A breast pump manufacturer is storing millions of documents on an exposed server that includes the names, email addresses, and phone numbers of doctors across the U.S.
The California-based medical company, which the Daily Dot is declining to name, offers numerous models of breast pumps as well as referrals for customers seeking personal support from “trusted experts” in the field of breastfeeding.
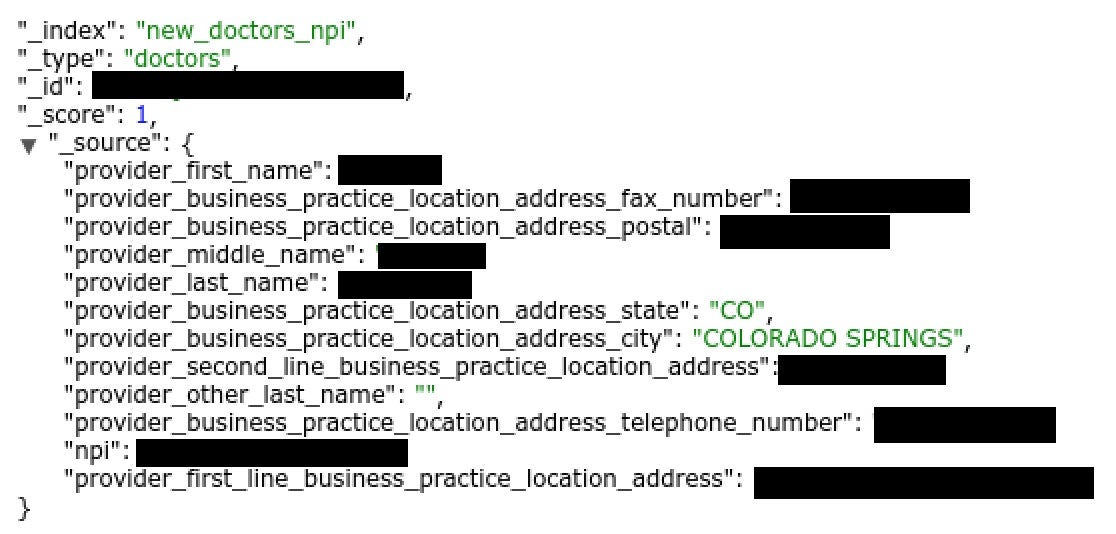
The server, discovered by Anurag Sen, a cloud security researcher with CloudDefense.AI, is run by Amazon’s cloud computing service and contains approximately 7,151,537 documents in total.
The documents, divided between two separate databases, hold the full names, business addresses, fax numbers, and phone numbers of those in the medical profession. National Provider Identifier (NPI) numbers, unique 10-digit identifiers issued to healthcare providers in the U.S., are also present.
In remarks to the Daily Dot, Sen stated that he came across the exposed server while using his company’s internal tools for monitoring data leaks. The security issue, Sen added, appears to have been caused by a configuration error that left the server exposed without password protection.
While much of the information could be found publicly, it remains unlikely that those listed are aware that their information is centrally available in a database of that size. A timestamp on one of the listings notes that it was made in July 2020.
The Daily Dot reached out to a number on the list purported to belong to a doctor in Florida and confirmed it to be accurate. After informing a secretary of the reason behind the call, the Daily Dot was swiftly hung up on.
Sen says that although he reached out to the company on March 11 to inform them of the security lapse, the company did not respond. The Daily Dot reached out over a contact form on its website and at a customer service email last week but did not receive a reply either.
The Daily Dot is declining to name the company, as the data is still available as of publication.
After reaching a customer service representative over the phone, the Daily Dot was told to once again send an email to the company that would then be forwarded to the appropriate party. After being given a full week to respond, no contact was ever made.
The pseudonymous blogger Dissent Doe, a licensed healthcare professional who chronicles such data exposures on DataBreaches.net, speculated to the Daily Dot that the data could either be a customer list or marketing list.
The blogger also noted that while the exposure is unlikely to cause any significant harm, the company could potentially “lose any competitive advantage if their contact list was acquired by competitors.”
“As far as misuse of the data, I’ve learned not to underestimate what creative criminals can do with information, so the fact that I wouldn’t see anything particularly evil other than spamming doesn’t
mean that clever criminals can’t figure out a way to misuse it,” they said.
While the exposure of the data may not be inherently dangerous, the failure to implement basic security measures by a healthcare company marketed toward women is troubling. Companies that handle data relating to women’s healthcare and pregnancy have come under increased scrutiny over the past year, following the overturning of Roe v. Wade, as fears grow that states that are outlawing abortion could use sensitive data to help prosecute abortion seekers.

