Hackers exploited a previously undisclosed security flaw in Microsoft’s Windows operating system to spy on the North Atlantic Treaty Organization (NATO), Ukrainian officials, and European telecommunication firms, according to U.S. cybersecurity firm iSIGHT.
A security report released by iSIGHT on Tuesday claimed that a team of Russian hackers—dubbed “Sandstorm” due to their frequent use of Dune references—is responsible for a cyberespionage campaign employing multiple exploit methods, including this newly reported Windows zero-day vulnerability.
The Sandstorm hackers rely on techniques like social engineering and email phishing to be effective, iSIGHT said. Operating systems vulnerable to their attacks include Windows 7, Windows 8, and Windows RT.
“The vulnerability exists because Windows allows the OLE packager (packager .dll) to download and execute INF files,” iSIGHT’s reports. “In the case of the observed exploit, specifically when handling Microsoft PowerPoint files, the packagers allows a Package OLE object to reference arbitrary external files, such as INF files, from untrusted sources.”
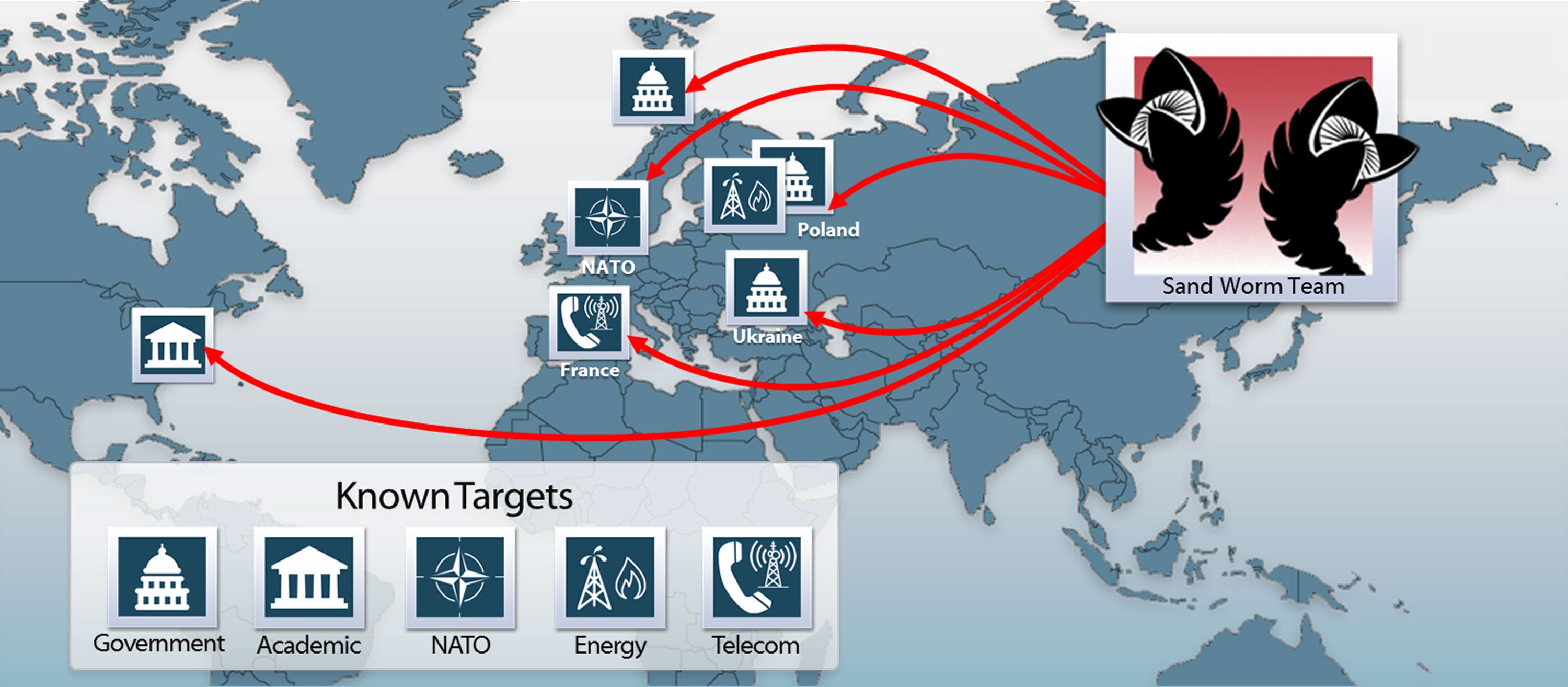
Image by iSIGHT
For more than a month, iSIGHT and Microsoft coordinated to track the use of the exploit “in the wild” and develop a patch to protect against it. The two companies elected to withhold the vulnerability until the patch was finished to prevent other criminal hackers from taking advantage of the security flaw. “Should we have witnessed a major change, both Microsoft and iSIGHT Partners were ready to release this information in advance of the patch,” iSIGHT said.
According to the researchers, use of the Windows exploit increased as fighting intensified in Eastern Ukraine. Multiple organizations in Ukraine were attacked along with the NATO alliance and an unnamed Polish energy firm. A French telecommunications firm was also targeted by the same group, iSIGHT said, using a malicious program called Black Energy, which has been used in the past to launch denial of service (DDoS) attacks and steal sensitive financial information.
“Though we have not observed details on what data was exfiltrated in this campaign,” iSIGHT said, “the use of this zero-day vulnerability virtually guarantees that all of those entities targeted fell victim to some degree.”
Photo via Herr Olsen/Flickr (CC BY 2.0)
