vickery said.
The Daily Dot reached out to Oklahoma’s statewide law enforcement agency, the Oklahoma Highway Patrol, to give notice of the breach, which specifically affected the building housing Troop A. An official became hostile with the reporter during the call, responding with disbelief and insisting that the reporter did not know what he was talking about.
MidFirst Bank of Oklahoma City was also affected, Vickery found. “I was even able to get images from within the bank’s safe deposit box vault,” Vickery said. An official at the bank said it would respond to a press inquiry shortly.
Vickery said by phone on Tuesday that he discovered the leaky database one day before the Dallas police shooting, which claimed the lives of five officers. He was initially concerned about going public with a vulnerability affecting law enforcement. “I was very cautious at first about it,” he said, “but I decided the risk of doing harm with the information I was putting out there wasn’t that great.”
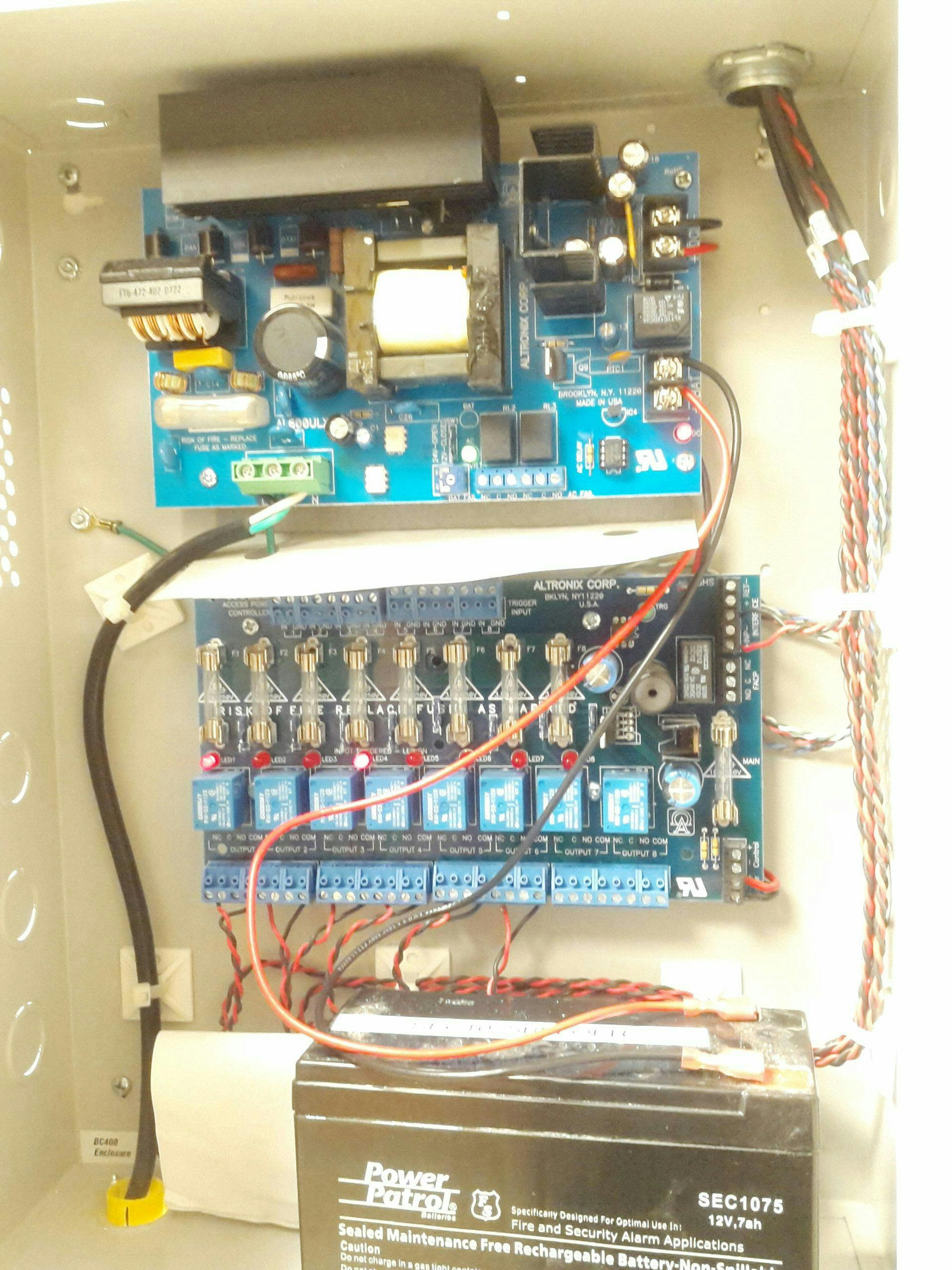
Vickery provided images contained in the database, which he said could be previously accessed without a username or password. The photos show various doors, locks, RFID access panels, and the controller board of an alarm system, which is a device typically masked for security purposes. The database additionally contained “details on the make, model, location, warranty coverage, and even whether or not the unit was still functional,” Vickery said.
“This is an example of excellent incident response,” Vickery said of the Automation Integrated whom he alerted of the breach. “The guy didn’t try to call me a hacker, he didn’t try to claim that it was a fake database filled with dummy-data, and he didn’t try to deflect responsibility onto another company. What he did do was fix the issue promptly, verify with the original reporter that the issue was fixed, and he appreciated the fact that someone would go out of their way to make sure an issue like this was taken care of.”
Vickery added that Automated Integration is far from the only company whose database are left exposed online. “I have a constantly fluctuating list of 50 to 100 similar breaches that need to be reported,” he said. “This one just happened to involve a security-related company and government buildings, so it got bumped to the top of my list.”