A Muslim hacktivist group is using stolen Israeli credit cards to fund Palestinian charities, according to the group’s leader.
The group, known as AnonGhost, reportedly gained access to credit card credentials after hacking into dozens of Israeli websites. Mauritania Attacker, AnonGhost’s founder, told the Daily Dot that the group had paid out roughly $18,000 to an unspecified number of Palestinian charities using stolen cards on Tuesday.
“We hope that we will make Israel lose money and as much possible,” the hacker said.
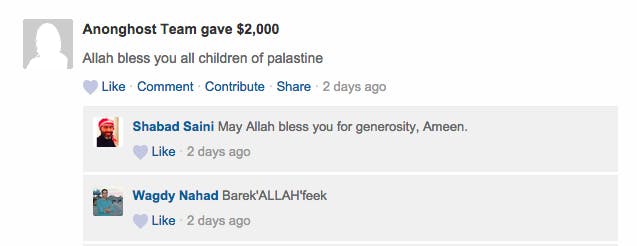
Evidence of the fraud was posted online by AnonGhost in the form of screenshots, which purportedly show thousands of dollars being transferred to “Keeping the Children of Gaza Alive,” an apparent Palestinian fundraising campaign that accepts donations on the website FundRazr.
Recent activity on the page confirms that separate payments of $2,000 and $200 were received within the last three days from a user named “Anonghost Team.”
We were unable to reach Shabad Saini, who launched the FundRazer campaign nearly two months ago. According to Mauritania Attacker, neither Saini nor any of the other recipients are aware of AnonGhost’s activities.
Funds donated to Saini’s campaign go to support Compassionate Hearts 4 Gaza, an organization that claims to be based in Rafah, a refugee camp located in the southern Gaza Strip, which “makes regular distributions of food, clothing, and medical supplies to the people of Gaza,” according to the campaign’s FundRazr page.
AnonGhost has been waging a cyberwar against Israel since 2008. In the past week alone, the group has infiltrated around 255 websites, the majority of which are Israeli, according to Zone-H, which maintains an archive of website defacements. According to Mauritania Attacker, not all of the websites are listed, and he places the figure closer to 10,000.
Some of the websites defaced by AnonGhost included photos of militants holding the Islamic State (ISIS) flag, also known as the “Black Standard.” Mauritania Attacker says the group is not officially associated with ISIS but that some of the members support them, including himself.
“ISIS doesn’t need us, whether we support them or not, because they already have big hackers,” he said.
The group’s members have been ordered by Mauritania Attacker to continue hacking Israeli websites until April 20. Facebook and email accounts are also being targeted.
The group’s activities have been associated with Anonymous in various news reports, including a Tuesday article by the New York Times. But according to Mauritania Attacker, his group is in no way affiliated with the loosely organized hacktivist collective.
“We were never associated with Anonymous. They’re a group of kids with masks that play with keyboards,” he said, adding that his group is much older.
Anonymous is, however, currently engaged in a long-term cybercampaign against Israel, which has entered its third year. The campaign was spurred in November 2012 by a violent eight-day conflict between the Israeli military and Hamas. Roughly 140 Gazans and five Israelis were killed as a result of the clash.
In response, Anonymous launched “Operation Israel,” or #OpIsrael, a hashtag also adopted by AnonGhost. This co-adoption, along with the group’s “anon”-branded name, likely contributes to the confusion over AnonGhost’s association with Anonymous.
As a result of Anonymous’s 2012 campaign, Israeli websites endured more than 60 million hacking attempts—a figure that likely refers to distributed denial-of-service (DDoS) attacks—according to then-Israeli Finance Minister Yuval Steinitz.
In a video released last month, Anonymous-affiliated hacktivists vowed to unleash an “electronic holocaust” on Israel.
“As we did many times, we will take down your servers, government websites, Israeli military websites, and Israeli institutions,” the group warned. The subsequent attacks, however, were widely reported by security analysts as the weakest so far in the long #OpIsrael campaign, with few government-related websites affected.
Anonymous’s targets, meanwhile, appear to have grown a bit wiser, downplaying the effectiveness of DDoS attacks and referring to website defacements as simple “cybergraffiti.”
Illustration by Fernando Alfonso III